Organisations that can automate more than 70% of their network changes can reduce the number of outages by at least 50% and deliver services up to 50% faster - Gartner
Manually changing the security policy is complex and error-prone leading to business slow down. Reworking to rectify the policy may lead to compliance violations. It includes multiple teams and multiple devices making it furthermore complicated.
The network is a lifeline of any organisation and making it work flawlessly takes a lot more than establishing and setting the things once. That's why many businesses are looking up to automation as a solution for regularly maintaining the security.
Challenges to Automation
In spite of knowing that manual policy changes impact the productivity of the organisation they are not ready to take the steps towards automation because of the wrong perception of security. The production environment in every organisation is maintained by multiple teams like DevOps, maintenance, IT, Cloud security, and so on. Different teams have different levels of security understanding and hence it is challenging to bring them all on a common platform.
The threat to the business is not a determined hacker finding elaborate ways through defences. Networks get exposed due to accidental firewall and cloud security group misconfigurations. Manual rule and policy management of complex ground-to-cloud networks introduce countless opportunities for error and most breaches, giving advantages to the hacker to sneak in.
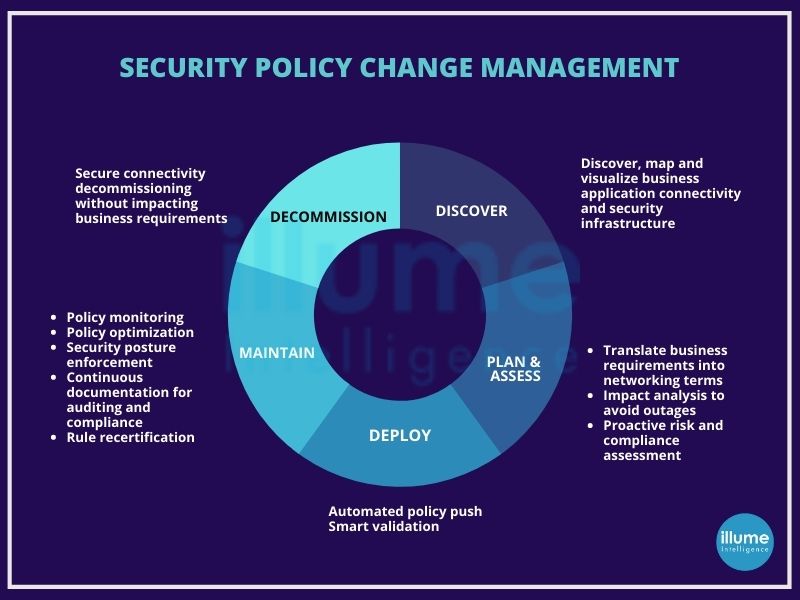
How does the Security Policy Change Management process work?
The process of Security Policy Change Management typically involves the following steps:
1. Identification of the change request - A change request is submitted, detailing the proposed security policy modification.
2. Review and approval - The change is reviewed by relevant stakeholders, and approval is obtained.
3. Testing and validation - The change is tested in a controlled environment to ensure it works as expected and doesn't cause any issues.
4. Implementation - The change is deployed following a pre-defined plan, and a rollback plan is prepared in case of any issues.
5. Post-change evaluation - The effects of the change are monitored to ensure everything is functioning correctly.
What to focus on for Security Policy Change Management?
With the quick-rising threat, all the industries are under pressure to implement security for safeguarding their business and in a hurry they may trip on some common problems such as under -
1. Focusing on less important tasks - Documentation is often confusing and makes teams focus on less important things and waste more time on things that just need to be mentioned rather than things that hold more importance in understanding the dependencies and support to the business.
2. Not removing firewall rules for decommissioned applications - old and decommissioned network components and firewall rules may clutter the network and make the performance bad and it must be revised from time to time.
3. Miscommunications among different teams - Maintaining a large IT infrastructure requires multiple teams. These teams always have problems understanding each other's work and communications making it a lengthy and difficult process to implement changes.
4. No proper documentation - proper documentation is a must as it helps in keeping everyone updated on the changes made in the past. What happened and what was done to rectify it, why any rule was applied and what is linked to it? Without the proper documentation, it will be hard to perform the audit.
5. Human errors - there is a huge scope of errors when editing the rules manually. Even the slightest looking mistype of port number can lead to a big problem for the entire network making it vulnerable.







