Preventing against Human hacking
Humans are the weakest links in any security strategy. Understanding the security exposure in any organisation is very important to prevent possible social engineering attacks. Human beings are very unpredictable, depending upon the circumstances they are in. The security professional needs to design the security assessment accordingly.
Social engineering is the usage of manipulation techniques by the threat actors exploiting human error and gaining access to private information, spreading malware, ransomware etc. These attacks can be done online, in-person and in other ways.
Social engineering assessment or employee vulnerability assessment comes into the picture to prevent social engineering attacks. Social engineering is dangerous because it is not the vulnerabilities in applications or systems. Mistakes or access given through legitimate users are less predictable. Social engineering simulation is a simulated test aiming to measure the information security awareness levels of the organisation's employees by exploiting the natural behaviour (trust, friendliness, assumptions, biases etc) of the employees.
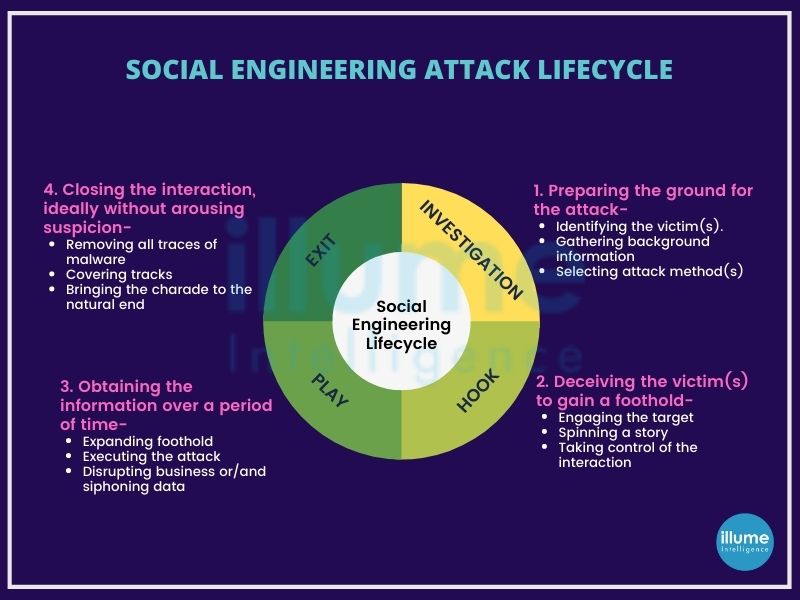
How is social engineering assessment or Employee Vulnerability Assessment done?
The team assessing the system attempts direct contact with the targeted employees, either through phone calls or in-person or through restricted access.
The assessment employs psychological manipulation for deceiving people into performing adverse actions like clicking on fabricated links, opening infected attachments, sharing personal details or divulging confidential information. The social engineering team develops familiar-looking fabricated content to lure the users and then make them take unwarranted actions.
We assist in assessing the ability of the organisation's system and employees to detect social engineering attacks. The assessment is conducted in close coordination with the concerned person in a controlled manner. The assessment may involve following steps:
1. Gathering Information - The assessment team researches the target organization to understand its structure, employees, and security policies.
2. Crafting Attack Scenarios - Our team creates scenarios that mimic real social engineering attacks, such as phishing emails, phone calls, or physical attempts.
3. Executing Simulated Attacks - The team performs the social engineering attacks on employees, monitoring their responses and actions.
4. Analyzing Results - The results of the assessment are analyzed to identify weaknesses and areas of improvement.
5. Providing Recommendations - The assessment report includes recommendations for strengthening the organization's defenses and enhancing employee awareness.
A detailed report on the analysis along with suggestions to improve the security of an organisation is provided after the assessment.
How to prevent social engineering attacks?
One can not guarantee the prevention of social engineering, but some precautions can help in strengthening the organisation's security system against social engineering attacks.
1. Don't open attachments or emails from unknown or suspicious sources.
2. Usage of multifactor authentication can help in avoiding unauthorised access.
3. Be careful with tempting offers. Hackers spoof the sender to make the message look real and offer tempting deals.
4. Antivirus or antimalware software should always be up to date.







