Govern your Security Policies easily with the Security Operations Center
Expanding the Internet has given global access to business but it has also come with security problems as well. Cybersecurity breaches are no longer restricted to big organisations, they are happening everywhere. Irrespective of the organisation's size or type, it is essential for all to ensure a defence system. According to a survey around 77% of companies have increased their cybersecurity Budget.
Many organisations find it difficult to achieve complete threat visibility lacking siloed security log management, costly and ever-expanding infrastructure changes and the non-availability of specialised staff. It is a time to work on advanced security events and infrastructure management. It is important to rethink the security designs for implementing the right security policy and security incident detection.
What is Security Operations Center (SOC)?
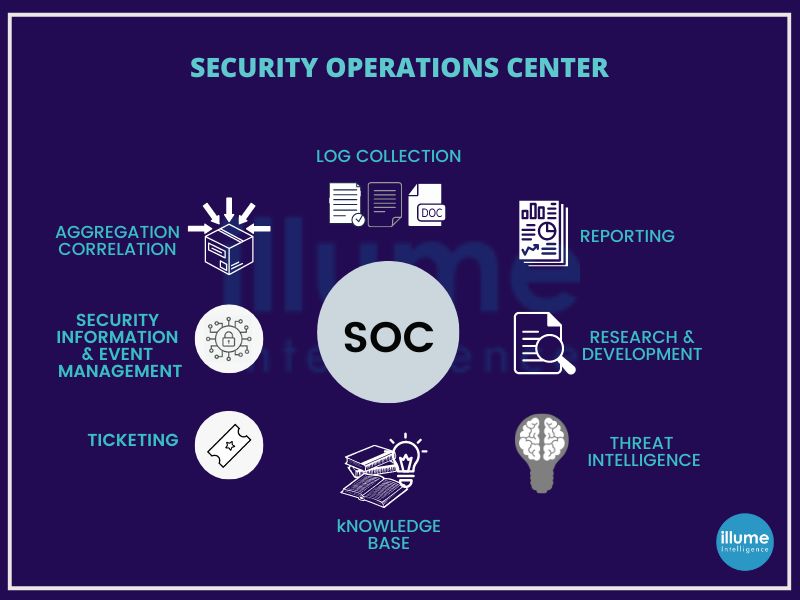
A Security Operations Center (SOC) is an in-house or outsourced team of IT Security Professionals for monitoring the organisation's entire IT infrastructure. This team works 24*7 for real-time detection of cybersecurity events to address them quickly and effectively.
The SOC team works closely with the incident response team to ensure quick addressing of the issues as and when detected. Security operations centres monitor and analyse network activities, servers, databases, devices and other connected systems for anonymous activities. SOC helps in operating and maintaining the cybersecurity of the organisation by continuous threat detection and data analysis for finding ways to strengthen the organisation's security posture.
The major benefit of SOC is that it ensures the identification, analysis, defence, investigation and reporting of all potential security incidents. To begin with, it is important to have a strong strategy, followed by the implementation of required infrastructural support like firewalls, IPS/IDS, breach detection solutions, probes, security information, event management (SIEM) systems etc.
How Security Operations Center (SOC) works
1. Recording - Making a record of available resources for preparation under the scope of the organisation's infrastructure.
2. Preparation and preventative maintenance - Preparation and preventative maintenance by regularly updating the existing systems, updating the firewall policies, patching vulnerabilities and whitelisting, blacklisting and securing applications.
3. Monitoring - Continuous proactive monitoring for detecting abnormalities or suspicious activities.
4. Alert handling - Alert ranking and management for prioritising the issues and their handling.
5. Early detection and defensive action - Quick response to the detected threats by performing actions like isolating endpoints, and terminating the harmful process.
6. Restoring - Restoring and recovering the compromised systems and data, including wiping and restarting endpoints, reconfiguring systems or, in the case of ransomware attacks, deploying viable backups in order to circumvent the ransomware.
7. Log management - Log Maintaining includes collecting, maintaining, and regularly reviewing the log of all network activity and communications for the entire organization.
8. Investigating - Investigating the root cause to figure out what and how it happened.
9. Futuristive approach - Security refinement and improvement on the basis of the findings to protect the future mishaps
10. Compliance ready - Getting the system always ready for compliance-ready by providing all the audits and other reports.
Illume Intelligence's SOC as a Service empowers your organisation by providing complete visibility within the infrastructure. Identifying hidden risks and implementing the security strategy so that you focus on your business. A complete record of the important security logs for helping in building a compliance-ready secure environment trusted by the employees and the clients







