Know the vulnerabilities in your network security
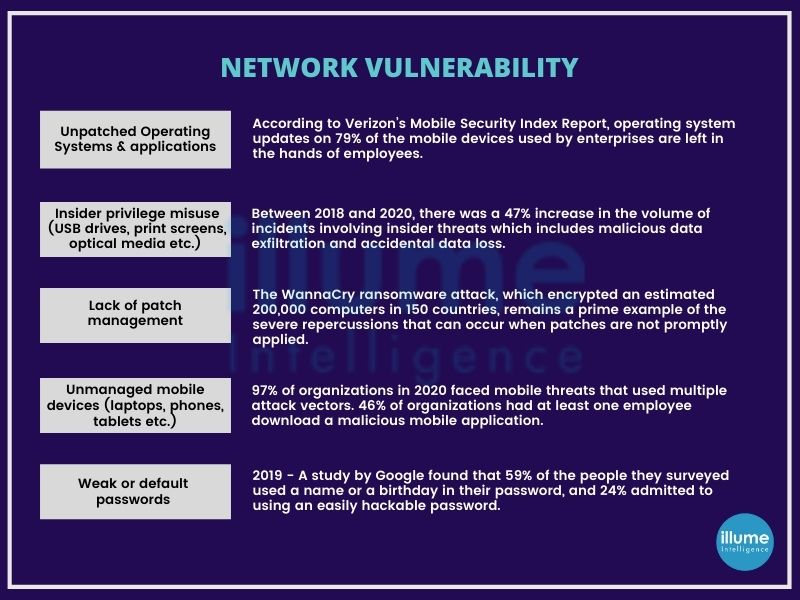
A network security assessment is an audit designed to seek vulnerabilities in any network. A network with weak security can be compromised easily resulting in harming the business operations and leaking sensitive data. The vulnerabilities can be due to old software, viruses, malware or coding flaws in applications.
securing the network should be the top priority of any organisation. It's obligatory to carry out vulnerability assessments to comply with compliance and regulatory standards like HIPAA, PCI DSS etc.
Network VAPT assessment helps in identifying vulnerabilities lying in the physical layer and network design of the infrastructure. It is capable of finding the loopholes and the vulnerabilities caused so that the experts can remediate them quickly before being exploited by the threat actors.
Network Vulnerability Assessment helps in finding security flaws from both inside and outside the network whereas Penetration Testing looks for the vulnerabilities that can be exploited to gain access to the network.
What are the goals of the Network Security Assessment?
1. Determine the ability of attack vectors.
2. Identifying the low-risk vulnerabilities could be exploited to impact more.
3. Identifying flaws that are hard to be tracked by vulnerability scanning software.
4. Auditing and analysing the impact of attacks if successful, from inside and outside the network.
5. Testing the capacity of network defenders to detect and respond.
How do we perform a Network vulnerability assessment?
We perform internal and external network penetration testing using network vulnerability assessment with the black box and grey box testing. While auditing external and internal network testing are very important to make the system foolproof.
1. Assessment scope - Depending upon the requirements we outline the assets, services, devices and IP addresses for scanning.
2. Information gathering - Gathering information on all possible assets using the open-source tools.
3. Scanning for vulnerabilities - scanning the target with the manually tuned automated scanning tools.
4. Analysis - Analysing the findings for filtering false positives and assigning priorities with the severity of the impact.
5. Reporting - Comprehensive report on the methods employed, findings, remediations and mitigations according to the findings.
We suggest performing network vulnerability assessment and penetration testing every 3 months (monthly in case of regulations) and each time after introducing changes into the network.
Stay ahead of the emerging security threats and keep your data protected without wasting your money. Our team of experts can help in securing your network.







