Securing the most critical network of the organisation and strengthening bonds with clients and stakeholders
WiFi is a wireless method of establishing network connections using radio waves. Due to its nature connecting WiFi has been a lucrative option for threat actors to penetrate organisations' networks. IoT devices have also enhanced the risk of cyber attacks.
Wireless penetration testing plays a role in identifying the potential vulnerabilities in the wireless network environment. It attempts to penetrate the network using any vulnerabilities to gain access. This helps in creating mitigation strategies for enhancing security.
What is the need to protect wireless networks?
Wireless networks enhance the organisation's performance and connectivity, however, they are also targeted by the threat actors to disclose the organisation's critical data. Organisations are required to follow certain regulations to do business by granting safety to the organisation's and customer's data.
Testing the wireless network can help in addressing the issues related to security controls along with real-world vulnerabilities. It will help in strengthening the security posture of the organisation as well as increasing customer trust and brand value.
How do we perform Wireless Penetration Testing?
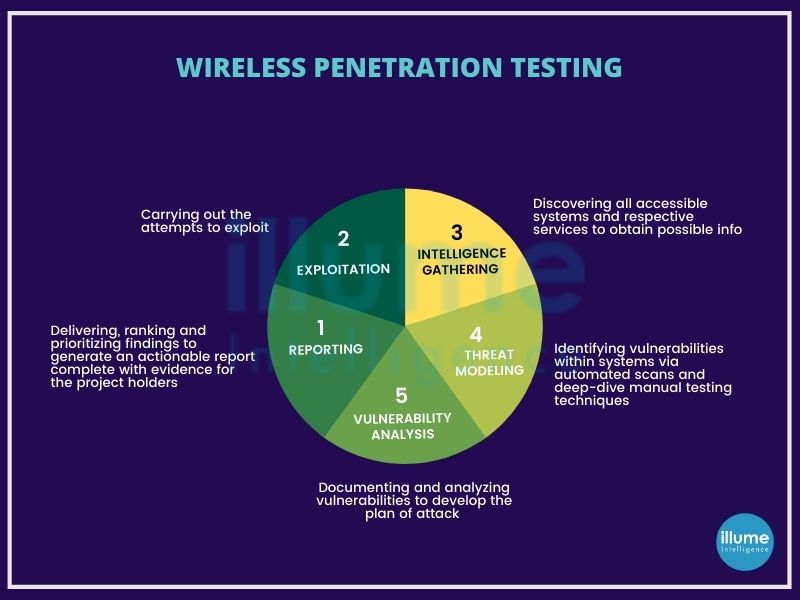
The wireless penetration testing at Illume Intelligence comprises various modes of analysis to identify vulnerabilities, resilience against threats and responses against attacks. We inculcate methods developed by Penetration Testing Execution Standard (PTES) and Information Systems Security Assessment Framework (ISSAF), suiting best to the organisations' needs:
1. Reconnaissance - Creating a comprehensive map of all the network components based on available systems and services.
2. Threat modelling - Combining automated scans and manual testing to determine the exposure to threats.
3. Vulnerability analysis - Documenting the analysis and development of the attack plan so that nothing skips.
4. Exploitation - Attacking the system to reveal the vulnerabilities impacting the network's security.
5. Reporting - Providing a complete report on the methods, processes, results etc, for better decisions on implementing adequate solutions.
How secure is your wireless network? We can be your reliable security partner enhancing your business security and growth.







