Securing your network by finding the vulnerabilities, like a hacker
Red Team testing as the name suggests is the assessment of the organisation network by trying to hack it. Red Team is the group of professionals responsible for emulating a genuinely malicious threat actor trying to break into the systems.
Real-world hackers don't follow any rules and methods, for exploiting the limitations of any testing programs. They will deploy any method to gain access, seek a point of entry for a successful breach. At times their passive attacks may exploit the organisations for a long time as they remain unnoticed.
A commonly employed method to breach an organisation's external security is combining social engineering and phishing. There are many ways to breach the first line of defense that depends on the human factor. Once the hackers get in they can steal sensitive data, deploy ransomware or exploit the organisation's resources.
With the increasing size of the organisation, the attack surface also increases and the difficulty to secure and monitor all the endpoints and users. It may be assumed that penetration testing is a great method to secure services, but it often focuses on a specific asset and has a defined scope.
Red Team Testing vs. Penetration Testing
Red Team testing also known as Red Team Security Testing is often confused with penetration testing, but pen testing is only a part of red team assessment. Red team operations have broader objectives than penetration testing.
These assessments are designed to emulate a more real-world scenario, with detailed analysis and defensive strategies. It also includes evasion and persistence, privilege escalation, and exfiltration. The Red team will test the organisation's detection and response capabilities.
How does Illume's Red Team work?
Our Red Team testing methodology covers methods to attempt real-time attacks on an organisation. We follow the ATT&CK Framework, which comprises of the knowledge base of adversary tactics, techniques, and procedures (TTP) based on real red and blue teams’ actual experiences.
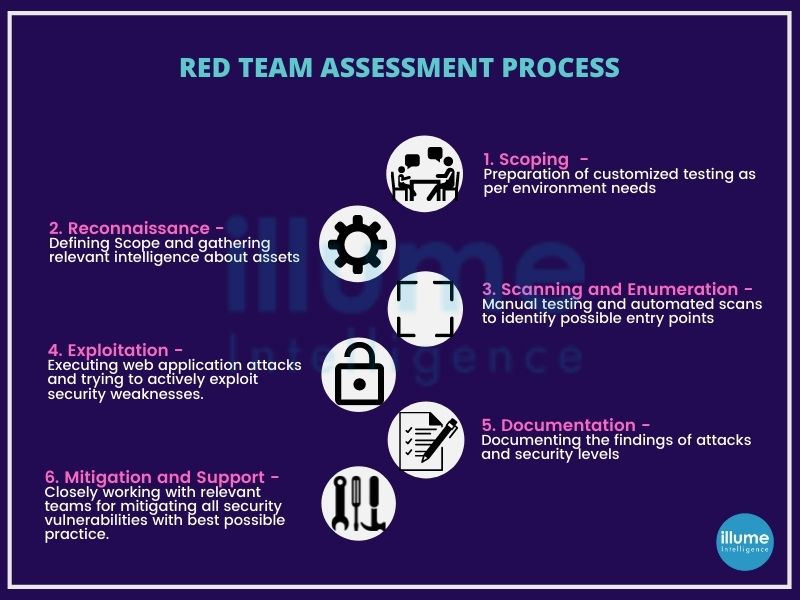
The methodology has the following steps -
1. Reconnaissance - This includes Scanning of several areas of the environment to determine interconnecting vulnerabilities and exposure.
2. Payload & Delivery - It is the ability to deliver a malicious payload of malware, ransomware, and viruses across parts of the environment leveraging email, social media, and web content as a rogue delivery tool.
3. Exploitation - This helps in finding the most susceptible areas to the risks in the environment.
4. Installation - This is to locate the scope of adding rouge devices, including WIFI, servers, and Internet of Things devices, without being detected across several parts of the environment.
5. Command & Control - Locating the endpoints and servers which can receive rouge communication instructions from the hackers.
6. Actions on Objectives - setting objectives to find if the response capabilities and defence mechanisms are working as expected across the environment.
7. Post-Engagement Reporting - The post-engagement report will cover remediation recommendations, including improvements to existing adaptive control and response capabilities, security measures, and incident response protocols.
The Red Team security assessment is a powerful technique for identifying the security vulnerabilities of any organisation. It will expose vulnerabilities, hidden from the organisation and mitigate them. Our Red Team assessment will enhance your organisation's security by uncovering the potential vulnerabilities to level up your security as expected.







