Understand and prepare for your SOC 2 assessment today to secure internal and client's businesses.
With the increasing cyberattacks, all the organisations are subjected to the risks like malware, phishing, DDoS attacks etc. Hence saas and Cloud computing vendors are required to undergo SOC 2 audits to assess and ensure their internal security controls.
SOC 2 framework (System and organisation Controls) was created by the American Institute of Certified Public Accountants (AICPA) in response to the growing concerns for data security and privacy. It is an independent auditing procedure ensuring that service providers handle sensitive client data securely on the cloud and maintain its privacy.
SOC 2 certified means the organisation has established practices as required with levels of security across the organisation for data protection. Saas companies that manage customer data in the cloud should be SOC 2 compliant. This audit is performed annually. Although SOC 2 is not a legal requirement, it shows the trustworthiness of the service provider and assures the clients that their data will be handled securely.
SOC 2 audit preparation
SOC 2 evaluates the security control's effectiveness over a period. The audit preparation has eight steps-
1. Defining the SOC reporting period
2. Quantifying Risk
3. Defining the Scope
4. Building a strong compliance team
5. Readiness assessment
6. Identifying gaps
7. Remediation
8. Gathering additional documentation
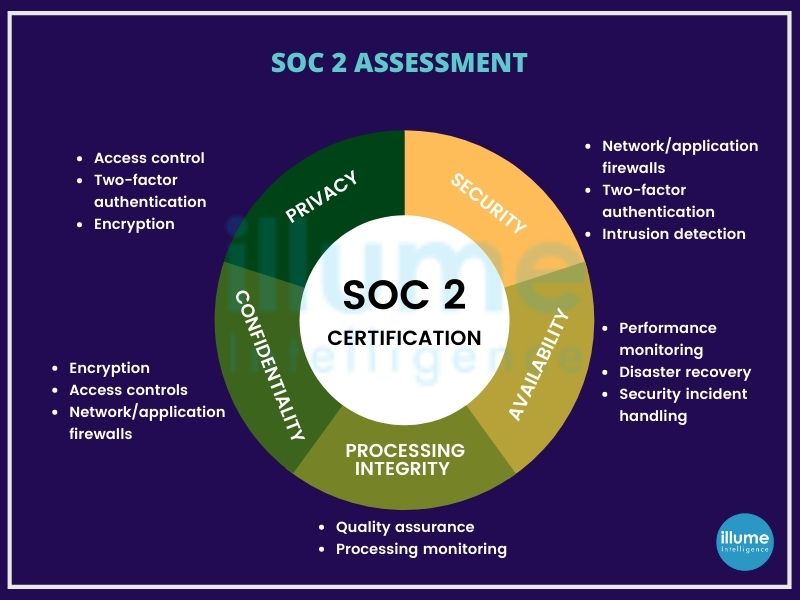
5 trust service principles of the SOC 2 compliance -
1. Security - Security is important and includes common criteria related to data and system protection.
2. Availability - Availability ensures the access to data the customer receives and how readily available it is. Also reviews accessibility for operations, monitoring and maintenance of data.
3. Processing integrity - The processing of data as per authorization and assesses the accuracy, completeness, validity and timeliness of the data.
4. Confidentiality - Encourages the encryption of in-transit data as well as client certificates and personal authentication certificates.
5. Privacy - Aims at ensuring the confidentiality and security of personal identifiable information (PII).
Why SOC 2 Assessment for your organsation?
1. Trust and Reputation - Increased customer trust and organisational reputation
2. Better Data Protection - Increased data protection with the application of norms
3. Improved Outlook - Increased security, availability, processing integrity, and privacy
4. Increased Awareness - Better awareness of organisational vulnerabilities
5. Marketing Differentiator - Marketing differentiator among others by adhering to rigorous standard with SOC2 Audit
6. Operating Effectiveness - Ensures maintaining an effective information security control environment
7. Commitment to IT Security - Strong commitment towards overall IT security
8. Regulatory Compliance - SOC2 requirements goes in sync with other frameworks including HIPAA and ISO 27001
How often do you schedule a SOC2 Audit?
Normally a SOC2 report is for a 12 month duration, but the auditing can be performed in the duration of every 6 months depending on the requirements of the organisation for the ongoing concerns in the operational control environment.
SOC 2 audits and reports provide detailed evidence of the effective security controls implemented in the service provider's system. It makes the vendor trustworthy and gives an edge over competitors.
Book your SOC 2 audit today and raise the bar for the competition.







