Finding flaws in the security regularly like a hacker using Cyberattack Simulation
With the increasing cyber attacks, it has always been a worry for professionals to provide 360-degree protection. Cyber attacks are becoming advanced and audacious day by day leading to financial threats, writing malicious code and lodging political protests. The impact of cyber attacks is unimaginable as the intruder can misuse the system or the stolen data the way they want.
Understanding the loopholes present in the security from a hacker’s perspective can only help the technical team to remove them. Knowing the real threat's an organisation faces, will help in preparing against sophisticated cyber attacks. Illume can enlighten you on this. A cyber-attack simulation exercise is capable of exposing known and unknown vulnerabilities by testing against real-world threats.
Utilizing our customized, tested and proven methodologies to identify shortcomings in physical security, personnel and procedural security and system and application-level security.
What is cyberattack simulation?
Cyberattack simulation is software used to mimic real-world security threats to find vulnerabilities in the security system of a business and prepare incident response plans. These simulated attacks may send fake phishing attacks to employees or may attack the organisation's web application firewall. It may use automated simulations for continuous testing using AI-based threat logic to ensure the team is always on guard.
These simulations are designed as per the client's requirements. These are available all the time but can be used periodically as per the requirements. No matter whether a manual method is used, it is hard to assess the efficacy of security operations. Our customized software can simulate various threats over various environments to help our clients prepare and evaluate their security. The cyberattack simulation exercise includes phishing, malware compiling and binding, SQL injection, DDOS and other exploits that generate deeper insights for the CISO/CFO/CEO, to strengthen the security of the organisation.
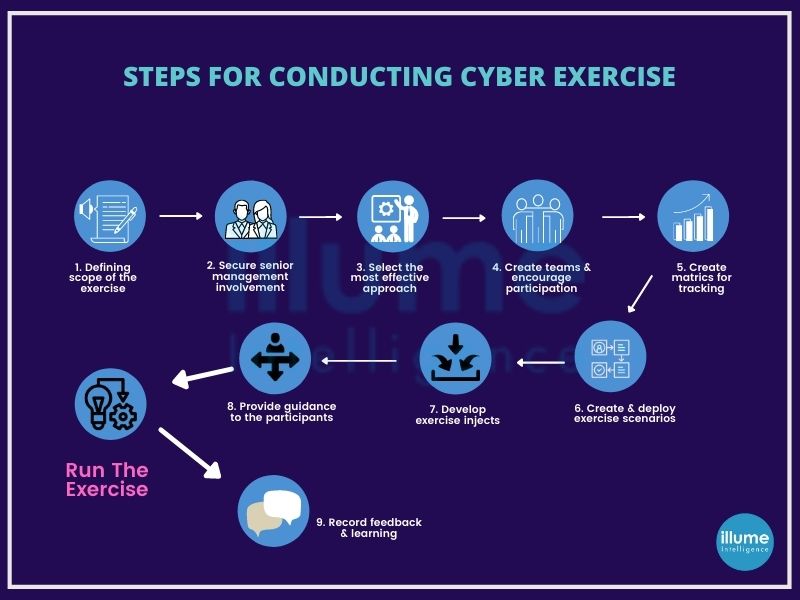
How do we conduct cyberattack simulations?
Thinking like threat actors to identify the exploitable options. We employ the information available on open sources, to understand the hacker's view. Going beyond the traditional penetration testing to understand the importance of the tactics, assets, locations and other factors for a hacker. This helps in easily identifying the security gaps in the organisation's arrangement for protecting the most valued assets. We look at every possible attack surface as anything can be exploited by hackers.
How about understanding your threat position? Let's arrange a confidential cyberattack simulation now.







