Implement NIST framework to Improve the organisational Critical Infrastructure along with all-time cyber threats protection
Cyber attacks have become a nightmare for businesses of all sizes. According to the researchers, cyberattacks cost businesses billions of dollars every year and these attacks are increasing in frequency and sophistication.
Strengthening organisational security with the frameworks is not a new concept for cybersecurity professionals. NIST is one of the most commonly accepted global cybersecurity frameworks that offer immense benefits with effective application among varied industries.
What is NIST?
NIST known as the National Institute of Standards and Technology, is a non-regulatory government agency that promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards and technology, all with a goal of greater economic security.
The NIST sets the standards and best practices for handling and securing data within government organisations and their contractors. These requirements help public and private sector organisations alike to plan comprehensive security programs with robust controls that ensure systems and data protection.
The most commonly used cybersecurity frameworks are -
- NIST Cybersecurity Framework (CSF)
- NIST 800-53
- NIST 800-171
The directions and cybersecurity approach provided by NIST can be easily applied to almost any sector and any business size. The NIST compliance strengthens the organisation's security posture and improves resilience. Adopting these guidelines helps in keeping the systems protected from breach along with ensuring compliance with other mandatory regulations like HIPAA and FISMA. Implementing NIST compliance may not be mandatory but this acts as a best practice standard for cybersecurity and data protection. It also provides a competitive advantage to the organisation.
The NIST Framework
The NIST Cybersecurity Framework provides guidance for organisations to improve security risk management. It is widely considered the gold standard for building cybersecurity programs. The scalability and customisation make it flexible for implementation at any level across various industries.
The NIST framework comprises three main components -
* Framework Core
* Implementation Tiers
* Profiles
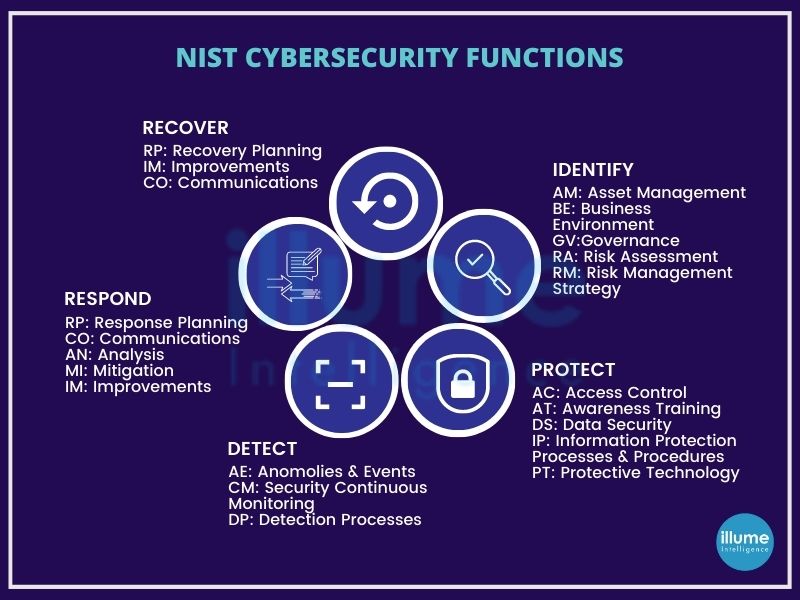
Framework Core - It is a set of cybersecurity activities, desired outcomes and applicable references that are common across critical infrastructure sectors. It comprises five functions - Identity, Protect, Detect, Respond and Recover.
Implementation Tiers - These describe the level of the organisation's cybersecurity risk management practice. These vary over a range from Partial (Tier 1) to Adaptive (Tier 4).
Profile - This represents the core functions categories and subcategories prioritized based on the business needs which are being used to measure the organisation's progress towards the target profile.
Why NIST?
The NIST framework provides an organisation with a list of guidelines and principles that are utilised to improve cybersecurity efforts. The framework provides an easy customisation of the cybersecurity strategy. It is precise and strict enough while providing the flexibility to manage risks in the most effective manner. NIST defines a four-step process for incident response mentioning it as a cyclical activity, as a process of continuous learning and improvement to discover a defence against cyber attacks. The four steps are
1. Preparation - This involves performing an inventory of IT infrastructure. Evaluating the importance of IT assets. Creating a policy for monitoring activities and a guide for incident handling.
2. Detection & Analysis - Data collection from IT systems, security tools, publicly available information etc and identifying incident signs that may happen in future.
3. Containment, Eradication and Recovery - This is for limiting the impact of a security incident. Eradicating the threat, restoring systems and recovering normal operations as quickly as possible with steps to ensure the attack happens again.
4. Post-Incident Activity - Security teams need to understand what went wrong, what needs to be changed, how can we do better and so on. This is required for strengthening the security policy and handling security incidents in future.
Approach NIST Cyber Risk Assessment with Illume
The NIST Risk Assessment aims at simplifying cybersecurity compliance but following all the outlined protocols can be complicated. Hence managed cybersecurity services provided by organisations such as Illume comes in handy to streamline the steps and ensure the proper applications of standards and guidelines. We understand the requirements of the organisations and know how to implement the steps outlined to secure the Infra and people against cyber threats. Our application of the latest outlined practices helps in easing the compliance journey.







