Bringing experience, expertise and leadership with virtual CISO to your organisation.
Securing your organization's data and customers' sensitive information associated with the business needs constant efforts along with the guidance of an expert executive-level leader called CISO(Chief Information Security Officer). It is not easy and affordable for all organizations to identify a security professional with expertise, experience and leadership skills to help in preparing and executing a successful security strategy.
Here a virtual CISO (Outsourced security professional) comes into the picture, who offers their expertise in designing or managing the organization's security strategy. This gives the organizations access to experienced cybersecurity, risk and compliance professionals at an affordable range.
Identifying an experienced and qualified CISO in today's competitive world is very challenging. Our virtual CISO can strengthen the IT Staff, set business supporting strategies, balance the administration and establish clear communications in the internal hierarchy of the organisation and stakeholders.
Where Virtual CISO is required?
Although vCISO is very important in designing and managing the security policies and strategies of an organisation, at a certain place their guidance becomes inevitable.
1. Planning of security audits, reviews and assessments.
2. Developing a new security strategy for threat management.
3. Getting compliance-ready.
4. Procuring new security components or expanding the network.
5. Recruiting or training the IT and security personnel.
6. Remediating the security incidents.
By employing a virtual CISO, one gets the benefit of advisory support from an industry expert familiar with the security challenges across a wide range of industries. Our virtual CISO can provide regular counselling, project-based assistance, and guides in making business-critical decisions.
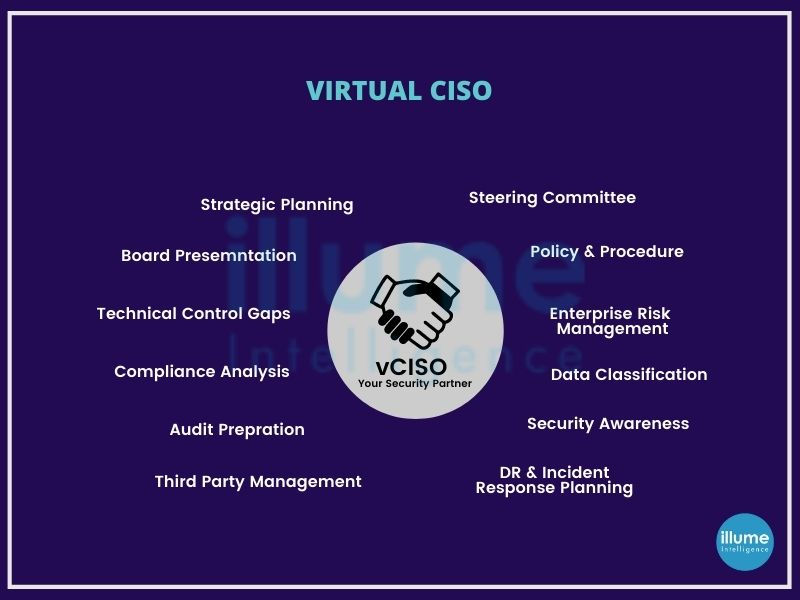
Key responsibilities of virtual CISO
Our virtual CISO aims at providing the security program leadership to guide the internal teams. Virtual CISO provides both the expertise and experience required for strategically leading the cyber security strategy. The key responsibilities of a virtual CISO are -
1. Implementing and Overseeing a Cybersecurity Program.
2. Planning of security audits, reviews and assessments.
3. Expert assessments on threat analysis and compliance.
4. Consultation for developing effective cybersecurity and resilience programs.
5. Aligning Cybersecurity & Business Objectives.
6. Reporting on Cybersecurity.
7. Monitoring Incident Response Activities.
8. Managing Business Continuity & Disaster Recovery.
9. Promote a Culture of Strong Information Security.
10. Managing Vendor Relationships.
11. Utilizing Cybersecurity Budgets Effectively.
12. Facilitating security integration into business strategies.
13. Assisting with the interpretation and integration of security program controls.
14. Serving as industry expert and security liaison to auditors and examiners.
Our virtual CISO helps our customers with effective advisory strategies and controls to build an upright cyber security structure.
Book your call to get your virtual CISO appointed.







