Auditing to remove unwanted policies and hardening servers as per CIS Benchmarks
Protecting systems and data is crucial for every organisation to ensure security from cyber attacks. System hardening or Server hardening is a process of securing a system’s configurations and settings to reduce IT vulnerability. It is done to minimize exposure to threats and mitigate possible risks.
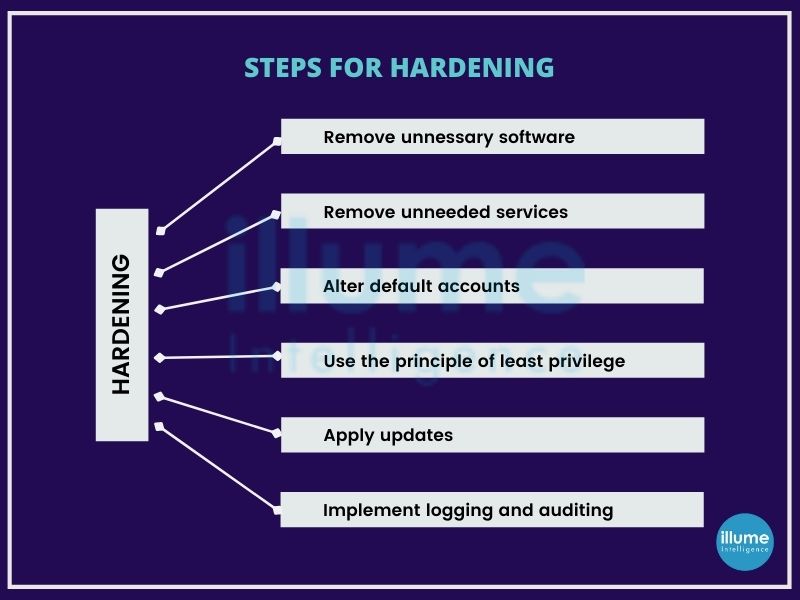
The operating systems are designed to provide convenience and ease of use over security. The IT security team may have a different opinion on this. But they don't have to worry as there are steps that can be taken to harden a system and eliminate as many security risks as possible. For example, the basic one is to change the vendor's default username and password. Default access codes can be easily hacked as they are available on open sources. The other examples include removing unnecessary services from the configuration settings, applying firewall rules, enforcing password complexity, system idle time outs and more.
Securing systems is crucial for IT infrastructure. Every organisation has one or multiple servers connected to the internet. Business continuity and credibility depend on the security of data stored in these devices.
We have a qualified team to support the clients' infrastructure management needs. Implementing hardening measures at multiple levels is required for ensuring reliability and uptime for the business. Some of the standard practices that we follow are -
1. Physically securing the server facility.
2. Separating the database server from the application server.
3. Hardening of webserver and application servers.
4. Security audits using tools.
5. Enforcing IP-based restrictions.
6. Implementing server password policy.
7. Limiting access.
8. Isolating production environment.
9. SSH hardening
10. Monitoring and maintaining infrastructure.
Why is Server Hardening important?
When talking about server hardening it is not only required for security but compliance as well.
Server hardening is an important factor in protective technologies like Firewalls and EDRs. If the server is not hardened properly no amount of money spent can secure the server.
All the major compliance frameworks have server hardening as mandated. All compliance frameworks consider CIS Benchmarks as the best practice. Hence when looking for compliance this becomes essential.
If you haven’t yet established the system hardening routine for your organisation, it is a good time to start now. We can help in building your policy according to the CIS Benchmarks, followed by implementation and maintenance.







