
ILLUME's AI Driven Cyber Attack Mitigation Plan for India
ILLUME Intelligence's AI-Driven Cyber Attack Mitigation Plan for India
AI-driven attacks use machine learning, automation, deepfakes, adversarial models, and AI-powered malware to exploit vulnerabilities faster and at scale.
Our mitigation plan ensures:
Early detection of AI-enabled threats
Protection of AI models and datasets
Compliance with Indian regulatory frameworks
Business contin
Read More
ILLUME's Enterprise Cyber Security Architecture
ILLUME's Enterprise Cyber Security Architecture defines the structured, layered controls required to protect organizational assets, reduce risk, and enable business resilience. Effective security is not measured by tool count, but by clarity of design, defined ownership, and integrated control execution.
1. Identity Security (Control Plane)
Identity serves as the primary control plane
Read More
Top AI Cyber Security Company Kerala India
1. What Is An AI Cyber Security Company Means to business enterprise?
AI Cyber Security Company capable to the use of artificial intelligence and machine learning to protect digital systems, networks, and data from cyber threats, as well as securing AI systems themselves against misuse or malicious attacks.
As An AI Cyber Security Company, ILLUME can deliver following Solutions:
Security A

What is Cybersecurity and Why It’s Critical for Small Businesses in 2025
Because you're never too small to be targeted anymore.
In June 2025, a small advertising firm in Lucknow, India, became the victim of a ransomware attack that encrypted all their files, from campaign creatives to client invoices. The attackers demanded a hefty ransom, and with no backups or contingency plan in place, the company had to rebuild weeks of work from scratch.
This wasn't a tech startup or a larg

What to expect from DPDP Consulting services in India: Ensuring Seamless Compliance
With the enactment of the Digital Personal Data Protection (DPDP) Act, 2023, India has taken a significant leap in regulating data privacy. The law mandates organizations—whether B2B or B2C—to establish robust mechanisms for data protection, consent management, and regulatory compliance. Failure to comply can result in hefty penalties, reputational damage, and loss of consumer trust.
This is where DPDP consultants step in. They provide e
Read More
DPDP Compliance: Key Differences Between E-commerce and Web Application Businesses
Are You Running an Ecommerce Business. And wondering if the E-commerce app is the same as the normal web application when implementing DPDP compliance?
Every business is going online to expand the reach and convenience for its customer, increasing dependency on the web apps and ecommerce apps. But there is a difference between the two apps when it comes to its security implementation. The web app is way different than the ecommerce app.
H

Designing DPDP-Compliant Web and Mobile Apps: A Comprehensive Guide for your Business
Are you using a web or mobile app for your business or planning to design a new one?
With data privacy becoming a critical concern, ensuring compliance with the Digital Personal Data Protection (DPDP) Act, 2023 is no longer optional. This regulation mandates how businesses collect, store, and process user data, making it essential to integrate compliance into the very fabric of your app and business.
In this gu
Read More
Integrating Cybersecurity into Business Continuity Planning: A Comprehensive Guide for Small and Large Enterprises
In a world where businesses increasingly rely on technology, the line between operational disruptions and cybersecurity threats has blurred. A natural disaster, a system outage, or a cyberattack can bring business operations to a standstill, often with devastating consequences.
The numbers are staggering, in 2023 alone, ransomware attacks cost businesses over $20 billion globally, with many organizations taking weeks to recover. For small businesses, 60% shut their
Read More
The Role of Cybersecurity Risk Management in Safeguarding Your Business
In the hyper-connected world, businesses are more exposed to cyber threats than ever before. From ransomware attacks that can paralyze operations to phishing schemes targeting employees, the digital landscape is fraught with risks. While large corporations often have dedicated teams to counter these threats, small and medium-sized businesses (SMBs) are often left vulnerable, lacking awareness.
According to a report by Accenture, 43% of cyber
Read More
Top 10 Security Oversights Startups Must Avoid to Protect Their Future
Starting a business is no easy feat. Entrepreneurs are often focused on product development, marketing, and scaling their startups. However, one crucial aspect that many tend to overlook is cybersecurity. According to a 2023 report from the National Cyber Security Alliance, 60% of small businesses that suffer a cyber attack close their doors within six months. With cyber threats becoming increasingly sophisticated, neglecting security from day one could be th
Read More
Post-VAPT Remediation: A Comprehensive Guide to Securing Your Organization
In today’s rapidly evolving digital landscape, cyber threats loom large over organizations of all sizes. Vulnerability Assessment and Penetration Testing (VAPT) acts as your first line of defence, uncovering weak links in your IT ecosystem. However, merely conducting VAPT is not enough, it is only half the battle. The real value lies in post-VAPT remediation—a structured and strategic approach to addressing vulnerabilities. According to Cybersecurity Ventures, cybercrime is projec
Read More
The Foundation of Security: Scoping for Web Application Red Team Testing in E-Commerce
In the ever-evolving e-commerce industry, where every click, transaction, and customer interaction occurs digitally, the security of web applications is paramount. Cybercriminals increasingly target these platforms for financial gain, data theft, or sheer disruption. While Red Team testing is one of the most effective methods to identify and mitigate risks, its success hinges on one critical factor: scoping.
Scoping for Red Team testing is not just
Read More
The Rise of AI-Driven Cyber Threats: How Pentesting Can Help Mitigate Risks
Imagine waking up on a regular Monday morning, only to find your phone buzzing with an urgent message from your security team. A cyberattack has hit your business. But this isn’t a typical breach—this is a new breed of attack powered by Artificial Intelligence (AI). The data is compromised, systems behave erratically, and there’s no time to waste. This isn't a scene from a sci-fi thriller; it's a very real risk we face in 2024. The AI not only has the power to transf
Read More
Why Pentesting Is Critical for Ransomware Resilience in 2024
Imagine waking up to find your organization’s entire network locked down, with a chilling ransom note on your screen demanding millions to restore access. Would you pay up, risking reputation and financial loss, or take the harder road of rebuilding everything from scratch?
It’s not a nightmare. It’s a real threat - “Ransomware” that has paralyzed businesses, stolen data, and shattered reputations worldwide. These ransomware attacks are
Read More
Cybersecurity in Smart Manufacturing: The Next Big Challenge
The rise of smart manufacturing—where IoT devices and connected systems automate and optimize production—has brought unprecedented efficiency to the industry. However, it has also introduced new cybersecurity challenges. With multiple access points, from sensors to industrial control systems, these smart factories are prime targets for cyberattacks.
In this blog, we’ll discuss the unique cy
Read More
The Role of AI in Penetration Testing: What Businesses Need to Know
As cyberattacks become more sophisticated, artificial intelligence (AI) transforms how organizations conduct penetration testing. AI-driven testing may promise faster vulnerability detection, automation of repetitive tasks, and deeper insights into potential security flaws. But does AI truly enhance the effectiveness of penetration testing, or are there limitations businesses should be aware of?
In this blog, we’ll explore how
Read More
What to Expect in a VAPT Report: A Comprehensive Guide for IT and Security Managers
After a Vulnerability Assessment and Penetration Testing (VAPT) exercise, the final deliverable is the VAPT report—a comprehensive document outlining the security flaws identified, the potential impact of those vulnerabilities, and recommended fixes. However, understanding this report in a way that can drive action is critical for IT and security managers.
In this blog, we’ll break down the key m
Read More
Red Teaming vs. Blue Teaming: Crafting a Holistic Security Strategy for Mining and Manufacturing
As cyber threats become more sophisticated, relying on one-dimensional security measures is no longer enough. Organizations need a balanced, proactive, and reactive defence strategy to safeguard their infrastructure. This is where Red Teaming and Blue Teaming come into play.
In this blog, we will break down the differences between Red Teaming and Blue Teaming, explain how they complement each other,
Read More
How Often Should Your Organization Conduct Penetration Tests? Industry-Specific Guidelines
Cyber threats evolve rapidly, and as technology advances, so do the methods of attackers. One of the most effective ways to stay ahead of these threats is through penetration testing (pentesting), which simulates real-world attacks to identify vulnerabilities before they are exploited. But how often should your organization perform these tests? The frequency of pentesting depends on various factors, including your industry, the sensitivity of your data, and compliance require
Read More
How Penetration Testing Can Help with Data Privacy Regulations: GDPR, HIPAA, and More
In an era when data breaches make headlines almost daily, compliance with data privacy regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) is not optional—it’s a necessity. Organizations, particularly those in sensitive sectors like healthcare and government, are under constant scrutiny to protect personal data.
Read More

ISO 27001 and CIS Controls: What Every Industry Should Know About Compliance
In today’s highly regulated business landscape, organizations across industries—especially in healthcare, government, and other critical sectors—must adhere to strict cybersecurity standards. Two of the most widely recognized frameworks are ISO 27001 and the Center for Internet Security (CIS) Controls. Both play a pivotal role in building and maintaining a robust cybersecurity posture, but compliance with th
Read More
Red Team Testing: Simulating Advanced Persistent Threats (APT) to Safeguard Critical Industries
As cyber threats continue to evolve, organizations in critical industries such as mining and government face an increasing risk from Advanced Persistent Threats (APTs). APTs represent sophisticated and prolonged attacks aimed at stealing sensitive information or causing significant disruption. According to a report by Mandiant, APT groups have been linked to high-profile incidents that led to extensive data breaches and compromised national security.
< Read More

Mobile Application Penetration Testing: Securing Your App for Healthcare and Government Use
As mobile applications become integral to healthcare and government operations, the importance of security testing cannot be overstated. With sensitive patient data and critical government information often accessed via mobile apps, vulnerabilities can lead to severe consequences, including data breaches, financial loss, and compromised safety. A staggering 43% of data breaches in healthcare are due to mobile app vulnerabilities, highlighting the urgent need for rigorous

The Rise of Ransomware Attacks in Logistics: How Red Teaming Can Safeguard Your Supply Chain
Ransomware attacks have surged dramatically in recent years, particularly affecting the logistics sector. As logistics companies manage vast amounts of sensitive data and critical infrastructure, they are prime targets for cybercriminals seeking to disrupt operations and extort ransom payments. According to Cybersecurity Ventures, ransomware damages are projected to reach $265 billion annually by 2031, making it a significant threat to industries reliant on t
Read More
Securing SaaS Platforms: The Crucial Role of Penetration Testing in Protecting Your Software as a Service
As Software as a Service (SaaS) continues to dominate the software landscape, offering businesses flexibility, scalability, and cost-effectiveness, it also opens the door to unique cybersecurity challenges. With the rapid adoption of SaaS solutions across various industries, companies must remain vigilant in protecting sensitive data from cyber threats.
Penetration testing (pentesting) emerges as a vital practice to identify and remediate vulnerabil
Read More
Cybersecurity for Startups: Building a Strong Defense with Early-Stage VAPT and Cost-Effective Solutions
For startups, cybersecurity might not always be top of mind in the early stages of growth, especially when resources are tight and the focus is on product development, scaling, and customer acquisition. However, in today’s digital-first environment, ignoring cybersecurity can be costly, even for small businesses.
Startups are prime targets for cyberattacks due to their perceived lack of robust security measures. A single breach could lead to stolen intellectua
Read More
Healthcare Data Breaches: Why Penetration Testing is Vital for Healthcare Providers to Stay Secure and Compliant
In today’s healthcare environment, data is as vital as the care itself. From patient records to medical devices, the healthcare sector is increasingly reliant on interconnected systems to deliver services. While this digital transformation has improved patient outcomes and operational efficiencies, it has also introduced a significant new risk: data breaches. With cyberattacks on the rise, healthcare providers must be vigilant about their cybersecurity practices to prot
Read More
Securing Your Enterprise IT Infrastructure: Why Vulnerability Testing is Critical for Logistics and Government Sectors
IT infrastructure security has become a mission-critical priority in an era where businesses and governments are more connected than ever. Whether it's ensuring the uninterrupted flow of goods across borders or safeguarding sensitive governmental data, IT systems form the backbone of operations in sectors like logistics and government. However, this connectivity comes with a heightened risk of cyberattacks, which can cause operational paralysis, reputational damage, and significant financ
Read More
VAPT vs. Red Team Testing: Choosing the Right Cybersecurity Strategy for Your Business
As cyber threats evolve, businesses face increasing pressure to safeguard their digital assets and customer data. Whether you're running a startup, a manufacturing plant, or a government agency, ensuring the security of your IT infrastructure has never been more critical. But with multiple security services available, how do you know which one is right?
Vulnerability Assessment and Penetration Testing (VAPT) and Red Team testing are commonly confused but distinc
Read More
Unlocking the Power of Penetration Testing: Why Every Industry Needs It to Stay Secure
In today’s increasingly digital world, cyberattacks have become a daily reality. From high-profile data breaches to sophisticated ransomware operations, no industry is immune. This evolving threat landscape demands proactive measures to secure sensitive data, operational systems, and customer trust. That’s where penetration testing (pentesting) comes into play. Whether in healthcare, manufacturing, logistics, or even a startup, understanding what penetration testi
Read More
Strategic Security Within Budget Constraints for SaaS Companies
In the ever-evolving landscape of cybersecurity, SaaS organizations face a dual challenge: safeguarding sensitive data and systems while navigating budget constraints. As cyber threats become more sophisticated and regulatory demands intensify, finding a balance between robust security measures and financial feasibility is critical. Fortunately, several cost-effective strategies can enhance your cybersecurity posture without breaking the bank. As an expert in the field, Illume Intelligence wi
Read More
Network Segmentation: A Budget-Savvy Approach to Strengthening Cybersecurity for SaaS Companies
In the digital landscape, where cyber threats are escalating and data breaches are becoming more frequent, maintaining robust cybersecurity is non-negotiable for SaaS companies. The global cost of cybercrime reached a staggering $8.44 trillion in 2023, highlighting the severity of the threat facing businesses today. For SaaS organizations, particularly those operating on a tight budget, the challenge is twofold: ensuring the protection of sensitive data and systems while managing expenses eff
Read More
Mastering Cybersecurity on a Shoestring: Essential Strategies for Budget-Conscious SaaS Organizations
In an era where cyberattacks are becoming increasingly sophisticated and costly, safeguarding your SaaS organization’s infrastructure is more critical than ever. Did you know that in 2023, the global cost of cybercrime surged to a staggering $8.44 trillion? For SaaS companies, this threat is even more pronounced, as they manage sensitive customer data and often operate under stringent international compliance standards. According to a recent report, 43% of cyberattacks target small and
Read More
Safeguarding Indian Businesses in the Age of Cyber Threats: Strategies for a Secure Future
Imagine arriving at your office one morning only to find your systems locked, your data held hostage, and a ransom note demanding an exorbitant fee for its release. Unfortunately, this is not just a plot from a thriller but a reality many businesses in India face today. Cyber threats have become a stark reality as we embrace the digital age, and safeguarding our businesses has never been more critical.
In recent years, India has rapidly transformed into a digital po
Read More
Prioritizing Supply Chain Security in Manufacturing: Why It’s Crucial and How to Achieve It
Is your manufacturing operation as secure as you think? In the age of Industry 4.0, cyber threats are no longer confined to IT systems—they have penetrated the very core of manufacturing processes, targeting supply chains with alarming frequency. Imagine the impact of a single breach: production halted, intellectual property stolen, and trust eroded. This isn’t a distant possibility; it’s a reality many manufacturers face today.
The manufactu
Read More
Navigating the Cybersecurity Challenges in the SaaS Industry
In today’s fast-paced digital landscape, Software as a Service (SaaS) has become the backbone of many businesses, offering unparalleled convenience, scalability, and efficiency. As SaaS platforms host vast amounts of sensitive data and critical business processes, they increasingly become prime cyberattack targets. According to Gartner, the global SaaS market is projected to reach $200 billion by 2024, but with growth comes an increase in cybersecurity threats.
< Read More

Ensuring Cybersecurity in Manufacturing: The Critical Role of Continuous Monitoring and Incident Response
Can your manufacturing operation withstand the onslaught of a sophisticated cyberattack? In today's highly interconnected industrial landscape, the frequency and sophistication of cyber threats are escalating alarmingly. In 2023, ransomware crippled 66% of organizations, and IoT malware attacks skyrocketed by 400%, making the manufacturing sector the most targeted globally (Deloitte United States) (IBM - United States). These numbers are not just statistics; they represent real threats wi
Read More
Securing the Future: How SaaS Companies Can Thrive in an Era of Cyber Threats
In a rapidly evolving digital landscape, the phrase "You're only as strong as your weakest link" has never been more relevant. For SaaS companies, where every connection is a potential entry point for cyber threats, the stakes are particularly high. Imagine building a thriving business, only to see it crumble overnight due to a cyberattack that could have been prevented. This scenario is no longer hypothetical—it's happening, and it’s happening m
Read More
The Unsung Heroes of Cybersecurity: The Crucial Role of the Red Team in Cybersecurity
In the heart of a bustling metropolis, there's a high-stakes game of cat and mouse being played out every day. This game isn't taking place on the city streets between criminals and law enforcement but rather in the invisible, digital realm, where data is the treasure and hackers are the elusive foes. Here, two teams stand out as the stalwart guardians of our digital fortresses: the Red Team and the Blue Team. The Red Team in cybersecurity is akin to a squad of undercover operatives,
Read More
Leveraging Advanced Technologies to Bolster Cybersecurity in Manufacturing
Consider a major automotive manufacturer coming to a grinding halt because cybercriminals have infiltrated its production systems. Millions of dollars in losses disrupted supply chains, and a tarnished reputation. Unfortunately, this is not a hypothetical situation. In 2023, ransomware impacted 66 per cent of organizations, and there was a staggering 400 per cent increase in IoT malware attacks, with the manufacturing sector being the most targeted globally (Deloitte United States). This alar
Read More
Securing the Future: How Manufacturing Organizations Can Overcome Cybersecurity Challenges
In an age where digital transformation is revolutionizing industries, the manufacturing sector stands at a critical juncture. As advanced technologies like IoT, AI, and automation become integral to manufacturing operations, the cyber threat landscape is expanding at an alarming rate. But are manufacturing organizations truly prepared to combat these evolving threats?
A recent study revealed that cyberattacks on manufacturing organizations have surged by over 200% i
Read More
Cybersecurity Compliance in the Manufacturing Industry: A Comprehensive Guide
In the ever-evolving landscape of the manufacturing industry, cybersecurity has become a critical concern. Did you know that cyber attacks on manufacturing companies surged by over 300% in recent years? Are you aware that these breaches can lead to significant financial losses, operational disruptions, and damage to your brand's reputation? As manufacturing organizations increasingly integrate advanced technologies such as IoT and OT into their operations, the need for robust cybe
Read More
Navigating the Maze: Major IoT and OT Security Challenges in the Manufacturing Industry and How to Overcome Them
In today’s interconnected world, the manufacturing industry is rapidly embracing the Internet of Things (IoT) and Operational Technology (OT) to enhance productivity, streamline operations, and drive innovation. However, this digital transformation comes with a caveat: it opens up new avenues for cyber threats. With more devices connected than ever before, each serving as a potential entry point for malicious actors, the stakes are incredibly high. As a security expert and leader, under
Read More
Risk Management for the Manufacturing Industry: A Comprehensive Guide
Imagine your manufacturing operations grinding to a halt because of a cyber attack. What if critical intellectual property is stolen or your production lines are locked down by ransomware? In an era where digital and operational technologies converge, these scenarios are not merely theoretical—they are tangible threats faced by today’s manufacturers. With the stakes so high, how prepared is your organization to manage and mitigate these risks? Or how efficient is your risk managem
Read More
Stay Secure: Cyber Defense Strategies for Manufacturers
In today's highly interconnected world, the manufacturing sector stands at the forefront of technological innovation. However, this digital transformation brings with it an elevated risk of cyber threats. As manufacturing operations become increasingly dependent on complex IT systems, the potential impact of cyber attacks grows significantly.
Recent incidents in the industry highlight the pressing need for a robust cybersecurity strategy. From ransomware attacks
Read More
Major Cyber Attacks That Shook the Manufacturing Industry: Lessons Learned
The manufacturing industry stands as a pillar of global economic stability, driving innovation and production across various sectors. However, as technology advances and industrial processes become more interconnected, the sector faces an escalating threat: cyber attacks. In an era where everything from assembly lines to supply chains relies heavily on digital infrastructure, the vulnerabilities have never been greater.
Cybersecurity breaches in manufacturing are no
Read More
From Ransomware to IP Theft: Understanding Cyber Risks in Manufacturing
We all know the manufacturing industry is a powerhouse, driving economic growth and innovation. But did you know it's also a prime target for cyber attacks? Yes, cybercriminals are increasingly setting their sights on manufacturers, and for good reasons.
In today’s tech-driven world, the manufacturing industry is the backbone of our global economy. But with great power comes great responsibility—and great risk. The very technology that propels our fa
Read More
SMBs vs. Ransomware: How to Prevent Attacks and Regain Customer Trust
In the world of small and medium-sized businesses (SMBs), cybersecurity can often feel like an overwhelming task reserved for large corporations with dedicated IT departments. Yet, the stark reality is that SMBs are prime targets for ransomware attacks. The increasing frequency and sophistication of these attacks make it crucial for businesses of all sizes to fortify their defences and prepare for potential breaches. So, how can you protect your SMB from ransomware, and what steps should you
Read More
Streamline Security: The Cyber Due Diligence Checklist You Need
In today's digitally driven world, cybersecurity due diligence has become a cornerstone for organizations seeking to safeguard their assets and mitigate risks effectively. Whether you're gearing up for an M&A transaction or simply aiming to enhance your cybersecurity posture, thorough preparation is key. To help you navigate this critical process, we've compiled a comprehensive checklist of essential steps to ensure your organization is ready to undergo cybersecurity due dilig
Read More
Crack the Code: Your Complete Cyber Due Diligence Handbook
In today's digital landscape, where cyber threats lurk around every corner, the need for robust cybersecurity measures has never been more critical. Whether you're contemplating a merger or acquisition, or simply aiming to fortify your organization's defenses, conducting cybersecurity due diligence is paramount. This comprehensive guide will walk you through the step-by-step process of preparing for and performing cybersecurity due diligence, ensuring that your organization stays
Read More
IT Vs. Cyber Due Diligence: Simplified For You
In the digital realm where every byte of data holds immense value, the concept of due diligence emerges as the sentinel guarding the gates of technological fortresses. As stewards of information security, it's crucial to discern the nuances between IT due diligence and cybersecurity due diligence, for within these distinctions lie the keys to resilience and preparedness.
In the labyrinth of digital landscapes, due diligence stands as the bastion
Read More
Safeguarding Data Integrity in the Digital Age: Ensuring compliance with DPDP
In an era defined by unprecedented technological advancement and digital interconnectedness, the protection of personal data has emerged as a paramount concern for individuals, businesses, and governments alike. As the custodians of vast troves of sensitive information, organisations find themselves at the nexus of this data-driven revolution, grappling with the dual imperatives of innovation and responsibility. At the heart of this paradigm shift lies the Data Privacy and Personal Data Prote
Read More
A Comprehensive Guide to Implementing the DPDP Act for Data Privacy in India
In response to the growing concerns surrounding data privacy and security in the digital age, India introduced the Data Privacy and Personal Data Protection (DPDP) Act. This landmark legislation aims to regulate the collection, processing, storage, and transfer of personal data in India, thereby ensuring the protection of individuals' privacy rights in the digital ecosystem.
The importance of the DPDP Act cannot be overstated in today's interconnected world,
Read More
8 Reasons Why Penetration testing is Important for Every Business
Cybersecurity is not a choice anymore but a necessity for all sorts of organisations, even if you run a not-for-profit organisation. Getting the name of your organisation in the news for the wrong reasons may create serious repercussions for the business. So how do we secure the business and what can we do to prevent the ever increasing cyber threat? Begin with cybersecurity!
While planning cybersecurity, penetration testing plays a crucial role as without knowing t
Read More
Why Cyber Hygiene is important for every business?
Have you heard of something called cyber hygiene lately? Cyber hygiene refers to fundamental cybersecurity best practices that an organisation's security practitioners and users can undertake in order to improve online security. These practices are generally part of a routine ensuring identity and data security. Similar to other regular practices, cyber hygiene is regularly conducted to assure safety from common threats.
Why is cyber hyg Read More

Important things to know about HIPAA Compliance
Healthcare information is always sensitive. These details often contain the family's medical history and financial information making it more critical. This made it important for introducing Health Insurance Portability and Accountability Act (HIPAA).
HIPAA Compliance as defined is adherence to the physical, administrative and technical safeguards outlined in HIPAA, which covered entities and business associates must uphold to protect the integrity of Protected
Read More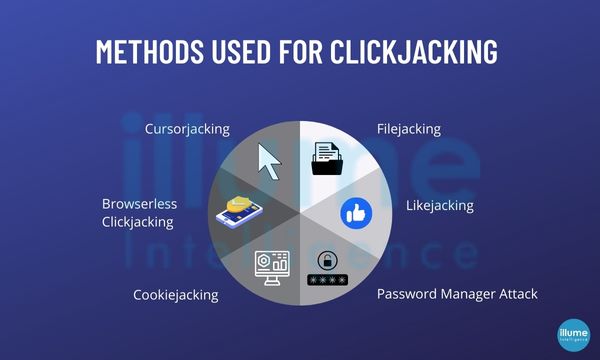
What is clickjacking and how to protect your business from it?
Bigger or smaller ignoring any threat is not advisable in today's highly challenging time. Clickjacking has never been considered a big threat by most businesses over time.
Researchers have found that not every organisation considers clickjacking a severe security threat. But it can harm businesses. In many instances unknowingly the employee who clicks on the false link can open a chain of vulnerabilities for the organisation. Major industry giants like Tw
Read More
Why Web Application Penetration Testing Is Important For Software security?
With the increased online presence of businesses, the need to secure Web Applications has taken a toll. Web Application Penetration Testing has emerged as an important tool for this.
There have been massive attacks on the organisations causing them to lose billions. Statistics have shown, that around 99% of businesses have at least one undiscovered vulnerability. These security issues are the ticking bomb that can blast anytime. Compromising on cybe
Read More
Why ignoring cybersecurity audits can never be healthy for your business?
Are you thinking, if you need a cybersecurity audit for your business? Or maybe you implemented a cybersecurity audit sometime back, you don't remember. With the increasing cyber incidents globally no business is safe online.
According to Gartner's report, 41% of employees that went remote due to the pandemic want to continue to work from home. These kinds of changes in the global workforce also increase the challenges in implementing security policies. Regu
Read More
Cyber security in India: How India is responding to the growing challenge?
India is among the top 3 most affected nations in Asia. India witnessed three times more cyber attacks in 2020 than in 2019. More than 11.5 lakh incidents of cyberattacks were tracked and reported to India’s Computer Emergency Response Team (CERT-In) in 2021. Ransomware attacks have increased by 120% in India as per official estimates.
Not only big businesses but SMBs and startups have also fallen victim to cyberattacks. Online grocery s
Read More
How to protect your business against ransomware attacks in an effective way?
Ransomware is becoming the biggest nightmare for all organisations with the increasing number of attacks amid the pandemic. Cyberattacks have become quite common and all countries whether big or small are falling victim to them. Power companies, oil and gas majors, telecom vendors, educational institutes, universities, retail chains, restaurant chains, transportation, hospitals and even diagnostic labs have been victims of cyberattacks.
In this glo
Read More
How businesses can meet the challenges of Cyber security in Kerala?
Cyber security in Kerala is alarming as according to the police records, one cybercrime is recorded every two hours in the State of Kerala. The sudden outbreak and spread of the pandemic have left everyone in a state of panic and chaos, providing the best time for the threat actors to exploit this fear of humans.
The hackers drafted the attacks aiming to compromise computers and devices to gain access to users' confidential data, banking details and cryptocurren
Read MoreSearch Here


