Cybersecurity Due Diligence: Fortify Your Digital Perimeter with Expert Precision.
In today's highly interconnected and rapidly evolving business landscape, the protection of sensitive data and digital assets is paramount. As organizations engage in mergers, acquisitions, partnerships, and other strategic transactions, the risks associated with cybersecurity breaches loom larger than ever before. In this context, robust cybersecurity due diligence emerges as an indispensable safeguard, ensuring that organizations navigate the intricate web of digital risks with confidence and resilience.
What is Cybersecurity Due Diligence?
Cybersecurity due diligence is a critical process aimed at identifying, assessing, and mitigating cyber risks within an organization's network ecosystem. It involves thoroughly examining the governance, processes, and controls utilized to safeguard information assets. This evaluation extends beyond the organization itself to include third-party vendors and external stakeholders, such as partners and suppliers.
During cybersecurity due diligence, comprehensive insights are gathered into the cybersecurity posture of third-party vendors, as well as the efforts undertaken by internal security teams. This allows clients to gain a deeper understanding of potential vulnerabilities and cybersecurity risks associated with their business relationships.
In the context of mergers and acquisitions, cybersecurity due diligence plays a pivotal role in uncovering any issues that may impact the deal's terms, conditions, or overall valuation. By conducting a thorough assessment, organizations can identify and address potential risks proactively, ensuring compliance and minimizing the impact of cyber threats.
Ultimately, cybersecurity due diligence serves as a proactive measure to safeguard against cyber risks and enhance overall security resilience. By conducting due diligence assessments, organizations can strengthen their cybersecurity posture, protect sensitive information, and mitigate potential threats effectively.
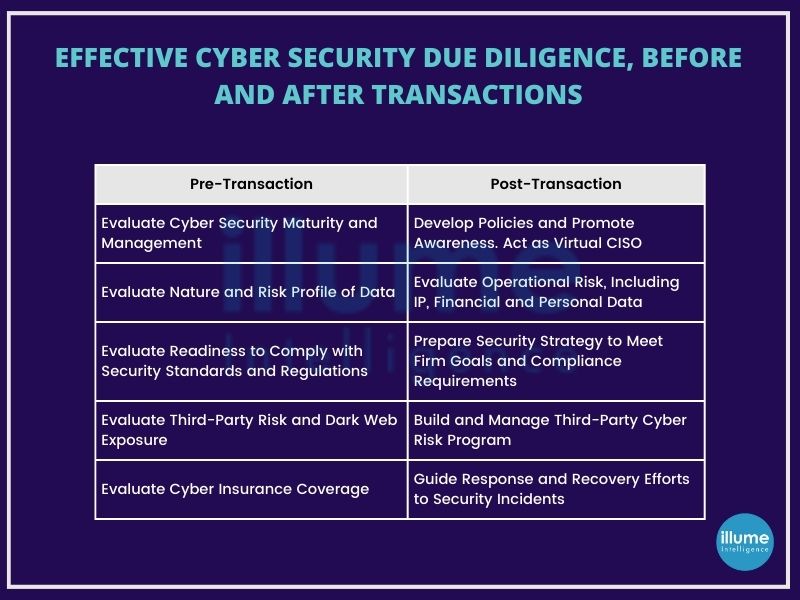
Importance of Cyber Due Diligence
Cybersecurity due diligence offers organizations unparalleled insights into potential risks and vulnerabilities. Let's delve deeper into why cybersecurity due diligence matters:
1. Comprehensive Risk Assessment: By conducting cybersecurity due diligence, organizations gain a comprehensive understanding of potential risks associated with mergers, acquisitions, or partnerships. This assessment allows for the identification of any issues that could impact the terms or structure of a deal, enabling informed decision-making and risk mitigation strategies.
2. Third-Party Risk Management: Cybersecurity due diligence provides a detailed examination of third-party vendors' security networks, vulnerabilities, and threats. This scrutiny allows organizations to assess the viability of business relationships and implement measures to mitigate associated risks effectively.
3. Enhanced Cyber Threat Awareness: Through cyber due diligence, organizations gain valuable insights into the cyber threat landscape, enabling proactive measures to address emerging threats and vulnerabilities. This heightened awareness empowers organizations to stay ahead of potential cyber-attacks and safeguard critical assets.
4. Cybersecurity Risk Ratings: Leveraging cybersecurity risk ratings enables organizations to better manage cyber risk associated with third-party relationships and supply chain partnerships. These ratings provide transparency and assist in assessing, calculating, and managing security risks effectively, particularly during periods of business growth or investment.
5. Continuous Monitoring and Mitigation: It facilitates continuous monitoring of cyber risk and allows organizations to evaluate performance over the short and long term. Through prompt alerts and data-driven insights, organizations can identify and address security issues swiftly, ensuring ongoing protection against evolving threats.
6. Data Privacy and Compliance Assurance: Helps organizations understand the complexities of data privacy policies and security protocols followed by target companies. This ensures compliance with regulatory requirements and reinforces trust with stakeholders by demonstrating a commitment to safeguarding sensitive information.
In essence, cybersecurity due diligence serves as a cornerstone in safeguarding organizational assets, reputation, and resilience in the face of evolving cyber threats. By conducting thorough assessments and implementing proactive measures, organizations can navigate the digital landscape with confidence and fortify their cybersecurity posture for long-term success.
Who needs cyber due diligence?
Cyber due diligence is essential for various entities and scenarios, including:
1. Mergers and Acquisitions (M&A): Both acquiring and target companies in M&A transactions need cyber due diligence to assess the cybersecurity posture of the target company. This helps in identifying potential risks, liabilities, and vulnerabilities associated with the acquisition.
2. Investors and Venture Capitalists: Investors and venture capitalists conducting due diligence before investing in a company need to evaluate its cybersecurity measures. This ensures that their investment is protected against cyber threats and potential data breaches.
3. Startups and Small Businesses: Startups and small businesses often undergo cyber due diligence when partnering with larger corporations, entering into contracts, or seeking funding. It helps them demonstrate their commitment to cybersecurity and enhances their credibility.
4. Government Agencies and Contractors: Government agencies and contractors handling sensitive data or providing critical infrastructure services are subject to cyber due diligence to comply with regulatory requirements and safeguard national security interests.
5. Service Providers and Vendors: Service providers and vendors offering software, IT services, or cloud solutions may undergo cyber due diligence as part of their clients' vendor management processes. This ensures that they meet cybersecurity standards and protect clients' data.
6. Compliance and Regulatory Requirements: Companies operating in regulated industries such as finance, healthcare, and telecommunications are required to undergo cyber due diligence to comply with industry-specific regulations and standards.
Overall, any organization that handles sensitive data, relies on digital infrastructure or is involved in transactions where cybersecurity is a concern can benefit from cyber due diligence. It helps identify and mitigate risks, protects assets and data, and enhances trust and confidence among stakeholders.
Illume Intelligence’s Approach to Cyber Due Diligence
As pioneers in providing due diligence services, we've honed our approach to cybersecurity and data privacy assessments. Our methodology encompasses the following key steps:
1. Phased Evaluation and Risk Assessment:
-
We conduct a phased evaluation of the target company's cybersecurity posture, systematically assessing governance structures, operational practices, and technological infrastructure. This comprehensive approach ensures a thorough understanding of potential risks.
2. Risk Calculation:
-
Our experts meticulously calculate the risks identified during the evaluation process, considering factors such as the likelihood of occurrence and potential impact on your organization. This quantitative analysis provides clarity on the severity of each risk and informs decision-making.
3. Development of Risk-Handling Mechanisms:
-
Based on our findings, we collaborate with your team to develop tailored risk-handling mechanisms. Whether it's implementing mitigating controls, negotiating terms, or allocating resources for remediation, we guide you through the process to effectively manage cyber risks.
With our cybersecurity due diligence services, you can approach mergers, acquisitions, and partnerships with confidence, knowing that your investments are protected and your organization is equipped to navigate the complexities of the digital landscape.
Here's how our comprehensive approach can benefit your organization
1. Identifying Information Security Risks:
-
Our meticulous assessment uncovers any vulnerabilities or shortcomings in governance, operations, and technology within the target company. By identifying these risks upfront, we empower you to make informed decisions and mitigate potential threats.
2. Researching Undisclosed Data Breaches:
-
Our experts delve into the target company's cybersecurity history to uncover any undisclosed or unknown data breaches. This proactive approach enables you to address any hidden issues before they escalate into costly post-transaction risks.
3. Assessing Incident Response Capabilities:
-
We evaluate the target company's ability to detect and respond to cybersecurity incidents promptly. This assessment provides insights into the effectiveness of their incident response procedures and helps you gauge their readiness to handle cyber threats.
4. Quantifying Remediation Costs:
-
Leveraging our expertise, we quantify potential remediation costs from various perspectives, including operational, financial, and reputational. By understanding the full scope of potential exposures, you can make informed decisions and allocate resources strategically.
In an era defined by relentless innovation and unparalleled connectivity, the need for proactive cybersecurity diligence has never been greater. Whether navigating complex mergers, acquisitions, or strategic partnerships or simply seeking to fortify cybersecurity defences against emerging threats, our Cybersecurity Due Diligence Services offer peace of mind and confidence in an uncertain world.
Cyber Due Diligence Service Modules
Unlock comprehensive insights and mitigate information security risks with our tailored cyber due diligence service modules. We offer four distinct modules designed to empower you in uncovering, assessing, and addressing cybersecurity risks, both pre-and post-transaction. Each module is fully customizable to suit the unique requirements of your transaction. You have the flexibility to select and deploy the combination of services that best aligns with your risk concerns, transaction timelines, and access levels to the target company.
For organizations embarking on acquisitions, positive findings or swift remediation actions resulting from our assessments, particularly Modules 3 and 4, can serve to assuage potential buyers' concerns and expedite the closure of deals.







