Securing the nation by securing critical information infrastructure
Industrial Control Systems, specifically the old configurations, are often deployed as isolated installations to work in standalone environments without any connection to the external network including the internet.
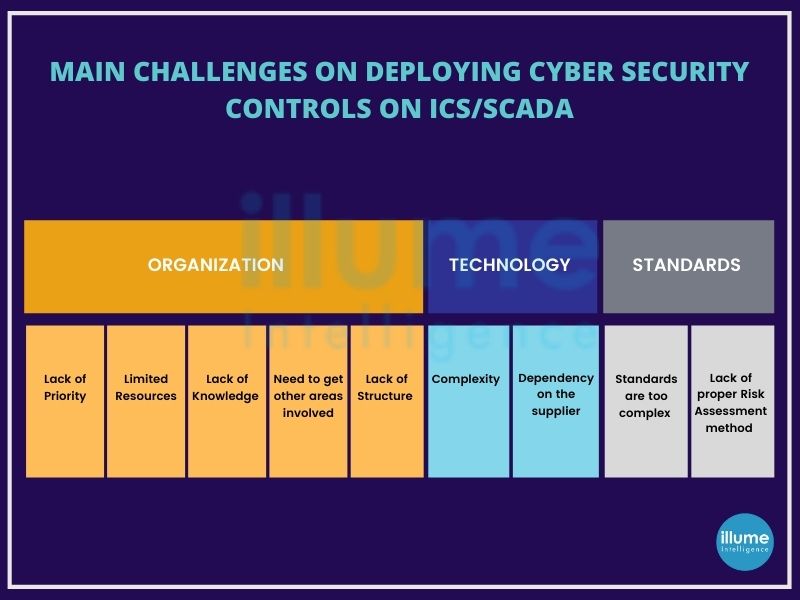
ICS-embedded architectures are different from other systems. Older ICS were designed on the assumptions to connect in a small internal network. The span of the internet has changed the complete picture. ICS even working on internal networks are exposed to security threats. The ICS may be running on a separate network, but physical isolation is becoming the exception. Even without direct contacts, the security of the ICS can be compromised.
It has always been a challenge for the security team to keep up with new threats but with ICS the impact could be unimaginable.
What is "ICS SCADA Security Testing"?
"ICS SCADA Security Testing" refers to the process of evaluating and assessing the security posture of Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems. These systems are used to monitor and control critical infrastructure such as power plants, water treatment facilities, manufacturing plants, and more. Security testing aims to identify vulnerabilities, weaknesses, and potential threats that could be exploited by malicious actors to disrupt or damage the infrastructure.
Why is ICS/SCADA security testing important?
ICS/SCADA (Supervisory Control and Data Acquisition) technologies are becoming high-value targets for threat actors for disrupting business operations, ransomware or compromising rival nation's systems. It is becoming crucial to address these security issues. The organisations should understand that even running on internal networks, their systems are exposed to cyberattacks if they are not adequately secured. It is important to conduct ICS security testing and implement the necessary compliances and regulations. The ICS/SCADA Security Testing or ICS/SCADA Penetration Testing helps in finding all the flaws that may cause a problem in future hence must be resolved on time.
Our approach to ICS/SCADA Security Testing
1. ICS Cyber security framework - Presenting a framework for the ICS/SCADA penetration testing requirements on accessing the entire system.
2. ICS/SCADA Risk Assessment - Gathering information regarding the applications and components required for conducting the testing.
3. ICS/SCADA gap analysis - Analysing the current and desired system gap to reduce the risk and eliminate threats.
4. ICS/SCADA Penetration Testing - Scanning the network with various tools to identify vulnerabilities.
5. ICS/SCADA services - Trying to exploit the vulnerabilities identified, manually with the help of commercial tools and custom scripts and Powershell.
6. ICS incident response - A detailed report of the assessment, including an executive summary for the management. This comprises the complete findings with risk priorities, remediations and recommendations made as a part of ICS/SCADA security testing.
ICS/SCADA tests require proper planning and a tailored approach for the testing. Our expert team can help you in getting the complete picture of your risk exposure with recommendations to resolve before they are exploited.
Talk to our executive and get your security testing conducted.







