Discovering your Cybersecurity Vulnerabilities with Penetration Testing
Penetration testing also known as Pen Test across the IT Industry is the simulated cyber attack on your security system to check, how vulnerable your system is? This can be done for any web application or network.
With the increasing digitization of business operations and processes, we are more exposed to the risks of new technologies. Threat actors can easily exploit the vulnerabilities that exist within our IT infrastructure. It's not hard to imagine what all can happen once the hackers get access to the internal critical data of an organisation.
Mitigating the risk and avoiding these attacks from happening is the only way out. It is advisable to be capable of preventing, detecting, responding and recovering from such risks. No system can be 100% secure hence we need proper procedures in place to perform security assessments such as Penetration Testing.
Penetration testing helps in risk assessment, along with adhering to compliances and regulations. The organisation's reputation and security of critical data are also at stake due to these attacks, which can be saved using Penetration Testing.
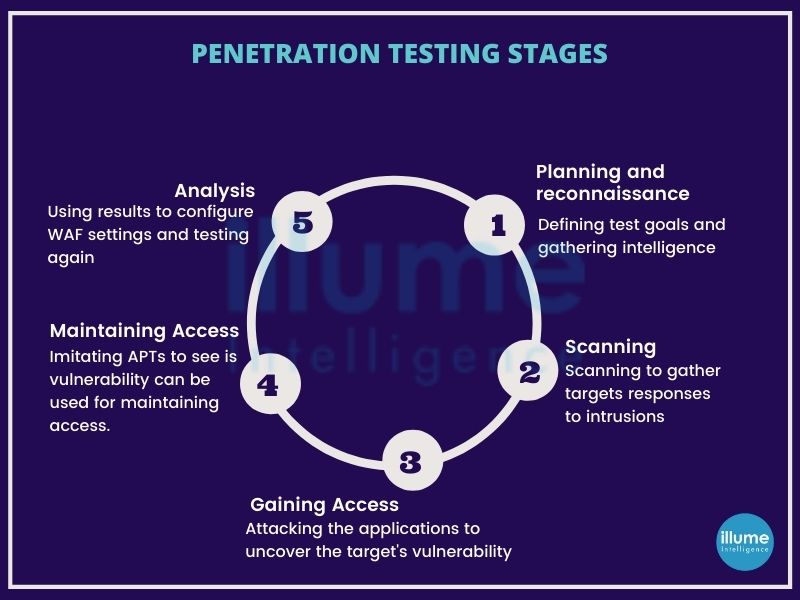
How do we implement Penetration Testing?
The type of testing depends upon the requirement of the organisation.
1. External Testing - Testing the organisational assets visible to the outside company's network, e.g. web applications, website, email and domain name servers.
2. Internal Testing - Testing from inside the corporate wherein the tester has got access to the organisational network as in case of stolen credentials.
3. Blind Testing - The tester is given limited information about the target and has to gather information from open sources.
4. Double-Blind Testing - Similar to blind testing but here in the organisation the security team is not updated about the activity. This helps in ascertaining how fast and effective the security team is in detecting the risk.
5. Targeted Testing - Tester and security person team up to keep each other updated on their movements. This helps in gaining real insights and feedback from the hacker's perspective.
Every organisation should conduct penetration testing on the regular basis especially after implementing any change in the IT infrastructure.
Contact us to safeguard your organisation from cyber threats.







