Discovering the security flaws in your VoIP infrastructure to secure from external attacks
VoIP (Voice over Internet Protocol) has become important for businesses and hence a good option for the attacker to exploit whenever left unprotected. Unlike other IT infrastructure, VoIP is also subjected to risks like interception, caller ID spoofing, Denial of Service (DoS) etc.
VoIP security is not only about call encryption, it is the level of trust that's conveyed over the text and voice network. If it is compromised, it can become a huge threat by carrying out more attacks.
A VoIP security assessment is a manual assessment of the security of the VoIP infrastructure. It identifies the vulnerability in the VoIP system to reduce the risk of financial loss or unauthorized access.
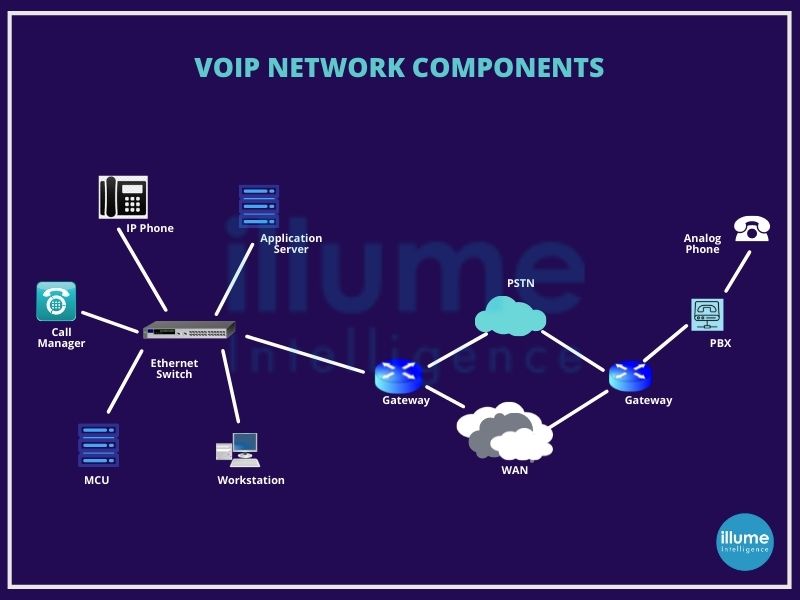
Securing a VoIP network is important for every organisation in a world full of uncertainties. Our team accesses the VoIP infrastructure to determine the risk of all the possible network infrastructure attacks. Evaluating the different VoIP components from the security perspective and capability to ensure they maintain confidentiality, integrity and availability. VoIP security assessment generally includes-
1. Application-level vulnerabilities
2. Extension enumeration and number harvesting
3. Default credentials testing
4. Voicemail security testing
5. Traffic capture and eavesdropping
6. Caller ID spoofing
7. Identifying DoS vulnerabilities
8. Design and configuration issues
How is VoIP security assessment performed?
The general approach is to gain access to the network and identify the vulnerabilities which are explained in the steps below -
1. Information gathering - Gathering all the possible information about the IP of servers, VoIP devices, PSTN's signalling system etc.
2. Enumeration - Gathering information about services running in the environment.
3. Vulnerability analysis - Identifying the vulnerabilities in the devices, services and infrastructure.
4. Attacking - Exploiting the vulnerabilities to gain access and accessing the scope of attacks
5. Report and Support - Presenting a detailed report on the vulnerabilities found with their strength, risk and standard associated with the security. Assisting in deploying the mitigation strategies as suggested in the assessment.
It is important to resolve the flaws as early as possible as the slightest negligence can result in severe financial and property losses. Application of required regulations for every business using VoIP infrastructure.
Are you still using unprotected VoIP services for your business? We can help in securing your VoIP infrastructure located anywhere in the world. Contact us via call or write an email and we will be there for assistance.







