Quick efficient support for managing and improving your responses to security incidents
When impacted by a cyberattack, a clear understanding is needed for analysing the situation and responding quickly for protecting the assets, operations and business reputation.
Incident response management is a set of policies and procedures that are used to identify, contain and eliminate cyberattacks. The aim is to enable an organisation to quickly detect and limit the attacks, minimising damages and preventing future attacks.
Preparing an Incident Response Management Plan will help an organisation in defining a clear understanding of what constitutes an incident for the organisation along with the clear guidelines on the process to be followed on the occurrence of the incident. It should also clearly mention the roles and responsibilities of the teams, employees or leaders responsible for complete incident handling.
The goal of an incident response management team is to coordinate and align the key resources and team members during a cyber security incident to minimise impact and restore operations as quickly as possible. This includes customised functions like investigation and analysis, communications, training and awareness, documentation and timeline development as per the organisation’s requirements.
Why is Incident Response Management Important?
Cyber attacks are increasing in scale and frequency making incident response plans a must for organisations’ cyber defences. Data breaches not only cost operational downtime but reputational and financial losses. The longer the time taken to detect and mitigate any vulnerability, the more harmful it becomes for the business. It may lead to devaluation of the stock value, loss of customer trust and heavy financial penalties from regulatory bodies making it impossible for the businesses to recover from the shock. To eliminate such risks, organisations need to plan -
1. Restoring daily business operations.
2. Minimising the attack surface.
3. Fixing cyber vulnerabilities quickly and effectively.
4. Securing the infrastructure by avoiding future attacks.
5. Aligning with the regulatory standards.
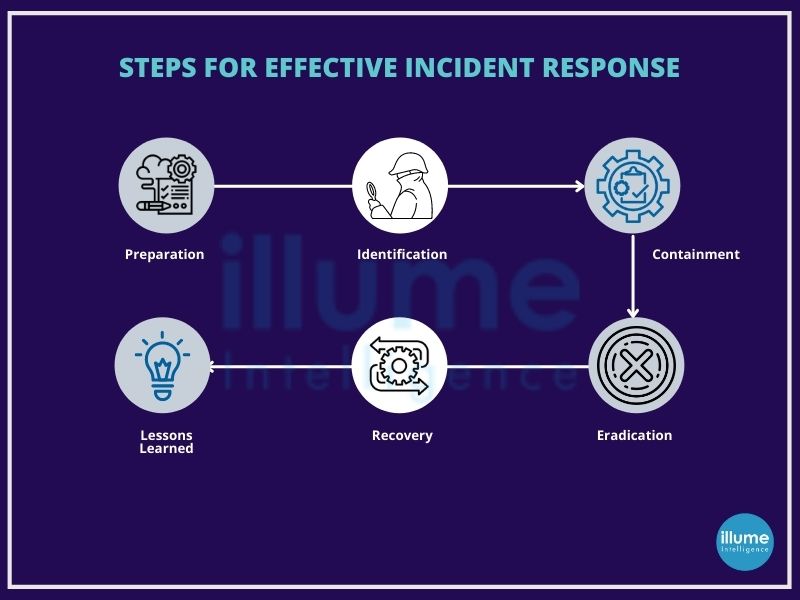
Steps for effective Incident Response Management
The SANS Institute provides guidelines for 6 steps for effective Incident Response Management
1. Preparation - Preparation involves reviewing the existing security measures and policies to determine the effectiveness of the current system. The gathered information will be useful for prioritising responses to the incident types. This should also involve policy, response plan, communication, documentation, determining CIRT members, access control, tools and training.
2. Identification - Once the tools and procedure are determined in the preparation phase, teams work to identify any suspicious activity. After detecting the incident, the team works to determine the nature of the attack, its source and the motive of the hacker.All the evidence found should be secured for in-depth analysis along with the proper documentation of the steps taken.
3. Containment - Containing the incident is the top priority as soon as the incident is detected, for containing the damage and preventing further damage from occurring. It is advised to follow SANS guidelines for preventing the destruction of any evidence that may be needed later for prosecution. These steps include short-term containment, system back-up, and long-term containment.
4. Eradication - The phase of neutralising the threat and restoring the system to as close to the previous state as possible. Ensuring proper removal of the malicious content and the affected systems are completely clean. If required the systems can be taken offline for replacing the clean versions in recovery.
5. Recovery - Bringing the recovered systems back online and ensuring the systems are not infected or compromised again by monitoring for some time. This includes setting timelines for fully restoring the operation and monitoring for abnormal activities. At this stage, it is also possible to calculate the cost of a breach and subsequent damage.
6. Lessons Learned - Often overlooked or ignored phase but is highly important as it helps to understand and improve future incident response efforts. This provides the opportunity for updating the incident response plans with the information gathered. This is highly helpful for review of the incident and may be used for recap meetings, training materials or as the benchmark for comparison.
There is a need for an incident response plan but shockingly very few organisations have a proper action plan. When talking about cyber security, time is a very crucial factor. The longer the time the attack is undetected, the more dangerous it becomes. It can destroy the organisation and its associates by using the organisation's data and network to launch a bigger attack spreading to other organisations as in the case of supply chain attacks.







