Bigger or smaller ignoring any threat is not advisable in today's highly challenging time. Clickjacking has never been considered a big threat by most businesses over time.
Researchers have found that not every organisation considers clickjacking a severe security threat. But it can harm businesses. In many instances unknowingly the employee who clicks on the false link can open a chain of vulnerabilities for the organisation. Major industry giants like Twitter, yelp, WordPress, Shopify and many others have often paid bug bounties for locating this vulnerability.
What is Clickjacking?
Clickjacking is a cyber attacking method exploited by the threat actors to deceive the users into clicking on the fake link assuming that as the real one. Once they click on it, they will be routed to a different website, downloading a fraudulent app, exposing confidential data, or any other spamming activity. This may give the threat actors the opportunity of stealing the information or even take control of the victim's computer.
Also, known as a UI redress attack, may not be the end goal of the attack, it is simply a means of initiating some other by fooling the user, from installing credential-stealing malware to innocuous things like boosting clicks and traffic to unrelated sites, boosting ad revenues on the sites, gaining social media likes etc.
If the website is vulnerable to clickjacking, the attacker can easily disable cross-site request forgery (CSRF) token protection. This will lead to trick the browser into doing things without the user's knowledge and permission.
ClickJacking Examples
1. Malware Download - The threat actor can initiate the download of malware when the user clicks on the fake link. This can corrupt the system and may act as spyware or as a gateway for advanced attacks.
2. Cursorjacking - A duplicate cursor is created and attached to the real one at a specified offset. only the duplicate cursor will be visible. The hacker will smartly offset the real cursor to the specific area for clicks, whenever the fake cursor is manoeuvred to that area.
3. Money Transfer Scam - The user can be tricked into clicking on the link on a malicious page authorizing the transfer of money from the bank account.
4. Webcam and microphone activation - The hacker can invisibly load the flash settings over another link. When the user will click the infected link, the flash plug-in settings will be modified to give a hacker access to the webcam and microphone.
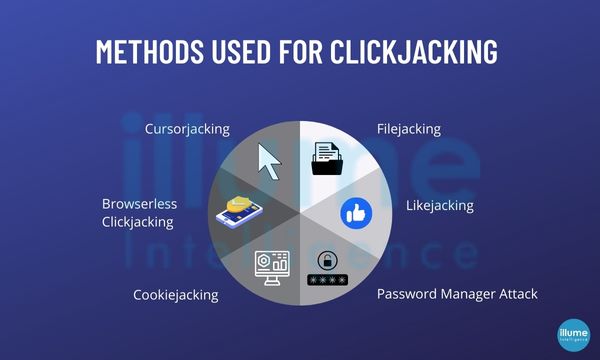
Types of Clickjacking
There may be multiple methods used by hackers for implementing clickjacking attacks. Some of these are -
1. Cursorjacking - This is a method for manipulating the cursor on the computer screen. It shifts to a different location. This is commonly used to attack Adobe Flash and Firefox flaws.
2. Browserless clickjacking - This is used to implement clickjacking in programs that do not run on browsers. These are common on smartphones.
3. Cookiejacking - The user is made to interact with a UI element through drag or drop, providing the attacker with the stored cookies on their browsers. This allows the attacker to perform actions on the target website.
4. Filejacking - with this the hacker can access the local file system and takes the user's files.
5. Likejacking - This captures the users' clicks and redirects them to likes on social media networks.
6. Password manager attack - This can easily deceive the password managers to take advantage of their auto-fill functionality.
How to effectively prevent Clickjacking?
The organisation comprises all sorts of employees having technical and non-technical knowledge. Unknowingly any user may allow some intrusion of some or the other form hence it is important to take preventive measures. These are generally done from both the server and client sides.
A. Server Side
1. Content Security Policy -
Using Content Security policy and its frame-ancestors directive can help in defending against clickjacking. It controls how the page can be embedded by different sites by specifying the main pages that may embed the page. It may be deployed directly as a response header. The frame-ancestors directive is just one of the many directives that can be used.
2. X-Frames Options -
X-frame Option may be used directly as an HTTP header. It is currently supported by all major browsers but not wholly. Also, the X-frame Option is very limited and hence may introduce difficulties for the website designers.
B. User Side
1. Frame busting - It is a client-side technique. It is a most generic method and can be easily circumvented by hackers in several ways hence not advisable by many experts.
2. Install browser extensions -
These browser extensions don't provide the best user experience as they disable all the javascript on loaded websites hence impeding the functionalities of many websites.
How to know if your website is safe from Clickjacking?
A basic way to confirm if your website is vulnerable to clickjacking or not is to create an HTML page and attempt to include a sensitive page from the website in an iframe. One can use the OWASP Testing guide for further support on this.
Once the test is conducted and the website is vulnerable it is important to secure it. If the website is not vulnerable then further testing is needed to find out the methods employed as they may be bypassed by the threat actors.
How Illume Intelligence can help?
The experts from Illume Intelligence India Pvt Ltd, Kerala, India, can test the vulnerability of your website and all the web assets to help in preventing clickjacking and other vulnerabilities on time. We also test your resources thoroughly for sending the proper X-Frame Options HTTP headers, for preventing some parts of the websites from being exploited on other pages or outside the organisation's domain.
With our services, you can regularly test and audit your entire cyber security and stay safe from the nightmares of increasing online threats.



