In the era of soaring cyber crimes, Ethical Hacking will work as a tool to safeguard your organisation's security
Amid the increasing online crimes and data theft, every organisation must protect against cybercrimes, irrespective of their size. Smaller companies often fall into the trap of threat actors as they think they don't have much to secure or they don't have a budget to install any security services. If applied properly, this doesn't need huge budgets to protect their sensitive data or the organisation's security.
Before talking about Ethical Hacking Services, we should know Why data is a valuable asset for any organisation. It needs to be protected from internal or external and illegal access else may lead to severe financial loss, reputational loss, customer trust degradation and brand erosion. Government and Security organisations have applied rules on data protection for the organisations/ industries and in case of non-compliance, this may lead to big troubles.
All organisations must adhere to the CIA triad (Confidentiality, Integrity and Availability) for data security and apply relevant measures to ensure data security. But there are still incidents happening because of some or other reasons. Hence ethical hackers (hackers that work with a positive approach) are required to comprehend the flaws better from the threat actors' point of view. Once discovered it is easy to plan a security roadmap and apply preventive measures.
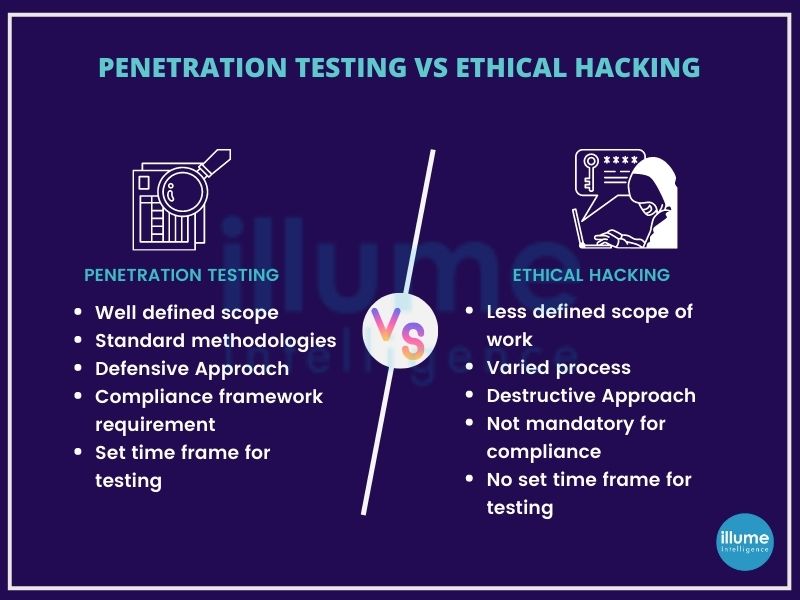
What are Ethical Hacking services?
The word hacking itself is capable of giving goosebumps to anyone so, how come Ethical Hacking is its solution? As the term says Ethical Hacking is the practice of making authorised attempts to hack into the security for finding the strength of the security posture.
No matter what you apply all the security methods, the slightest miss can bring down the entire system. So understanding the hackers' perspective helps in protecting the system in a better way. Ethical hackers intend to find loops for fixing them before they fall into the eyes of bad guys.
The aim of ethical hacking is to protect the data, system and infrastructure from threats and contribute to the success of the digital business. The information and data are kept secure as required by the business.
Identifying risks and weaknesses of the network to provide detailed reports with preventive measures along with guidance for implementing them is the core objective of ethical hacking.
What is included in Ethical Hacking Services?
Illume Intelligence’s ethical hacking services include the evaluation of infrastructure, devices, applications, networks etc as per the requirement of the organisation. It uses both automated and manual tools to gather information. Based on the information gathered the attack vectors are planned.
Our ethical hacking services focus on all the areas of your business, compliance, operations, security, awareness etc, providing insights into particular threats and vulnerabilities causing challenges to your organisation. Below are the services offered
-
Ethical Hacking Consultation
-
Vulnerability Assessment and Customized reporting
-
Ethical Hacking Remediation support
-
Internal systems assessment
-
Social engineering (phishing) exercises
-
External network penetration testing
-
Web application penetration testing
-
Cloud services Vulnerability Assessment
-
Wireless Security Assessment
-
Infrastructure architecture review
How Illume Intelligence's Ethical Hacking services can help?
Illume Intelligence's team of ethical hackers will customize the security services to meet the organisation's needs. From the quick vulnerability assessment to the complete security assessment of the entire organisation is supported by our skilled professionals.
Understanding the client's needs and preparing the strategy to address them with precision and optimum utilisation of resources. We address the needs of big organisations and SMBs with the required capabilities in a flawless manner with our industry expertise gained through experience. Our commitment to quality services is shown by our client's satisfaction and retention.
Are you still wondering whether to avail of Ethical Hacking services or not? We understand your business concern and advise you to talk to our security expert in finding the best methods to enhance your organisation’s security.
Taking action now is far better than regretting it in future.







