Ensuring secure applications for your business through VAPT assessment
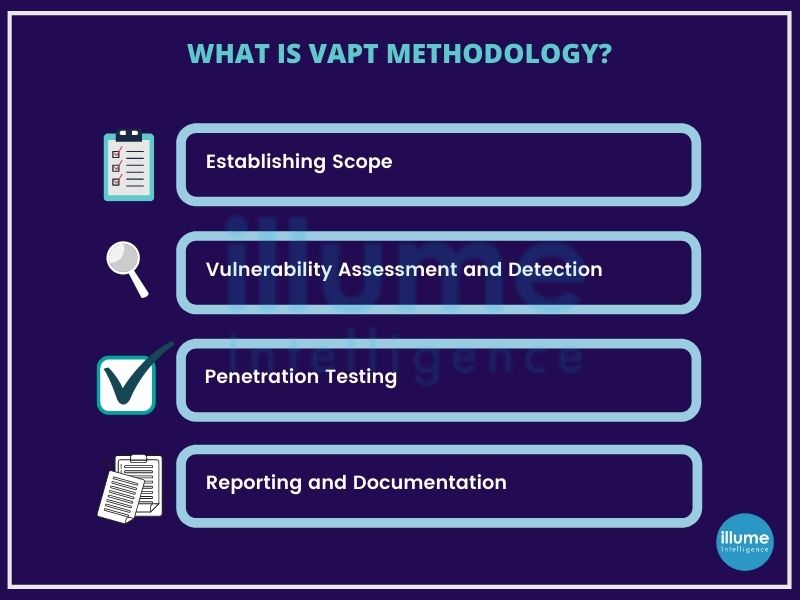
Vulnerability assessment and penetration testing a.k.a VAPT is a combination of Vulnerability assessment and penetration testing. This combination gives any organisation a better identification, classification and mitigation of the vulnerabilities present in the system and applications.
Vulnerability Assessment is focused to find the internal flaws present in the organisation’s system that may arise due to frequent changes made in the applications or due to the firewall default settings or other network settings. That’s the reason this needs to be regularly scanned and addressed.
Penetration testing aims at identifying the flaws in the system and exploiting them like a real-world hacker but in a controlled way, giving insight to the organisation on the vulnerabilities of their system. This testing is advised to be done at least annually for securing the system. The exposed flaws can be mitigated to strengthen the system, saving it from external cyber threats.
What is the necessity for Vulnerability Assessment & Penetration Testing (VAPT)?
Cyber attacks and threats are becoming nightmares for organisations these days, with thousands of websites and networks being compromised every day. Some of the reasons that make conducting Vulnerability Assessment & Penetration Testing (VAPT) in any organisation important are-
1. Keeping the data secure while in transition over the network.
2. Protecting the user data.
3. Identifying the security vulnerabilities within the system.
4. Detecting loopholes and flaws in the system.
5. Accessing the tolerance of the business against cyber attacks.
6. Implementing an effective security strategy in the organisation.
Protecting your data and resources before the attack is the idea behind conducting Vulnerability Assessment & Penetration Testing (VAPT). Every organisation is spending on security to stay away from cyber attacks.
Depending upon the requirements of the various industries, Vulnerability Assessment & Penetration Testing (VAPT) is mandatory across many industries as some compliance standards require VAPT at regular intervals. A list of such compliances are -
ISO 27002 / ISO 27001
PCI DSS – Payment Card Industry Data Security Standard
SOX – Sarbanes-Oxley Act
HIPAA – Health Insurance Portability and Accountability Act
TRAI – Telecom Regulatory Authority of India
DOT – Department of Telecommunication
CERT-In – Cyber Emergency Response Team of India
GLBA – The Gramm–Leach–Bliley Act
FISMA – The Federal Information Security Management Act
NIST – National Institute of Standards and Technology
SAS 70 – Statement on Auditing Standards
COBIT – Control Objectives for Information and Related Technology
Knowing how much vulnerable your organisation is always better than assuming the vulnerabilities, as then only one can take necessary preventive measures. If you are looking to fix your organisation's vulnerabilities we can help.







