Preventing your data and services on the cloud with the latest techniques
Every business looking for expanding, selects cloud services for switching from on-premises hardware and technology. The cloud gives access to more applications, better data accessibility, effective team collaboration and easier content management.
Putting the data on the cloud brings many security challenges as well hence cloud security comes into the picture. Cloud Security or Cloud Computing Security is a collection of security measures designed to protect cloud-based infrastructure, applications and data. This ensures user authentication, device authentication, data privacy protection, data access control and resource access control. This also protects against DDoS, malware and other hacking attacks. It also supports regulatory data compliance.
Due to the features provided on the cloud, more and more IT professionals are concerned about shifting more data and applications to the cloud. Thus making cloud security more crucial. Preventing leaks and data theft is critical for maintaining a customer's trust and protecting his assets.
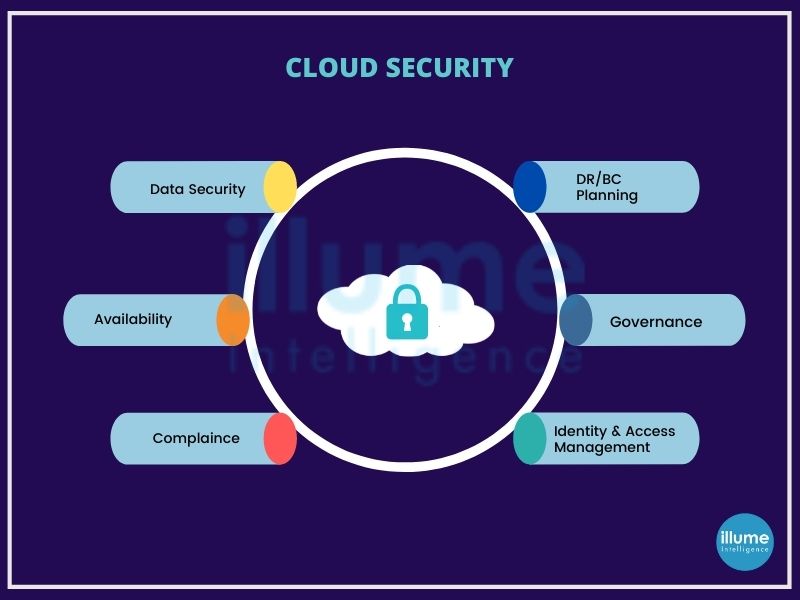
What does cloud security include?
Cloud security services encompass a variety of security measures, which may include:
1. Identity and access management (IAM) - Managing user identities, authentication, and access controls to ensure only authorized individuals can access cloud resources.
2. Data encryption - Encrypting data both at rest (stored in storage systems) and in transit (during transmission between systems) to protect against unauthorized access.
3. Network security - Implementing firewalls, intrusion detection/prevention systems, and secure network configurations to safeguard cloud networks from threats and attacks.
4. Vulnerability scanning and assessments - Regularly scanning cloud systems for vulnerabilities and conducting assessments to identify and address security weaknesses.
5. Security monitoring and incident response - Continuously monitoring cloud environments for suspicious activities or security breaches, and responding promptly to incidents to mitigate potential damage.
6. Security information and event management (SIEM) - Collecting and analyzing security event logs from various cloud resources to detect and respond to security incidents.
7. Security audits and compliance - Conduct audits and assessments to ensure compliance with industry standards and regulatory requirements.
8. Disaster recovery and business continuity - Implementing backup, replication, and recovery mechanisms to protect against data loss and ensure business continuity in case of disasters or disruptions.
What to look for when selecting a cloud security service for your business?
Finding the right solution for cloud services is essential for data protection and the company's overall safety. A good vendor should know the importance of security in cloud computing and have a few main features to lower risk.
1. Data Leakage Prevention - Built-in secure cloud computing controls to prevent issues such as unauthorized access, accidental data leakage and data theft.
2. Strong Authentication - Multi-factor authentication for all kinds of users and single sign-on to provide secure access to the users.
3. Data encryption - Security for both the data in rest and data in transit should be ensured.
4. Threat Detection - Automatic threat detection for unwanted behaviour and identity threats along with instant reporting.
5. Compliance Support - The services provided should be under regulation and compliance.
6. Integrated Security - The tools used by the service provider should integrate with your applications for a better user experience.
We aim at providing all the services you need at one point and for that, we may collaborate with some vendors to ensure your business security, integrity and continuity.
We protect our clients through a combination of threat intelligence, robust architecture and an efficient automated service delivery model. Testing and bringing the latest security features into our solutions to meet the client requirements with compliance is our agenda.
How secure is your present security system? Are you running your business from the cloud but still not sure about your data security? Maybe it's time to revise your cloud security services for enhanced business continuity.







