Strengthening your security with Firewall Security Testing and removing vulnerabilities
Firewall is the first line of defense in preventing cyber threats for any corporate network. Firewall security testing is the testing of the firewall done by pen testers similar to the threat actors for locating the vulnerabilities in the security method implemented or for deploying adequate security methods.
One can consider the firewall as the fencing around the periphery of the corporate network that secures against external threats and allows clients and trusted vendors traffic to enter. This traffic is often secured with the key given to them for the security of the network.
Considering and maintaining a firewall as an important component for security as it protects against data breaches or theft, is important for the organizations safety.
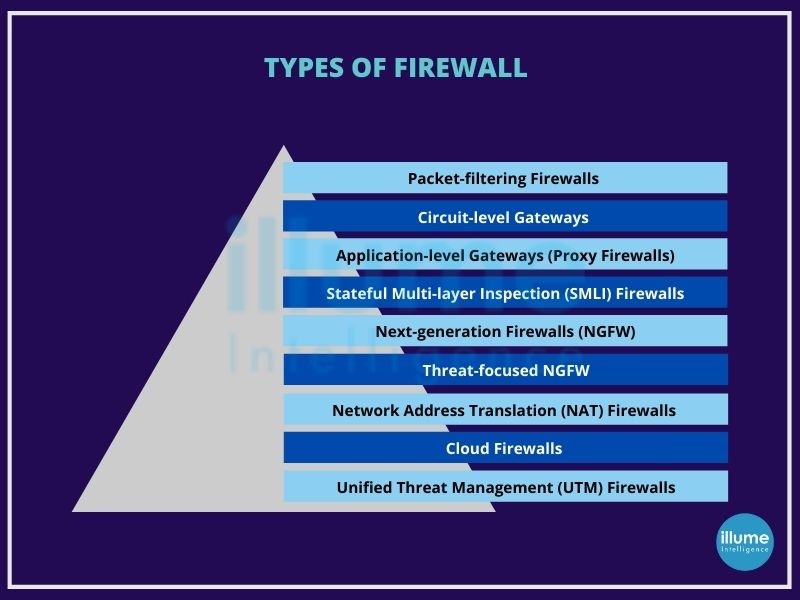
It is important to understand firewall security before implementing it as a security feature for your organization. Firewall security is
1. A preventive technical security control system (hardware/software).
2. Automated protection preventing unauthorised access.
3. An important part of business continuity plan and defense strategy.
Firewalls have their own predefined rules and filters to determine incoming traffic, hence making it important to configure them properly to achieve the expected security.
The idea behind firewall testing is to prevent unauthorized access to the secured network.
Why is firewall security testing needed?
Firewall security testing helps in identifying vulnerabilities in the network security posture. One can accordingly customize the security policies to ensure network security for intrusions.
1. Trust among stakeholders
2. Securing the company's network from malicious traffic
3. Proper configuration to remove the loopholes.
4. Regularly updating the system to keep it bug-free.
5. Proper functioning of the firewall rules.
Generally, firewall security testing (firewall penetration testing) includes locating the firewall, conducting traceroute, scanning ports, banner grabbing, access control enumeration, identifying the architecture, testing policies, firewalking, port redirection, internal and external testing, testing for covert channels, HTTP tunnelling and identifying firewall specific vulnerabilities.
How do we conduct firewall security testing?
1. Collect key information - Any security test can not be successful without complete information regarding hardware, software, rules, policies and risks.
2. Access Change Management - maintaining the proper record of changes done and changes required in the network.
3. Performing security checks on OS and physical components - evaluating the procedures deployed for the components and verifying the operating system passes standard rules.
4. Improving the rule base and decommissioning the old rules - decluttering the firewall rules by decommissioning old and inactive codes and rules.
5. Risk assessment and remediating - Analysing the risk and vulnerabilities. Making strategies to resolve and implement them.
6. Conducting regular audits - Penetration testing is required at regular intervals and specifically after implementing and changing.
Are you looking to implement firewall security testing? irrespective of the firewall implemented in your organisation, our experts will be able to find the vulnerabilities for suggest the best security measures required. Let's get your firewall secured.







