Network Segmentation can protect you against ransomwares and malwares
Network segmentation (Network Partitioning or Network Isolation) is used to improve network security but it is not an easy task. Generally, networks are designed to be tough on the outside and simple inside. Organisations following regulations install a mature firewall perimeter and some sort of Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) to monitor the incoming traffic.
However, if someone manages to sneak in through that traffic will have a smooth network structure that can be exploited as required. Most of the tools are designed to perform specific functions and will ignore the movement outside of their programming. Gives the advantage to the hidden malicious programs to act free and launch an attack or simply stay quiet and leak the information. This kind of flat network infrastructure is easy to maintain but is a great opportunity for the threat actors to breach the main security and get access to the entire infrastructure.
What is Network Segmentation?
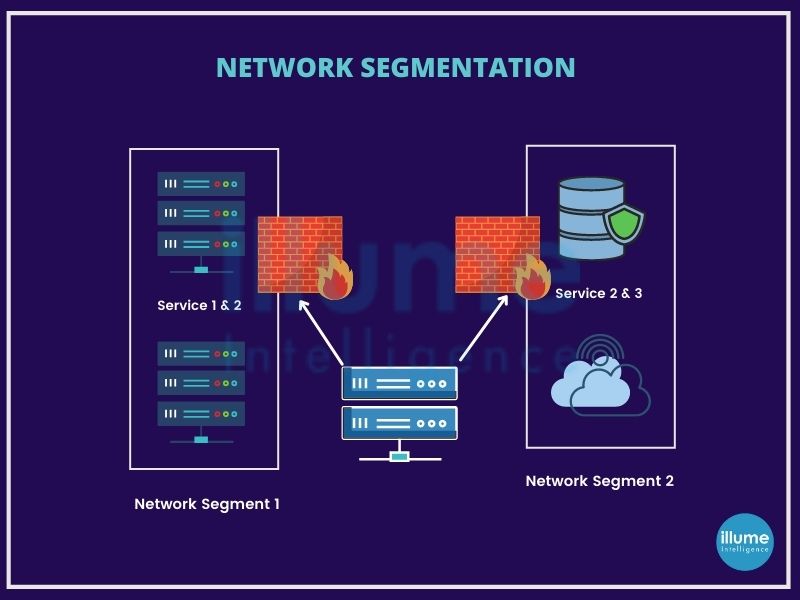
Segmenting the computer network is splitting the network infrastructure into smaller network segments. All servers and workstations are not required to communicate with each other but keeping them on a common network allows the threat actors for exploiting them.
Segmentation can be done physically or virtually. The main idea is to limit the communication between the devices and hence reduce the attack surface area.
Who Needs Network Segmentation?
Every organisation running multiple internal systems for meeting its business needs must have network security. The more complicated the architecture is, the more important the need for segmentation. Businesses relying 100% on SaaS solutions or business that works completely offline will not need network segmentation.
Businesses running on flat networks will be ideal targets for hackers. A flat network may seem easy saving time and money for installation may lead to bigger disasters later. There is no substitute for network segmentation.
The Benefits of Network Segmentation
Network segmentation offers absolute and efficient security among all the information security methods. Following are some of the benefits an organisation will avail from applying network segmentation -
1. Data Security - More segments will lead to more blocks and will stop the hackers from exploiting the network and stealing the data.
2. Threat Reduction - In case of the attacks the bad actors will have the access to the limited network and hence will take some time for them to get details and insights for full structure hence giving alerts and time to the administrators to take preventive actions.
3. Controlled Access - Network segmentation helps in protecting against insider threats. Limiting access to different critical networks and allowing only a limited number of people helps in restricting the way attackers gain access to systems.
4. Enhanced Threat Detection and Tracking - Segmentation allows easy monitoring. Increasing the number of checks makes it easier to detect suspicious behaviour. This also helps in determining the source and context of a problem.
5. Rapid Response Times - Quick response from the IT team is reacting to remote operations because of different routers. The threat can be easily tracked leading to quick detection of impacted sections.
6. Damage Management - Segmentation keeps the damage caused limited to the particular section, keeping the others safe.
7. Safeguard Endpoint devices - The unwanted activities are maintained away from the unsecured devices due to repeated load balancing. This is gaining importance due to the increasing use of IoT devices.
Network segmentation helps in reducing the threat landscape, controlling traffic and detecting crucial infringements. It is a recommended framework based on the patterns the hackers are using to exploit the organisation's network for creating a big impact to harm the organisation and the associated businesses.







