Ensuring the safety of your network against the threats, that may originate from IoT devices
The Internet of Things includes all the electrical devices, vehicles, and security devices that can connect to the internet for taking commands to operate. These devices are often made by different vendors using different techniques and methods. Ignoring their vulnerabilities can lead to severe havoc on your security.
IoT penetration testing is security testing used to test the insecurities posed by connecting IoT devices to the organisation’s network. It means conducting vulnerability assessment and penetration testing of all the IoT devices on the network. This ensures all the security flaws are identified and resolved. The connected devices are contributing to the growth of business and hence are being frequently targeted by the threat actors.
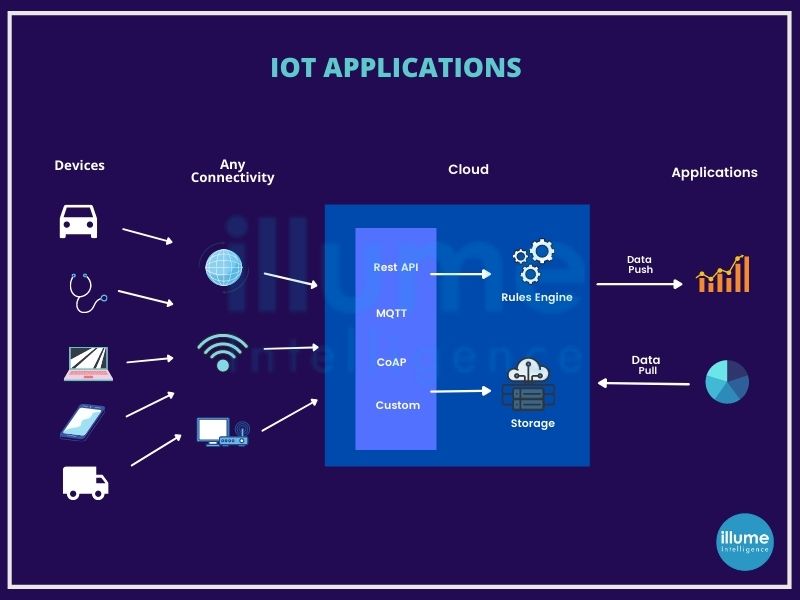
How can IOT penetration testing help?
The Center for Internet Security (CIS), recommends best practices for securing IT systems and data. Large organisations need to implement organizational CIS controls.
1. IoT devices have multiple interfaces making them vulnerable. Penetration testing can help in securing the input methods.
2. Network infrastructure interconnecting to these devices is at the risk of exploitation. Automated tools and manual penetration testing methods should be utilised to secure network infrastructure and protocols.
3. Scanning proprietary programs are important to secure the entire system architecture.
How do we perform IoT penetration testing?
Our team of experts helps you in strategically building and implementing an IoT ecosystem safe from threat actors. We use the most progressive penetration testing techniques to identify, evaluate and analyze vulnerabilities across the network ensuring the regulations and compliances.
We follow the below testing methodologies-
1. OWASP Testing Guide
2. NIST SP 800-115 Technical Guide to Information Security Testing and Assessment
3. PCI DSS Information Supplement
4. FedRAMP Penetration Test Guidance
5. ISACA's How to Audit GDPR
Every organisation needs to build a comprehensive security defence strategy with governance by regulations and compliances. With the help of penetration testing, the business can get a deep insight into the risks and vulnerabilities to implement the best-suited defence system.
How safe is your network with the IoT devices connected? We can help in securing your network as an IOT penetration testing and strategising partner leading to business growth.







