Identifying your small to severe security risks with vulnerability assessment
Vulnerability assessment as the name suggests is a process of systematically reviewing security weaknesses in an information system. Identifying the system if susceptible to any known vulnerabilities assigns priorities to them for addressing. Recommends remediation or mitigation, if and wherever needed.
This assessment provides the in-depth knowledge, awareness and background to understand and respond to the threats present in the environment of any organisation.
Types of vulnerability assessments
There are several types of vulnerability assessments, which includes -
1. Host assessment - Assessment of servers against vulnerabilities that may lead to severe attacks when left unattended.
2. Network and wireless assessment - Assessment of policies and practices to prevent unauthorized access to network resources.
3. Database assessment - Assessment of databases for vulnerabilities and misconfigurations, identifying rogue databases or insecure environments and classifying sensitive data across an organization's infrastructure.
4. Application scans - Assessing the web applications and their source code by scanning on the front-end or static/dynamic analysis of source code.
Knowing exactly how vulnerable you are is always a better choice than assuming that you are vulnerable to a cyberattack because with assumptions you can not plan the prevention. Hence a vulnerability assessment helps in testing some or all the systems as per the assessment goal and generates a detailed vulnerability report. Which can then be used to fix problems and avoid intrusions.
Benefits of conducting regular vulnerability assessments:
1. Identifying the loopholes in the security before attackers find them.
2. Ready inventory of all the network components with their purpose and system information. This also includes vulnerabilities associated with a specific device.
3. Ready inventory of all the devices in the organisation with the planning of upgrades and future assessments.
4. Risk assessment of the existing risk on the network.
5. Easy establishment of the risk/ benefit curve for optimized security investments.
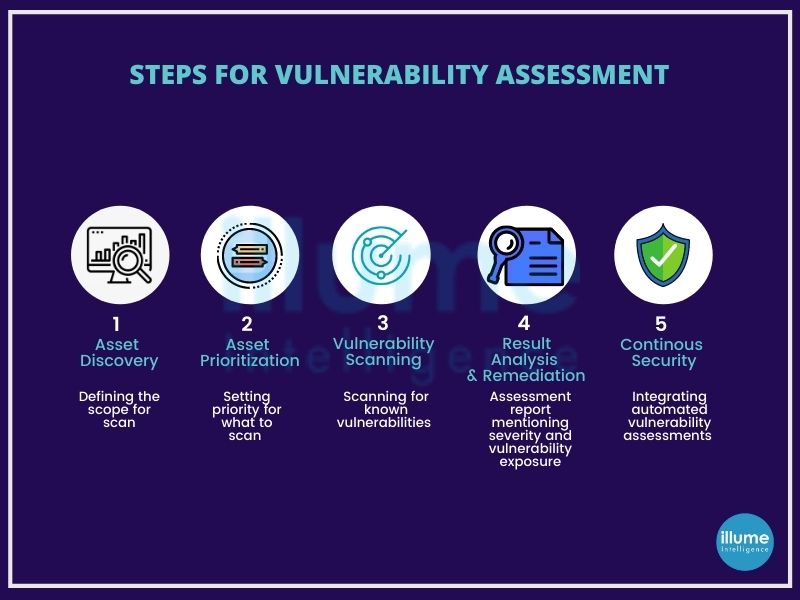
How is vulnerability assessment done?
The vulnerability assessment process consists of the following steps:
1. Identification - This phase focuses on listing the application's vulnerabilities. Scanning all the network components using automated tools and manually evaluating to make a complete list of vulnerabilities present.
2. Analysis - Identifying the source and root cause of the vulnerabilities identified in the previous phase.
3. Assessment - Once the risks have been identified, it is important to prioritize them according to the impact and risk associated.
4. Remediation - All the experts from the security, operations and development join hands to remediate each vulnerability.
Once the process is completed doesn't mean that it is done forever. Every day new vulnerabilities are getting detected hence it is advised to repeat the step at regular intervals.
What after vulnerability assessment?
The Vulnerability report generated is a documentation of the risks in the organisation's network, that need to be worked upon with the exerts for determining which vulnerabilities require a simple patch and which need to be addressed seriously with in-depth remediations.
This will lead to the next steps in the p[rocess like penetration testing, vulnerability management and overall risk management before setting goals for the next vulnerability assessment.
Vulnerability assessment informs on the weaknesses and loopholes present in the security of an organisation and guides in mitigating the risks emerging due to these weaknesses. For reducing the security risks, vulnerability assessment is a good choice. We provide a thorough, inclusive assessment of hardware and software. It is advised to conduct a regular assessment of the organisation’s system to assure safety from the attacks.







