Cybersecurity Due Diligence: Fortify Your Digital Perimeter with Expert Precision.
In today's highly interconnected and rapidly evolving business landscape, the protection of sensitive data and digital assets is paramount. As organizations engage in mergers, acquisitions, partnerships, and other strategic transactions, the risks associated with cybersecurity breaches loom larger than ever before. In this context, robust cybersecurity due diligence emerges as an indispensable safeguard, ensuring that organizations navigate the intricate web of digital risks with confidence and resilience.
What is Cybersecurity Due Diligence?
Cybersecurity due diligence is a critical process aimed at identifying, assessing, and mitigating cyber risks within an organization's network ecosystem. It involves thoroughly examining the governance, processes, and controls utilized to safeguard information assets. This evaluation extends beyond the organization itself to include third-party vendors and external stakeholders, such as partners and suppliers.
During cybersecurity due diligence, comprehensive insights are gathered into the cybersecurity posture of third-party vendors, as well as the efforts undertaken by internal security teams. This allows clients to gain a deeper understanding of potential vulnerabilities and cybersecurity risks associated with their business relationships.
In the context of mergers and acquisitions, cybersecurity due diligence plays a pivotal role in uncovering any issues that may impact the deal's terms, conditions, or overall valuation. By conducting a thorough assessment, organizations can identify and address potential risks proactively, ensuring compliance and minimizing the impact of cyber threats.
Ultimately, cybersecurity due diligence serves as a proactive measure to safeguard against cyber risks and enhance overall security resilience. By conducting due diligence assessments, organizations can strengthen their cybersecurity posture, protect sensitive information, and mitigate potential threats effectively.
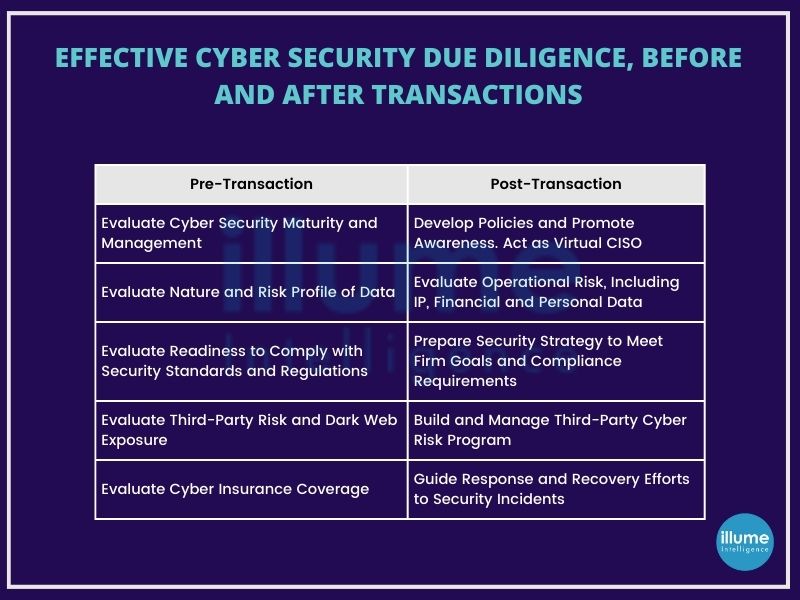
Importance of Cyber Due Diligence
Cybersecurity due diligence offers organizations unparalleled insights into potential risks and vulnerabilities. Let's delve deeper into why cybersecurity due diligence matters:
1. Comprehensive Risk Assessment: By conducting cybersecurity due diligence, organizations gain a comprehensive understanding of potential risks associated with mergers, acquisitions, or partnerships. This assessment allows for the identification of any issues that could impact the terms or structure of a deal, enabling informed decision-making and risk mitigation strategies.
2. Third-Party Risk Management: Cybersecurity due diligence provides a detailed examination of third-party vendors' security networks, vulnerabilities, and threats. This scrutiny allows organizations to assess the viability of business relationships and implement measures to mitigate associated risks effectively.
3. Enhanced Cyber Threat Awareness: Through cyber due diligence, organizations gain valuable insights into the cyber threat landscape, enabling proactive measures to address emerging threats and vulnerabilities. This heightened awareness empowers organizations to stay ahead of potential cyber-attacks and safeguard critical assets.
4. Cybersecurity Risk Ratings: Leveraging cybersecurity risk ratings enables organizations to better manage cyber risk associated with third-party relationships and supply chain partnerships. These ratings provide transparency and assist in assessing, calculating, and managing security risks effectively, particularly during periods of business growth or investment.
5. Continuous Monitoring and Mitigation: It facilitates continuous monitoring of cyber risk and allows organizations to evaluate performance over the short and long term. Through prompt alerts and data-driven insights, organizations can identify and address security issues swiftly, ensuring ongoing protection against evolving threats.
6. Data Privacy and Compliance Assurance: Helps organizations understand the complexities of data privacy policies and security protocols followed by target companies. This ensures compliance with regulatory requirements and reinforces trust with stakeholders by demonstrating a commitment to safeguarding sensitive information.
In essence, cybersecurity due diligence serves as a cornerstone in safeguarding organizational assets, reputation, and resilience in the face of evolving cyber threats. By conducting thorough assessments and implementing proactive measures, organizations can navigate the digital landscape with confidence and fortify their cybersecurity posture for long-term success.
Who needs cyber due diligence?
Cyber due diligence is essential for various entities and scenarios, including:
1. Mergers and Acquisitions (M&A): Both acquiring and target companies in M&A transactions need cyber due diligence to assess the cybersecurity posture of the target company. This helps in identifying potential risks, liabilities, and vulnerabilities associated with the acquisition.
2. Investors and Venture Capitalists: Investors and venture capitalists conducting due diligence before investing in a company need to evaluate its cybersecurity measures. This ensures that their investment is protected against cyber threats and potential data breaches.
3. Startups and Small Businesses: Startups and small businesses often undergo cyber due diligence when partnering with larger corporations, entering into contracts, or seeking funding. It helps them demonstrate their commitment to cybersecurity and enhances their credibility.
4. Government Agencies and Contractors: Government agencies and contractors handling sensitive data or providing critical infrastructure services are subject to cyber due diligence to comply with regulatory requirements and safeguard national security interests.
5. Service Providers and Vendors: Service providers and vendors offering software, IT services, or cloud solutions may undergo cyber due diligence as part of their clients' vendor management processes. This ensures that they meet cybersecurity standards and protect clients' data.
6. Compliance and Regulatory Requirements: Companies operating in regulated industries such as finance, healthcare, and telecommunications are required to undergo cyber due diligence to comply with industry-specific regulations and standards.
Overall, any organization that handles sensitive data, relies on digital infrastructure or is involved in transactions where cybersecurity is a concern can benefit from cyber due diligence. It helps identify and mitigate risks, protects assets and data, and enhances trust and confidence among stakeholders.
Illume Intelligence’s Approach to Cyber Due Diligence
As pioneers in providing due diligence services, we've honed our approach to cybersecurity and data privacy assessments. Our methodology encompasses the following key steps:
1. Phased Evaluation and Risk Assessment:
-
We conduct a phased evaluation of the target company's cybersecurity posture, systematically assessing governance structures, operational practices, and technological infrastructure. This comprehensive approach ensures a thorough understanding of potential risks.
2. Risk Calculation:
-
Our experts meticulously calculate the risks identified during the evaluation process, considering factors such as the likelihood of occurrence and potential impact on your organization. This quantitative analysis provides clarity on the severity of each risk and informs decision-making.
3. Development of Risk-Handling Mechanisms:
-
Based on our findings, we collaborate with your team to develop tailored risk-handling mechanisms. Whether it's implementing mitigating controls, negotiating terms, or allocating resources for remediation, we guide you through the process to effectively manage cyber risks.
With our cybersecurity due diligence services, you can approach mergers, acquisitions, and partnerships with confidence, knowing that your investments are protected and your organization is equipped to navigate the complexities of the digital landscape.
Here's how our comprehensive approach can benefit your organization
1. Identifying Information Security Risks:
-
Our meticulous assessment uncovers any vulnerabilities or shortcomings in governance, operations, and technology within the target company. By identifying these risks upfront, we empower you to make informed decisions and mitigate potential threats.
2. Researching Undisclosed Data Breaches:
-
Our experts delve into the target company's cybersecurity history to uncover any undisclosed or unknown data breaches. This proactive approach enables you to address any hidden issues before they escalate into costly post-transaction risks.
3. Assessing Incident Response Capabilities:
-
We evaluate the target company's ability to detect and respond to cybersecurity incidents promptly. This assessment provides insights into the effectiveness of their incident response procedures and helps you gauge their readiness to handle cyber threats.
4. Quantifying Remediation Costs:
-
Leveraging our expertise, we quantify potential remediation costs from various perspectives, including operational, financial, and reputational. By understanding the full scope of potential exposures, you can make informed decisions and allocate resources strategically.
In an era defined by relentless innovation and unparalleled connectivity, the need for proactive cybersecurity diligence has never been greater. Whether navigating complex mergers, acquisitions, or strategic partnerships or simply seeking to fortify cybersecurity defences against emerging threats, our Cybersecurity Due Diligence Services offer peace of mind and confidence in an uncertain world.
Cyber Due Diligence Service Modules
Unlock comprehensive insights and mitigate information security risks with our tailored cyber due diligence service modules. We offer four distinct modules designed to empower you in uncovering, assessing, and addressing cybersecurity risks, both pre-and post-transaction. Each module is fully customizable to suit the unique requirements of your transaction. You have the flexibility to select and deploy the combination of services that best aligns with your risk concerns, transaction timelines, and access levels to the target company.
For organizations embarking on acquisitions, positive findings or swift remediation actions resulting from our assessments, particularly Modules 3 and 4, can serve to assuage potential buyers' concerns and expedite the closure of deals.
Implement NIST framework to Improve the organisational Critical Infrastructure along with all-time cyber threats protection
Cyber attacks have become a nightmare for businesses of all sizes. According to the researchers, cyberattacks cost businesses billions of dollars every year and these attacks are increasing in frequency and sophistication.
Strengthening organisational security with the frameworks is not a new concept for cybersecurity professionals. NIST is one of the most commonly accepted global cybersecurity frameworks that offer immense benefits with effective application among varied industries.
What is NIST?
NIST known as the National Institute of Standards and Technology, is a non-regulatory government agency that promotes U.S. innovation and industrial competitiveness by advancing measurement science, standards and technology, all with a goal of greater economic security.
The NIST sets the standards and best practices for handling and securing data within government organisations and their contractors. These requirements help public and private sector organisations alike to plan comprehensive security programs with robust controls that ensure systems and data protection.
The most commonly used cybersecurity frameworks are -
- NIST Cybersecurity Framework (CSF)
- NIST 800-53
- NIST 800-171
The directions and cybersecurity approach provided by NIST can be easily applied to almost any sector and any business size. The NIST compliance strengthens the organisation's security posture and improves resilience. Adopting these guidelines helps in keeping the systems protected from breach along with ensuring compliance with other mandatory regulations like HIPAA and FISMA. Implementing NIST compliance may not be mandatory but this acts as a best practice standard for cybersecurity and data protection. It also provides a competitive advantage to the organisation.
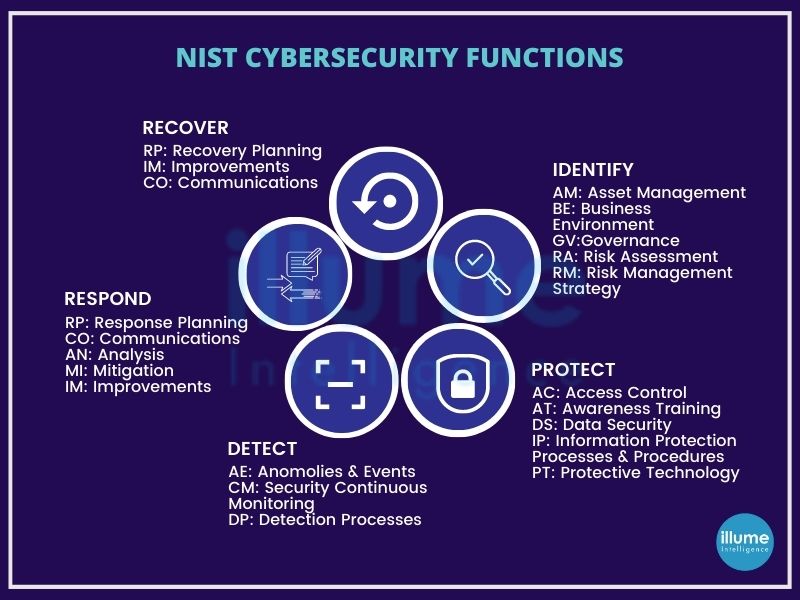
The NIST Framework
The NIST Cybersecurity Framework provides guidance for organisations to improve security risk management. It is widely considered the gold standard for building cybersecurity programs. The scalability and customisation make it flexible for implementation at any level across various industries.
The NIST framework comprises three main components -
* Framework Core
* Implementation Tiers
* Profiles
Framework Core - It is a set of cybersecurity activities, desired outcomes and applicable references that are common across critical infrastructure sectors. It comprises five functions - Identity, Protect, Detect, Respond and Recover.
Implementation Tiers - These describe the level of the organisation's cybersecurity risk management practice. These vary over a range from Partial (Tier 1) to Adaptive (Tier 4).
Profile - This represents the core functions categories and subcategories prioritized based on the business needs which are being used to measure the organisation's progress towards the target profile.
Why NIST?
The NIST framework provides an organisation with a list of guidelines and principles that are utilised to improve cybersecurity efforts. The framework provides an easy customisation of the cybersecurity strategy. It is precise and strict enough while providing the flexibility to manage risks in the most effective manner. NIST defines a four-step process for incident response mentioning it as a cyclical activity, as a process of continuous learning and improvement to discover a defence against cyber attacks. The four steps are
1. Preparation - This involves performing an inventory of IT infrastructure. Evaluating the importance of IT assets. Creating a policy for monitoring activities and a guide for incident handling.
2. Detection & Analysis - Data collection from IT systems, security tools, publicly available information etc and identifying incident signs that may happen in future.
3. Containment, Eradication and Recovery - This is for limiting the impact of a security incident. Eradicating the threat, restoring systems and recovering normal operations as quickly as possible with steps to ensure the attack happens again.
4. Post-Incident Activity - Security teams need to understand what went wrong, what needs to be changed, how can we do better and so on. This is required for strengthening the security policy and handling security incidents in future.
Approach NIST Cyber Risk Assessment with Illume
The NIST Risk Assessment aims at simplifying cybersecurity compliance but following all the outlined protocols can be complicated. Hence managed cybersecurity services provided by organisations such as Illume comes in handy to streamline the steps and ensure the proper applications of standards and guidelines. We understand the requirements of the organisations and know how to implement the steps outlined to secure the Infra and people against cyber threats. Our application of the latest outlined practices helps in easing the compliance journey.
Comply with the standards and implementation specifications of the HIPAA Privacy, Security, and Breach Notification Rules to secure your business
In 2022 alone, Healthcare companies would have paid over 2 million $ in penalties following HIPAA non-compliance. HIPAA and Compliance are very common in the healthcare industry. HIPAA known as Health Insurance Portability and Accountability Act is all about protecting patient privacy. This government act was created to keep patient data safe. It also ensures that businesses were protected against powerful lawsuits that can destroy their operations. The HIPAA applies to healthcare providers, health plans, and healthcare clearinghouses that conduct transactions electronically (referred to as covered entities). It is also applicable to business associates, subcontractors, researchers and hybrid entities that perform functions on behalf of HIPAA-covered entities that give them access to protected health information (PHI). For more details refer to Introduction to HIPAA Compliance Ignoring HIPAA regulations can be very expensive not only in terms of finances. Illume Intelligence India Pvt. Ltd. helps to ensure the organisation is always on the right side of the law. Streamlining the entire compliance journey by breaking all the HIPAA requirements into simple easy-to-understand steps making it easy to understand and implement
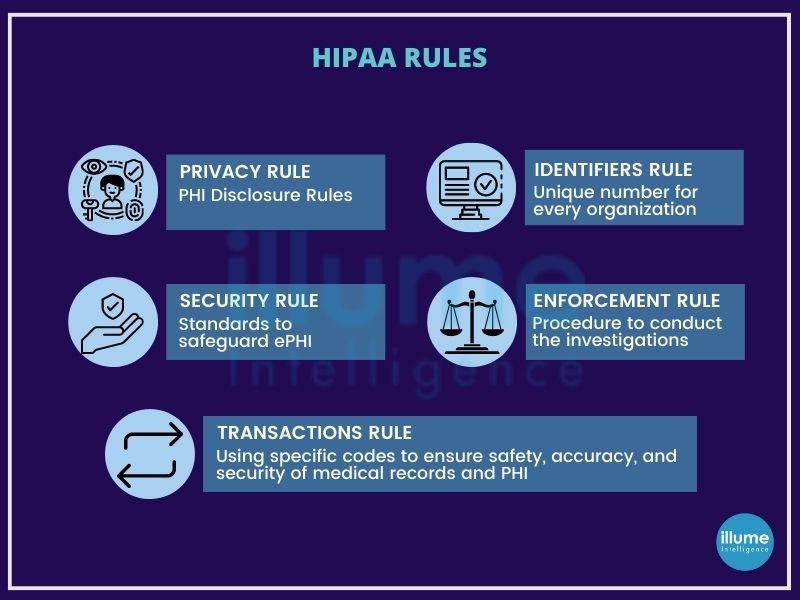
HIPAA Compliance
With digitisation, all organisations are moving towards computerised operations. This includes computerised physician order entry (CPOE) systems, electronic health records (EHR), radiology, pharmacy, laboratory systems and more. With the increased efficiency and mobility, the security risk has also increased making HIPAA compliance more important.
There are physical and technical safeguards mentioned by the relevant authorities that must be followed by the entities hosting sensitive patient data. Some of these are
1. Limited facility access and control with authorised access in place.
2. Policies about the use and access to workstations and electronic media.
3. Restrictions for transferring, removing, disposing, and re-using electronic media and ePHI.
4. Using unique user IDs.
5. Emergency access procedures.
6. Automatic log off.
7. Encryption and decryption.
8. Audit reports or tracking logs that record activity on hardware and software.
and more
It is universally understood that data is exposed only through the people in a way that is negligence, malicious intent, or outside attack and hence effective compliance focus on people.
The Seven Elements of Effective Compliance
There are seven elements created for the effectiveness of the compliance program. These are the absolute minimum requirements that the effective compliance program must address.
1. Implementing written policies, procedures, and standards of conduct.
2. Designating a compliance officer and compliance committee.
3. Conducting effective training and education.
4. Developing effective lines of communication.
5. Conducting internal monitoring and auditing.
6. Enforcing standards through well-publicised disciplinary guidelines.
7. Responding promptly to detected offences and undertaking corrective action.
The organisation's compliance program is tested against these seven elements to judge its effectiveness.
What is HIPAA Violation?
A HIPAA violation is any breach in an organisation's compliance program that compromises the integrity of PHI or ePHI. It is different from a data breach. All data breaches are not HIPAA violations until it results from an ineffective, incomplete, or outdated HIPAA compliance program or a direct violation of an organization’s HIPAA policies.
Some common causes of HIPAA violations and fines are
* Stolen laptop
* Stolen phone
* Stolen USB device
* Malware incident
* Ransomware attack
* Hacking
* Business associate breach
* EHR breach
* Office break-in
* Sending PHI to the wrong patient/contact
* Discussing PHI outside of the office
* Social media posts
These HIPAA violations commonly fall into several categories:
*Use and disclosure
* Improper security safeguards
* The Minimum Necessary Rule
* Access controls
* Notice of Privacy Practices
Assuring Applications reliability by Integrating security into the design to delivery phases of the Software Development Life Cycle
Software and applications play an important role in business these days. Businesses use these for their daily operations and customer dealing. The slightest miss in the security can bring a mountain of miseries to the business.
Secure SDLC (Software Development Life Cycle) or SSDLC process takes care of the entire software development life cycle with the security protocol keeping the system protected from internal and external threats.
What is SSDLC?
SSDLC (Secure Software Development Life Cycle) is a process framework used by organisations to build secure applications. This defines the integration of security into the SDLC.
Earlier the organisations used to do the security tests only as a part of testing at the end of the SDLC. Resulting in the late finding of the bugs that may delay the timeline to deliver the application. This leads to incomplete findings of the bugs, flaws and vulnerabilities.
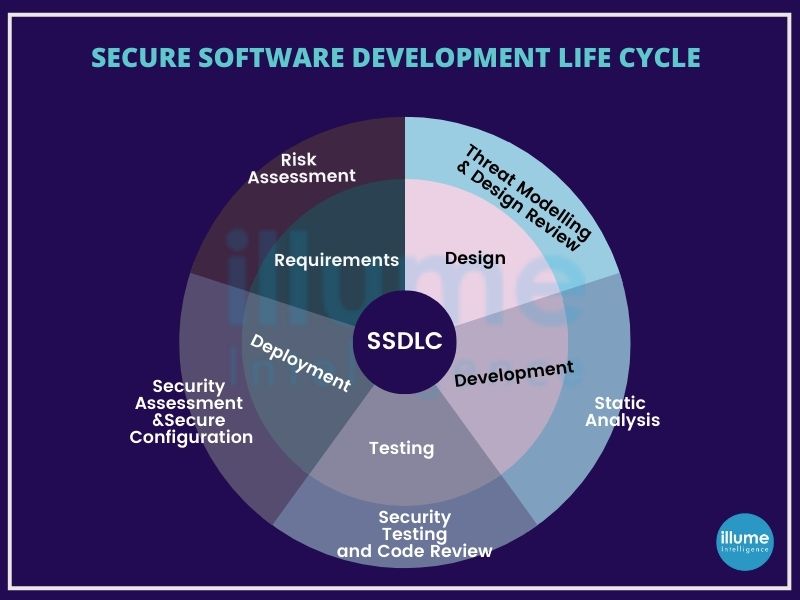
How does SSDLC work?
Secure SDLC involves integrating security testing and gap analysis into the existing development process. Examples may include ensuring the security of architecture while designing architecture and including security risk factors in the initial planning phase.
Secure SDLC is not intended to completely eliminate traditional security checks but to include security in the scope of developer responsibilities and help them to build secure applications from the beginning.
Security is added to each phase of the SDLC to ensure the security of an overall application. It is done by adding security needs in every stage to ensure that the entire team takes security seriously from the beginning.
Conducting Gap Analysis is important for the assessment of the defined areas of concern and security deficiencies to get the outcome flawless.
Why Is Secure SDLC Important for your organisation?
According to the researchers, it is six times costlier to fix the bug during implementation rather than a bug found in the design phase. According to IBM the cost of fixing bugs during the testing phase is 15 times more than fixing them in the design phase.
Implementing the security testing across the SDLC will help in the early detection of vulnerabilities. Activities like Architecture Analysis, Code Review and Penetration Testing are included in the SDLC to make it secure giving the following advantages to the organisation.
1. Secure Application - The delivered software is more secure as the security is monitored at every stage.
2. Early detection - Resolving of the bugs at the moment they are located in the SDLC itself.
3. Trust in Application - Clients and Stakeholders will have more trust in the business
4. Reduced Cost - As the flaws are fixed in the initial stages the cost is also saved.
5. Reduced Risk - The application is secure from external and internal business risks
Manual or Automated Security Testing?
When it comes to testing, many teams rely on Automation for quick and accurate bug findings. These tools succeed to some extent but in critical situations, only the experienced tester can locate the issues.
Whereas on the other hand manual testing is accurate, effective, and validates but the time and investments are too high.
It is always advisable to combine both Security tests and use them effectively.
How can I get started?
The SSDLC can be inculcated in any development process in two ways
A. Training an Internal Team
1. Educate your team on following the best secure coding practices and available frameworks for security
2. Perform architecture risk analysis at the beginning
3. Consider security in all the phases
4. Use code-scanning tools
B. Get Help from the Outside
You can always avail the help of professionals as many organisations are offering the SSDLC as a Service. You will get a complete team of professionals that will work with your internal team to make your project a success.
Are you still confused about how to proceed with the security of your Application development? You can always consult Illume Intelligence’s professionals to get insights and support on streamlining your SSDLC.
Govern your Security Policies easily with the Security Operations Center
Expanding the Internet has given global access to business but it has also come with security problems as well. Cybersecurity breaches are no longer restricted to big organisations, they are happening everywhere. Irrespective of the organisation's size or type, it is essential for all to ensure a defence system. According to a survey around 77% of companies have increased their cybersecurity Budget.
Many organisations find it difficult to achieve complete threat visibility lacking siloed security log management, costly and ever-expanding infrastructure changes and the non-availability of specialised staff. It is a time to work on advanced security events and infrastructure management. It is important to rethink the security designs for implementing the right security policy and security incident detection.
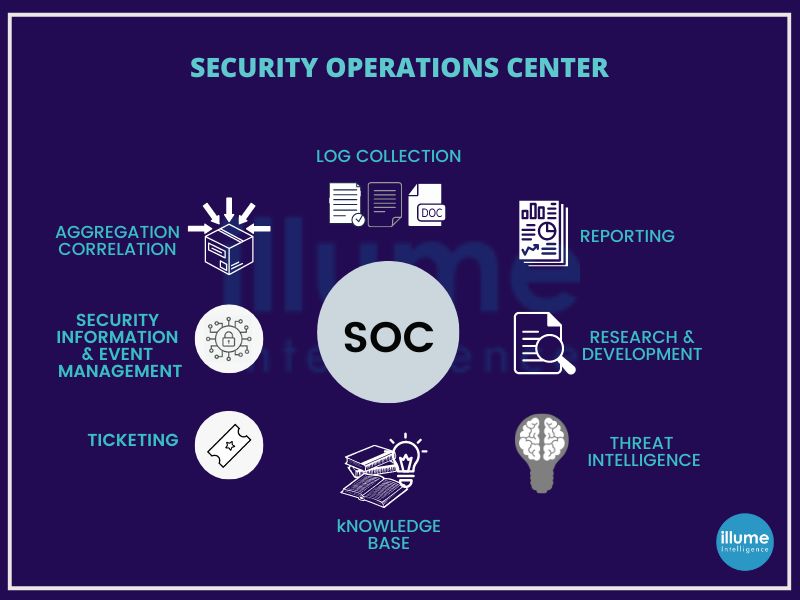
What is Security Operations Center (SOC)?
A Security Operations Center (SOC) is an in-house or outsourced team of IT Security Professionals for monitoring the organisation's entire IT infrastructure. This team works 24*7 for real-time detection of cybersecurity events to address them quickly and effectively.
The SOC team works closely with the incident response team to ensure quick addressing of the issues as and when detected. Security operations centres monitor and analyse network activities, servers, databases, devices and other connected systems for anonymous activities. SOC helps in operating and maintaining the cybersecurity of the organisation by continuous threat detection and data analysis for finding ways to strengthen the organisation's security posture.
The major benefit of SOC is that it ensures the identification, analysis, defence, investigation and reporting of all potential security incidents. To begin with, it is important to have a strong strategy, followed by the implementation of required infrastructural support like firewalls, IPS/IDS, breach detection solutions, probes, security information, event management (SIEM) systems etc.
How Security Operations Center (SOC) works
1. Recording - Making a record of available resources for preparation under the scope of the organisation's infrastructure.
2. Preparation and preventative maintenance - Preparation and preventative maintenance by regularly updating the existing systems, updating the firewall policies, patching vulnerabilities and whitelisting, blacklisting and securing applications.
3. Monitoring - Continuous proactive monitoring for detecting abnormalities or suspicious activities.
4. Alert handling - Alert ranking and management for prioritising the issues and their handling.
5. Early detection and defensive action - Quick response to the detected threats by performing actions like isolating endpoints, and terminating the harmful process.
6. Restoring - Restoring and recovering the compromised systems and data, including wiping and restarting endpoints, reconfiguring systems or, in the case of ransomware attacks, deploying viable backups in order to circumvent the ransomware.
7. Log management - Log Maintaining includes collecting, maintaining, and regularly reviewing the log of all network activity and communications for the entire organization.
8. Investigating - Investigating the root cause to figure out what and how it happened.
9. Futuristive approach - Security refinement and improvement on the basis of the findings to protect the future mishaps
10. Compliance ready - Getting the system always ready for compliance-ready by providing all the audits and other reports.
Illume Intelligence's SOC as a Service empowers your organisation by providing complete visibility within the infrastructure. Identifying hidden risks and implementing the security strategy so that you focus on your business. A complete record of the important security logs for helping in building a compliance-ready secure environment trusted by the employees and the clients
In the era of soaring cyber crimes, Ethical Hacking will work as a tool to safeguard your organisation's security
Amid the increasing online crimes and data theft, every organisation must protect against cybercrimes, irrespective of their size. Smaller companies often fall into the trap of threat actors as they think they don't have much to secure or they don't have a budget to install any security services. If applied properly, this doesn't need huge budgets to protect their sensitive data or the organisation's security.
Before talking about Ethical Hacking Services, we should know Why data is a valuable asset for any organisation. It needs to be protected from internal or external and illegal access else may lead to severe financial loss, reputational loss, customer trust degradation and brand erosion. Government and Security organisations have applied rules on data protection for the organisations/ industries and in case of non-compliance, this may lead to big troubles.
All organisations must adhere to the CIA triad (Confidentiality, Integrity and Availability) for data security and apply relevant measures to ensure data security. But there are still incidents happening because of some or other reasons. Hence ethical hackers (hackers that work with a positive approach) are required to comprehend the flaws better from the threat actors' point of view. Once discovered it is easy to plan a security roadmap and apply preventive measures.
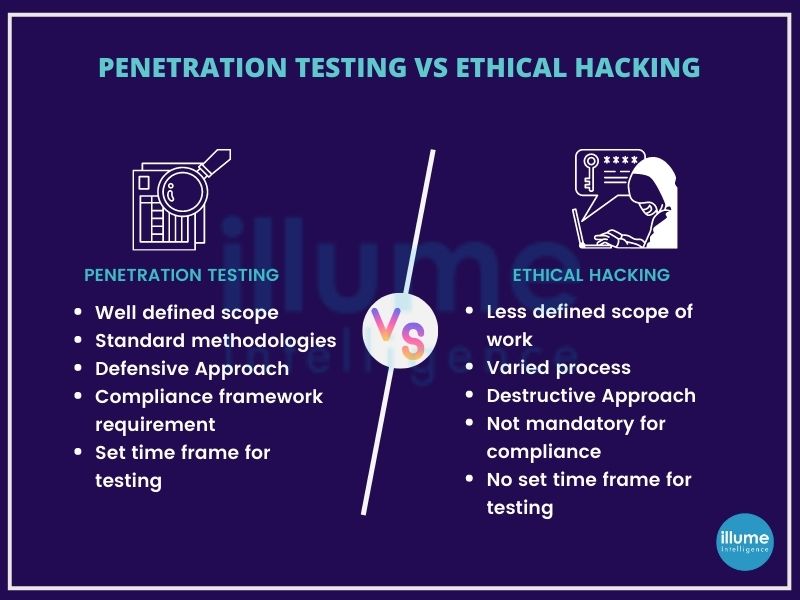
What are Ethical Hacking services?
The word hacking itself is capable of giving goosebumps to anyone so, how come Ethical Hacking is its solution? As the term says Ethical Hacking is the practice of making authorised attempts to hack into the security for finding the strength of the security posture.
No matter what you apply all the security methods, the slightest miss can bring down the entire system. So understanding the hackers' perspective helps in protecting the system in a better way. Ethical hackers intend to find loops for fixing them before they fall into the eyes of bad guys.
The aim of ethical hacking is to protect the data, system and infrastructure from threats and contribute to the success of the digital business. The information and data are kept secure as required by the business.
Identifying risks and weaknesses of the network to provide detailed reports with preventive measures along with guidance for implementing them is the core objective of ethical hacking.
What is included in Ethical Hacking Services?
Illume Intelligence’s ethical hacking services include the evaluation of infrastructure, devices, applications, networks etc as per the requirement of the organisation. It uses both automated and manual tools to gather information. Based on the information gathered the attack vectors are planned.
Our ethical hacking services focus on all the areas of your business, compliance, operations, security, awareness etc, providing insights into particular threats and vulnerabilities causing challenges to your organisation. Below are the services offered
-
Ethical Hacking Consultation
-
Vulnerability Assessment and Customized reporting
-
Ethical Hacking Remediation support
-
Internal systems assessment
-
Social engineering (phishing) exercises
-
External network penetration testing
-
Web application penetration testing
-
Cloud services Vulnerability Assessment
-
Wireless Security Assessment
-
Infrastructure architecture review
How Illume Intelligence's Ethical Hacking services can help?
Illume Intelligence's team of ethical hackers will customize the security services to meet the organisation's needs. From the quick vulnerability assessment to the complete security assessment of the entire organisation is supported by our skilled professionals.
Understanding the client's needs and preparing the strategy to address them with precision and optimum utilisation of resources. We address the needs of big organisations and SMBs with the required capabilities in a flawless manner with our industry expertise gained through experience. Our commitment to quality services is shown by our client's satisfaction and retention.
Are you still wondering whether to avail of Ethical Hacking services or not? We understand your business concern and advise you to talk to our security expert in finding the best methods to enhance your organisation’s security.
Taking action now is far better than regretting it in future.
The Consumer Data Right regime gives organisations the opportunity to become an accredited data recipient. The rewards are plentiful - but there's a lot to lose if you fall behind.
The Consumer Data Right (CDR) is a win-win situation for both the businesses and the consumers. It gives organisations the opportunity to become accredited data recipients giving them a unique chance to gain a competitive edge and providing Australian residents with better choice, access and control of their data. Initially, it is applied to the banking industry, with telecommunication and energy retailers following soon after.
Since its implementation in 2019, the CDR regime has begun its transformation and digitisation of the Australian economy. Data holders are required to transfer customer data if requested by the customers. In July 2021, the 'Consumer Data Right Strategic Assessment Consultation Paper' was released by the Treasury mentioning the expansion of CDR to a whole range of sectors covering almost the entire economy. This will be in action over time. Hence, the opportunity to become an Accredited Data Recipient (ADR) is now available to all sectors.
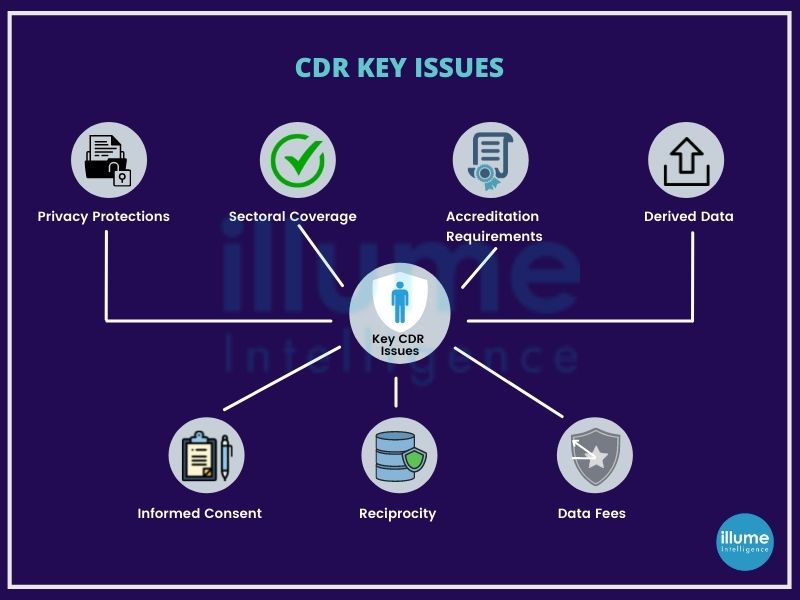
The ability to easily share data paves the way for new products and services, making it easier for individuals and businesses to compare products, helping to switch providers for the better deals. This will encourage more competition in the market leading to lower prices. CDR gives more choice, control and convenience to the consumers. It's an opt-in service, meaning one can choose whether to use it or not. CDR requires the organisations open to sharing consumer's data to third parties must obtain user consent for data sharing and apply strong customer authentication for services. All CDR accredited providers must follow strict rules and regulations for data security.
CDR regulation
The OAIC and Australian Competition and Consumer Commission (ACCC) jointly regulate CDR. OAIC enforces the privacy safeguards and privacy-related rules along with advising the minister and CDR agencies on the privacy implications of the CDR rules and data standards. whereas ACCC enforces the CDR rules and data standards and carries out strategic enforcement. The ACCC also accredits data recipients, manages suspensions and revocations of accreditation, and maintains a register of accredited persons.
Doing Business in Singapore? Missing on PDPA may become a big challenge for your business
Singapore is a global techgiant, topping the rankings of the Global Smart City Performance Index continuously for multiple years. Since launching its Smart Nation initiative in 2014, Singapore has introduced a lot of smart technologies in both public and private sectors.
Lot of data is travelling on the cloud as cloud computing is an integral element for the digital transformation objectives and hence the laws to protect the data becomes mandatory. Singapore's Personal Data Protection Act (PDPA) governs the collection, use, disclosure and care of personal data.
Purpose of the PDPA
“To govern the collection, use and disclosure of personal data by organisations in a manner that recognises both the right of individuals to protect their personal data and the need of organisations to collect, use or disclose personal data for purposes that a reasonable person would consider appropriate in the circumstances.”

What is the Personal Data Protection Act (PDPA)?
The Personal Data Protection Act (PDPA) is Singapore's primary law regulating its residents' data handling by businesses.
Businesses should take Singapore's data privacy laws as mandatory for the protection of data. As this has become of utmost importance, laws have installed nine data protection obligations with which every business must comply.
The Nine Data Protection Obligations
1. Consent Obligation
2. Purpose Limitation Obligation
3. Notification Obligation
4. Access and Correction Obligation
5. Accuracy Obligation
6. Protection Obligation
7. Retention Limitation Obligation
8. Transfer Limitation Obligation
9. Accountability Obligation
Scope of PDPA -
All private organisations in respect of the personal data of individuals that they collect, use and/or disclose.
Organisations that are not present in Singapore but collecting, using and disclosing data within Singapore. Related organisations receiving data from these organisations being parent companies or others are not exempted from PDPA.
Who is exempted from the application of PDPA -
1. Individuals acting in a personal or domestic capacity
2. Employees acting in the course of their employment with an organisation
3. Public agencies
4. Any other organisation or personal data, or classes of organisations or personal data as may be prescribed.
Although the government agencies are not subjected to PDPA as they have their own set of regulations, this exemption is not extended to the private sector organisations working on behalf of the government agencies.
Who regulates data protection?
The PDPC is the regulatory authority responsible for administering and enforcing the PDPA. It is part of the converged telecommunications and media regulator, the Infocomm Media Development Authority ('IMDA'), which is, in turn, a statutory board under the purview of the Ministry of Communications and Information.
The GDPR aims at allowing the European citizens to control their personal data, as an extension of an individual’s fundamental ‘Right to Privacy.’
GDPR (General Data Protection Regulation) is the core of Europe's digital privacy legislation. It is a new set of rules designed to give EU citizens more control over their personal data. The aim is to simplify the regulatory environment for business in the EU, benefiting both the citizens and businesses from the digital economy.
Every aspect of our lives revolves around data. From banks, governments, shopping malls, educational institutions, healthcare services to social media, whatever we use involves the collection and analysis of our personal data. Personal information like name, contact, address, financial details, IDs, etc is collected, analysed and perhaps most importantly stored by the organisations.
In this high time of cyber security, the data is at very big risk if not protected properly. Data breaches may happen, information may get lost or stolen by the people having malicious intent. Under GDPR, not only do the organisations have to ensure that personal data is gathered legally and under strict conditions, but also the data collectors and managers are obliged to protect it from misuse and exploitation, respecting the right of data owners, else may face penalties for not doing so.

Who comes under GDPR?
Any organisation operating within the EU, as well as the organisations outside of the EU offering goods or services to the customers or businesses in the EU.
According to Article 4 of GDPR, there are two different types of data handlers - 'Processors' and 'Controllers'. A controller is the one who determines the purpose and means of processing personal data and the processor is the one who processes the personal data on behalf of the controller.
When does the GDPR apply outside Europe?
The main purpose of the GDPR is to protect the EU citizens' and residents' data. The law, therefore, applies to all the organisations dealing with EU citizens whether they are EU-based organisations or not.
There are two situations when a non-EU organisation might have to comply with the GDPR -
1. Offering services or goods - If the organisation is catering to EU customers, it has to be GDPR compliant. Occasional instances are exempted from these.
2. Monitoring client's behaviour - Organisations using web tools that allow you to track cookies or the IP addresses of people visiting from EU countries.
Exceptions to the GDPR rule
Majorly there are two exceptions -
1. Purely personal or household activity - The GDPR only applies to organisations engaged in “professional or commercial activity”.
2. Fewer than 250 employees - Small and medium-sized organisations are not totally exempted from GDPR, but the regulation does free them from record-keeping obligations in most cases (see Article 30.5).
What are the penalties for non-compliance?
The GDPR recognizes two levels of fines for less severe and very severe violations.
Non-compliance may lead to fines up to 20 million euros or four per cent of worldwide turnover - whichever is greater - for infringements of the rights of the data subjects, unauthorised international transfer of personal data, and failure to put procedures in place for or ignoring subject access requests for their data.
Benefits for the businesses of data protection and GDPR compliance -
The GDPR aims at protecting the EU citizen's data and applies to all the organisations that are dealing with EU citizens' data irrespective of the organisation's location. Even now many organisations continue to view it as a troublesome requirement. The regulation can help in streamlining and improving multiple core business activities.
1. Easier business process automation - Gives an opportunity to look at how well they're managing customer and client data storage, processing and management responsibilities.
2. Increased trust and credibility - GDPR article 5 includes seven fundamental principles forming the basis and rationale for the laws within the GDPR. This helps organisations in gaining trust and credibility from their customers by following these principles.
3. Better understanding of the data being collected - GDPR gives businesses a greater understanding and appreciation of their data and how it moves throughout the organisation. Privacy initiatives generally trigger a consolidation of data platforms, which can benefit departments, such as human resources, by enabling easier reporting and faster and better decision-making.
4. Better data management - Organisations get a better idea of what data they are collecting and for what. This way they will be able to track the data flowing in the organisation, create and deploy data protection policies, preparing the cybersecurity breach response plan on time.
5. Brand reputation - By protecting consumer privacy, organisations not only will avoid potential penalties, but they will have a good brand value and reputation. This will help in building customers' trust in the brand in the long term.
Does your business come under GDPR? Check out how we can help you to get compliant with GDPR.
Every individual has a right to privacy and to decide where and with whom the data should be shared.
Introducing the India Digital Personal Data Protection Act—a groundbreaking legislative milestone designed to safeguard the rights and privacy of individuals across the nation. This comprehensive legislation establishes a robust framework governing the entire lifecycle of personally identifiable information (PII), encompassing its collection, utilization, storage, and transfer.
In navigating the dynamic landscape of digital data, a thorough grasp of the fundamentals of this act becomes indispensable. Compliance is not just a requirement but a commitment to upholding the principles that form the backbone of this progressive legislation. Stay informed, stay compliant, and embrace the future of responsible data management under the India Digital Personal Data Protection Act.
At the forefront of data protection in the digital age stands the DPDP Act, a pivotal legislation with the singular mission of safeguarding the personal data of individuals while empowering them with unprecedented control over their information. In an era marked by the incessant collection, processing, and sharing of personal data, this act emerges as a beacon, establishing a robust legal framework that addresses the myriad concerns and risks inherent in such activities.
Applying to a broad spectrum of entities, including government agencies, private enterprises, and organizations dealing with personal data, the DPDP Act casts a wide net to ensure comprehensive accountability. Its jurisdiction spans entities collecting, processing, storing, or transmitting personal data within India or from individuals within the country. By doing so, the act mandates compliance with its regulations, placing all stakeholders under the umbrella of responsibility.
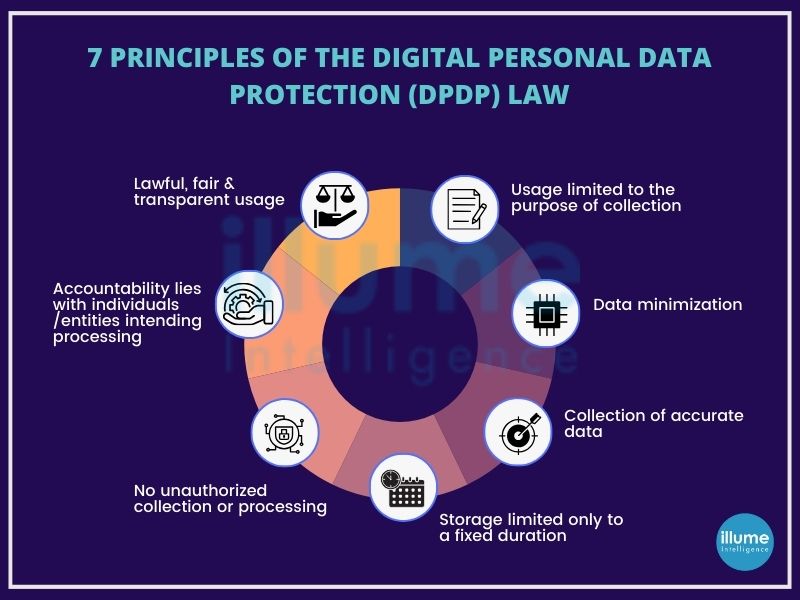
Who complies with the DPDP?
The expansive reach of the Bill encompasses your organisation, necessitating compliance if:
-
Your organisation engages in the processing of Personal Data belonging to individuals.
-
Personal Data is processed within the geographical bounds of India by your organisation.
-
The Personal Data collected by your organisation originates from online sources.
-
In the case of offline data collection, if the acquired information is subsequently digitized.
-
Your organisation engages in the processing of Personal Data outside the borders of India, specifically linked to profiling or activities related to offering goods or services to Data Principals within the territory of India.
In aligning with these criteria, your company falls within the ambit of the Bill, emphasizing the importance of ensuring adherence to the stipulated regulations for comprehensive data protection and compliance.
Why Do Businesses Need To Comply With The Digital Personal Data Protection (DPDP) Law?
Businesses are required to adhere to the Digital Personal Data Protection (DPDP) Law for a multitude of compelling reasons:
-
Data Privacy Protection: Compliance is synonymous with safeguarding individuals' data, offering a robust shield against unauthorized access, misuse, and data breaches. By prioritizing data privacy, businesses instil confidence in their customers, building a foundation of trust that is pivotal in today's digital landscape.
-
Legal Obligation: The DPDP Law establishes a mandatory framework for organizations handling personal data. Compliance isn't just a best practice; it's a legal imperative. Businesses that fall in line with the stipulations of the law mitigate the risk of legal actions, ensuring that their operations align with the regulatory landscape.
-
Business Reputation: Non-compliance poses a significant threat to an organization's reputation. In an era where trust is paramount, failing to meet the standards set by the DPDP Law can erode customer trust and damage an organisation's standing in the market. A tarnished reputation can result in losing existing customers and hamper acquiring new business opportunities.
-
Avoiding Fines and Penalties: The DPDP Law doesn't just set guidelines; it wields substantial consequences for non-compliance. Organizations that fail to meet the prescribed standards risk facing hefty fines, with penalties extending up to 250 crores. The financial impact of such fines can be severe, affecting the organization's financial health and potentially jeopardizing its business continuity.
In essence, compliance with the DPDP Law is not merely a regulatory formality; it is a strategic imperative for businesses seeking to thrive in the digital era while upholding the principles of data protection, legal responsibility, and maintaining a positive brand image.
How Can Businesses Comply With The Digital Personal Data Protection (DPDP) Law?
Achieving compliance with the Digital Personal Data Protection (DPDP) Law necessitates a strategic and proactive approach. Here are key steps that businesses should take to align with the regulatory framework:
-
Data Identification:
Thoroughly identify and document all personal data that the business collects and processes. This includes data obtained online, offline, or through any other channels.
-
Consent Management:
Implement robust consent mechanisms to ensure that individuals explicitly agree to the collection and processing of their data. Communicate the purpose for which the data is being collected and seek consent accordingly.
-
Data Security Measures:
Institute stringent security measures to safeguard personal data from unauthorized access, breaches, or misuse. Employ encryption, access controls, and other security protocols to create a robust defense against potential threats.
-
Data Retention Policies:
Develop and adhere to data retention policies to ensure that personal data is retained only for as long as necessary. Regularly assess the need for data storage and promptly delete information that is no longer required.
-
Individual Rights Response:
Establish a streamlined process to respond to individual requests about their data. This includes providing access to the data, correcting inaccuracies, or erasing the data when requested. Ensure that this process is transparent, efficient, and aligns with regulatory requirements.
-
Privacy by Design:
Integrate privacy considerations into the design and development of products, services, and systems from the outset. This proactive approach, known as Privacy by Design, ensures that data protection is embedded into the core of the business processes.
-
Employee Training:
Conduct regular training sessions to educate employees on the importance of data protection and compliance with the DPDP Law. Ensure that all staff members are well-informed about their responsibilities in handling personal data.
-
Data Protection Impact Assessments (DPIAs):
Conduct DPIAs to assess the impact of data processing activities on individual privacy. This helps in identifying and mitigating potential risks and ensures that privacy considerations are integral to business decisions.
-
Data Breach Response Plan:
Develop a comprehensive plan for responding to data breaches. This should include immediate steps to contain the breach, notifying relevant authorities, and communicating with affected individuals as required by the DPDP Law.
By diligently implementing these steps, businesses can not only navigate the complexities of the DPDP Law but also foster a culture of responsible data management, thereby building trust with customers and maintaining compliance with regulatory standards.
Network Segmentation can protect you against ransomwares and malwares
Network segmentation (Network Partitioning or Network Isolation) is used to improve network security but it is not an easy task. Generally, networks are designed to be tough on the outside and simple inside. Organisations following regulations install a mature firewall perimeter and some sort of Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) to monitor the incoming traffic.
However, if someone manages to sneak in through that traffic will have a smooth network structure that can be exploited as required. Most of the tools are designed to perform specific functions and will ignore the movement outside of their programming. Gives the advantage to the hidden malicious programs to act free and launch an attack or simply stay quiet and leak the information. This kind of flat network infrastructure is easy to maintain but is a great opportunity for the threat actors to breach the main security and get access to the entire infrastructure.
What is Network Segmentation?
Segmenting the computer network is splitting the network infrastructure into smaller network segments. All servers and workstations are not required to communicate with each other but keeping them on a common network allows the threat actors for exploiting them.
Segmentation can be done physically or virtually. The main idea is to limit the communication between the devices and hence reduce the attack surface area.
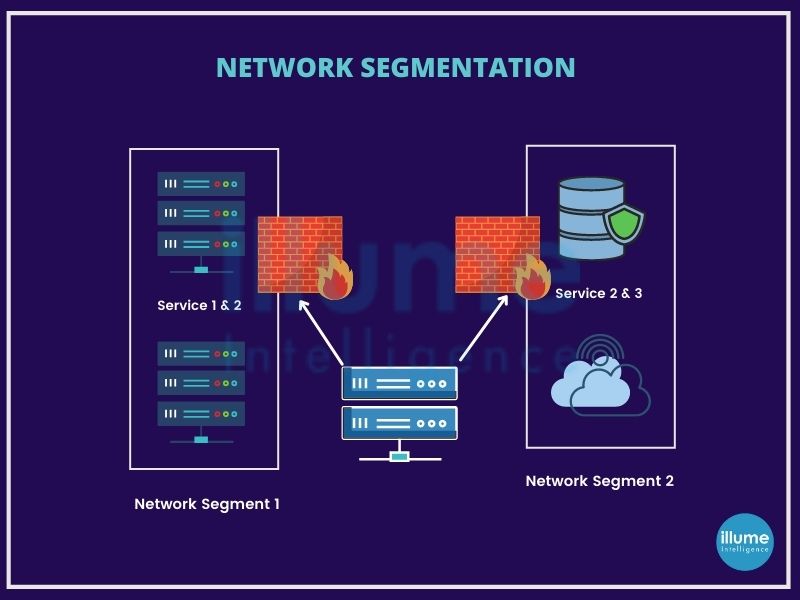
Who Needs Network Segmentation?
Every organisation running multiple internal systems for meeting its business needs must have network security. The more complicated the architecture is, the more important the need for segmentation. Businesses relying 100% on SaaS solutions or business that works completely offline will not need network segmentation.
Businesses running on flat networks will be ideal targets for hackers. A flat network may seem easy saving time and money for installation may lead to bigger disasters later. There is no substitute for network segmentation.
The Benefits of Network Segmentation
Network segmentation offers absolute and efficient security among all the information security methods. Following are some of the benefits an organisation will avail from applying network segmentation -
1. Data Security - More segments will lead to more blocks and will stop the hackers from exploiting the network and stealing the data.
2. Threat Reduction - In case of the attacks the bad actors will have the access to the limited network and hence will take some time for them to get details and insights for full structure hence giving alerts and time to the administrators to take preventive actions.
3. Controlled Access - Network segmentation helps in protecting against insider threats. Limiting access to different critical networks and allowing only a limited number of people helps in restricting the way attackers gain access to systems.
4. Enhanced Threat Detection and Tracking - Segmentation allows easy monitoring. Increasing the number of checks makes it easier to detect suspicious behaviour. This also helps in determining the source and context of a problem.
5. Rapid Response Times - Quick response from the IT team is reacting to remote operations because of different routers. The threat can be easily tracked leading to quick detection of impacted sections.
6. Damage Management - Segmentation keeps the damage caused limited to the particular section, keeping the others safe.
7. Safeguard Endpoint devices - The unwanted activities are maintained away from the unsecured devices due to repeated load balancing. This is gaining importance due to the increasing use of IoT devices.
Network segmentation helps in reducing the threat landscape, controlling traffic and detecting crucial infringements. It is a recommended framework based on the patterns the hackers are using to exploit the organisation's network for creating a big impact to harm the organisation and the associated businesses.
Organisations that can automate more than 70% of their network changes can reduce the number of outages by at least 50% and deliver services up to 50% faster - Gartner
Manually changing the security policy is complex and error-prone leading to business slow down. Reworking to rectify the policy may lead to compliance violations. It includes multiple teams and multiple devices making it furthermore complicated.
The network is a lifeline of any organisation and making it work flawlessly takes a lot more than establishing and setting the things once. That's why many businesses are looking up to automation as a solution for regularly maintaining the security.
Challenges to Automation
In spite of knowing that manual policy changes impact the productivity of the organisation they are not ready to take the steps towards automation because of the wrong perception of security. The production environment in every organisation is maintained by multiple teams like DevOps, maintenance, IT, Cloud security, and so on. Different teams have different levels of security understanding and hence it is challenging to bring them all on a common platform.
The threat to the business is not a determined hacker finding elaborate ways through defences. Networks get exposed due to accidental firewall and cloud security group misconfigurations. Manual rule and policy management of complex ground-to-cloud networks introduce countless opportunities for error and most breaches, giving advantages to the hacker to sneak in.
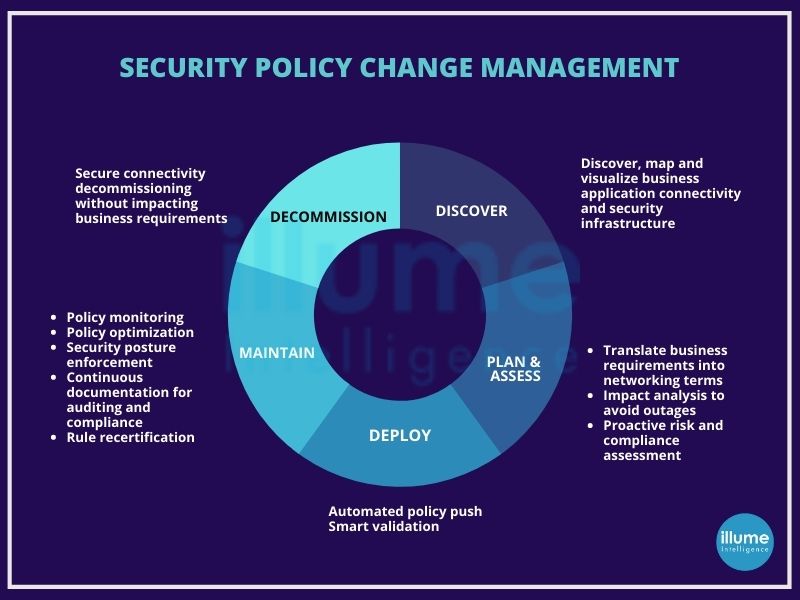
How does the Security Policy Change Management process work?
The process of Security Policy Change Management typically involves the following steps:
1. Identification of the change request - A change request is submitted, detailing the proposed security policy modification.
2. Review and approval - The change is reviewed by relevant stakeholders, and approval is obtained.
3. Testing and validation - The change is tested in a controlled environment to ensure it works as expected and doesn't cause any issues.
4. Implementation - The change is deployed following a pre-defined plan, and a rollback plan is prepared in case of any issues.
5. Post-change evaluation - The effects of the change are monitored to ensure everything is functioning correctly.
What to focus on for Security Policy Change Management?
With the quick-rising threat, all the industries are under pressure to implement security for safeguarding their business and in a hurry they may trip on some common problems such as under -
1. Focusing on less important tasks - Documentation is often confusing and makes teams focus on less important things and waste more time on things that just need to be mentioned rather than things that hold more importance in understanding the dependencies and support to the business.
2. Not removing firewall rules for decommissioned applications - old and decommissioned network components and firewall rules may clutter the network and make the performance bad and it must be revised from time to time.
3. Miscommunications among different teams - Maintaining a large IT infrastructure requires multiple teams. These teams always have problems understanding each other's work and communications making it a lengthy and difficult process to implement changes.
4. No proper documentation - proper documentation is a must as it helps in keeping everyone updated on the changes made in the past. What happened and what was done to rectify it, why any rule was applied and what is linked to it? Without the proper documentation, it will be hard to perform the audit.
5. Human errors - there is a huge scope of errors when editing the rules manually. Even the slightest looking mistype of port number can lead to a big problem for the entire network making it vulnerable.
Quick efficient support for managing and improving your responses to security incidents
When impacted by a cyberattack, a clear understanding is needed for analysing the situation and responding quickly for protecting the assets, operations and business reputation.
Incident response management is a set of policies and procedures that are used to identify, contain and eliminate cyberattacks. The aim is to enable an organisation to quickly detect and limit the attacks, minimising damages and preventing future attacks.
Preparing an Incident Response Management Plan will help an organisation in defining a clear understanding of what constitutes an incident for the organisation along with the clear guidelines on the process to be followed on the occurrence of the incident. It should also clearly mention the roles and responsibilities of the teams, employees or leaders responsible for complete incident handling.
The goal of an incident response management team is to coordinate and align the key resources and team members during a cyber security incident to minimise impact and restore operations as quickly as possible. This includes customised functions like investigation and analysis, communications, training and awareness, documentation and timeline development as per the organisation’s requirements.
Why is Incident Response Management Important?
Cyber attacks are increasing in scale and frequency making incident response plans a must for organisations’ cyber defences. Data breaches not only cost operational downtime but reputational and financial losses. The longer the time taken to detect and mitigate any vulnerability, the more harmful it becomes for the business. It may lead to devaluation of the stock value, loss of customer trust and heavy financial penalties from regulatory bodies making it impossible for the businesses to recover from the shock. To eliminate such risks, organisations need to plan -
1. Restoring daily business operations.
2. Minimising the attack surface.
3. Fixing cyber vulnerabilities quickly and effectively.
4. Securing the infrastructure by avoiding future attacks.
5. Aligning with the regulatory standards.
Steps for effective Incident Response Management
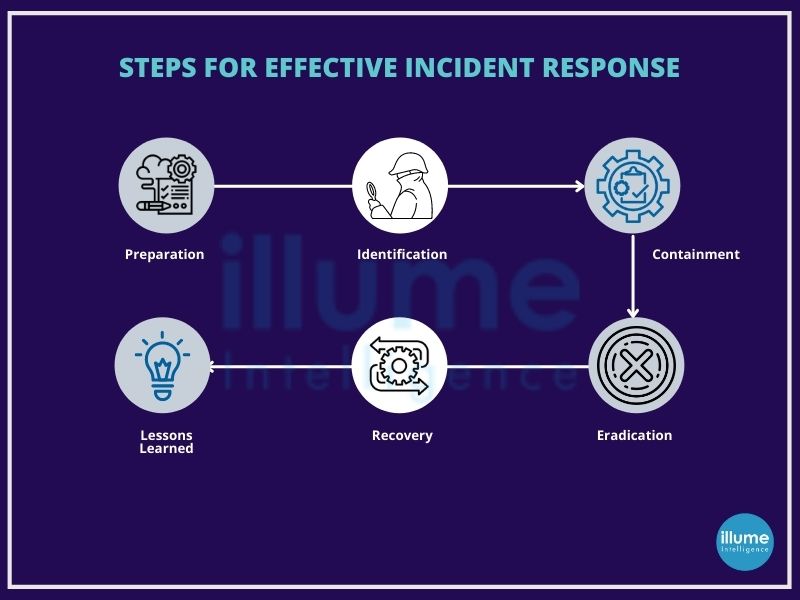
The SANS Institute provides guidelines for 6 steps for effective Incident Response Management
1. Preparation - Preparation involves reviewing the existing security measures and policies to determine the effectiveness of the current system. The gathered information will be useful for prioritising responses to the incident types. This should also involve policy, response plan, communication, documentation, determining CIRT members, access control, tools and training.
2. Identification - Once the tools and procedure are determined in the preparation phase, teams work to identify any suspicious activity. After detecting the incident, the team works to determine the nature of the attack, its source and the motive of the hacker.All the evidence found should be secured for in-depth analysis along with the proper documentation of the steps taken.
3. Containment - Containing the incident is the top priority as soon as the incident is detected, for containing the damage and preventing further damage from occurring. It is advised to follow SANS guidelines for preventing the destruction of any evidence that may be needed later for prosecution. These steps include short-term containment, system back-up, and long-term containment.
4. Eradication - The phase of neutralising the threat and restoring the system to as close to the previous state as possible. Ensuring proper removal of the malicious content and the affected systems are completely clean. If required the systems can be taken offline for replacing the clean versions in recovery.
5. Recovery - Bringing the recovered systems back online and ensuring the systems are not infected or compromised again by monitoring for some time. This includes setting timelines for fully restoring the operation and monitoring for abnormal activities. At this stage, it is also possible to calculate the cost of a breach and subsequent damage.
6. Lessons Learned - Often overlooked or ignored phase but is highly important as it helps to understand and improve future incident response efforts. This provides the opportunity for updating the incident response plans with the information gathered. This is highly helpful for review of the incident and may be used for recap meetings, training materials or as the benchmark for comparison.
There is a need for an incident response plan but shockingly very few organisations have a proper action plan. When talking about cyber security, time is a very crucial factor. The longer the time the attack is undetected, the more dangerous it becomes. It can destroy the organisation and its associates by using the organisation's data and network to launch a bigger attack spreading to other organisations as in the case of supply chain attacks.
Understand and prepare for your SOC 2 assessment today to secure internal and client's businesses.
With the increasing cyberattacks, all the organisations are subjected to the risks like malware, phishing, DDoS attacks etc. Hence saas and Cloud computing vendors are required to undergo SOC 2 audits to assess and ensure their internal security controls.
SOC 2 framework (System and organisation Controls) was created by the American Institute of Certified Public Accountants (AICPA) in response to the growing concerns for data security and privacy. It is an independent auditing procedure ensuring that service providers handle sensitive client data securely on the cloud and maintain its privacy.
SOC 2 certified means the organisation has established practices as required with levels of security across the organisation for data protection. Saas companies that manage customer data in the cloud should be SOC 2 compliant. This audit is performed annually. Although SOC 2 is not a legal requirement, it shows the trustworthiness of the service provider and assures the clients that their data will be handled securely.
SOC 2 audit preparation
SOC 2 evaluates the security control's effectiveness over a period. The audit preparation has eight steps-
1. Defining the SOC reporting period
2. Quantifying Risk
3. Defining the Scope
4. Building a strong compliance team
5. Readiness assessment
6. Identifying gaps
7. Remediation
8. Gathering additional documentation
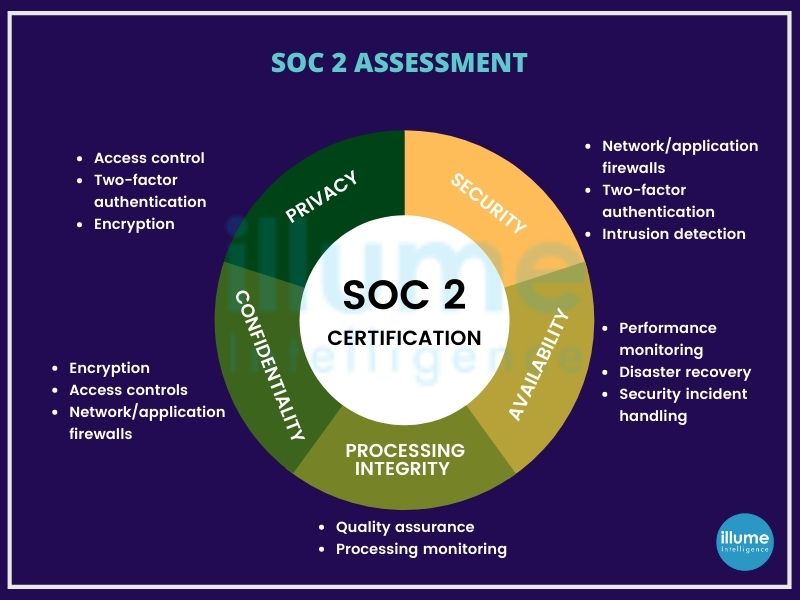
5 trust service principles of the SOC 2 compliance -
1. Security - Security is important and includes common criteria related to data and system protection.
2. Availability - Availability ensures the access to data the customer receives and how readily available it is. Also reviews accessibility for operations, monitoring and maintenance of data.
3. Processing integrity - The processing of data as per authorization and assesses the accuracy, completeness, validity and timeliness of the data.
4. Confidentiality - Encourages the encryption of in-transit data as well as client certificates and personal authentication certificates.
5. Privacy - Aims at ensuring the confidentiality and security of personal identifiable information (PII).
Why SOC 2 Assessment for your organsation?
1. Trust and Reputation - Increased customer trust and organisational reputation
2. Better Data Protection - Increased data protection with the application of norms
3. Improved Outlook - Increased security, availability, processing integrity, and privacy
4. Increased Awareness - Better awareness of organisational vulnerabilities
5. Marketing Differentiator - Marketing differentiator among others by adhering to rigorous standard with SOC2 Audit
6. Operating Effectiveness - Ensures maintaining an effective information security control environment
7. Commitment to IT Security - Strong commitment towards overall IT security
8. Regulatory Compliance - SOC2 requirements goes in sync with other frameworks including HIPAA and ISO 27001
How often do you schedule a SOC2 Audit?
Normally a SOC2 report is for a 12 month duration, but the auditing can be performed in the duration of every 6 months depending on the requirements of the organisation for the ongoing concerns in the operational control environment.
SOC 2 audits and reports provide detailed evidence of the effective security controls implemented in the service provider's system. It makes the vendor trustworthy and gives an edge over competitors.
Book your SOC 2 audit today and raise the bar for the competition.
Securing the nation by securing critical information infrastructure
Industrial Control Systems, specifically the old configurations, are often deployed as isolated installations to work in standalone environments without any connection to the external network including the internet.
ICS-embedded architectures are different from other systems. Older ICS were designed on the assumptions to connect in a small internal network. The span of the internet has changed the complete picture. ICS even working on internal networks are exposed to security threats. The ICS may be running on a separate network, but physical isolation is becoming the exception. Even without direct contacts, the security of the ICS can be compromised.
It has always been a challenge for the security team to keep up with new threats but with ICS the impact could be unimaginable.
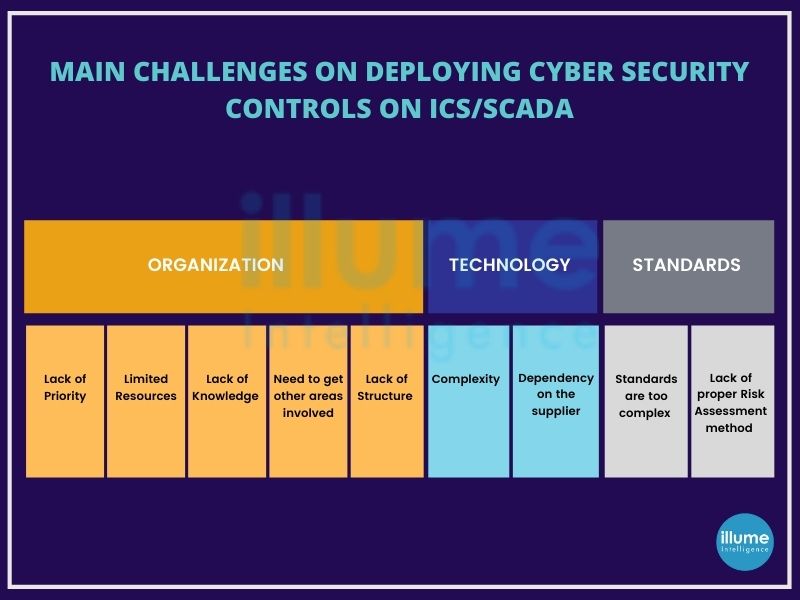
What is "ICS SCADA Security Testing"?
"ICS SCADA Security Testing" refers to the process of evaluating and assessing the security posture of Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems. These systems are used to monitor and control critical infrastructure such as power plants, water treatment facilities, manufacturing plants, and more. Security testing aims to identify vulnerabilities, weaknesses, and potential threats that could be exploited by malicious actors to disrupt or damage the infrastructure.
Why is ICS/SCADA security testing important?
ICS/SCADA (Supervisory Control and Data Acquisition) technologies are becoming high-value targets for threat actors for disrupting business operations, ransomware or compromising rival nation's systems. It is becoming crucial to address these security issues. The organisations should understand that even running on internal networks, their systems are exposed to cyberattacks if they are not adequately secured. It is important to conduct ICS security testing and implement the necessary compliances and regulations. The ICS/SCADA Security Testing or ICS/SCADA Penetration Testing helps in finding all the flaws that may cause a problem in future hence must be resolved on time.
Our approach to ICS/SCADA Security Testing
1. ICS Cyber security framework - Presenting a framework for the ICS/SCADA penetration testing requirements on accessing the entire system.
2. ICS/SCADA Risk Assessment - Gathering information regarding the applications and components required for conducting the testing.
3. ICS/SCADA gap analysis - Analysing the current and desired system gap to reduce the risk and eliminate threats.
4. ICS/SCADA Penetration Testing - Scanning the network with various tools to identify vulnerabilities.
5. ICS/SCADA services - Trying to exploit the vulnerabilities identified, manually with the help of commercial tools and custom scripts and Powershell.
6. ICS incident response - A detailed report of the assessment, including an executive summary for the management. This comprises the complete findings with risk priorities, remediations and recommendations made as a part of ICS/SCADA security testing.
ICS/SCADA tests require proper planning and a tailored approach for the testing. Our expert team can help you in getting the complete picture of your risk exposure with recommendations to resolve before they are exploited.
Talk to our executive and get your security testing conducted.
Providing powerful assistance for the risk and compliance through PCI DSS Compliance
Any organization that stores, processes or transmits credit card data needs to abide by the technical and operational requirements specified by the Payment Card Industry Data Security Standard (PCI DSS). All organizations irrespective of their size have to follow these rules.
A PCI DSS readiness assessment (Gap Analysis), helps in the identification of flaws in the organization's current system and recommends proper controls to be implemented. It helps in better understanding of weakness and responding to rapidly evolving security compliance obligations. This helps the organization develop a strategy and plan to achieve compliance.
This readiness assessment makes it easy to pass through the Qualified Security Assessors audit of the system, policies and procedures, controls and other areas of the organization.
Why is PCI DSS Compliance important?
Almost every organisation is at risk of fraud and identity theft with the increasing cybercrimes. Data breaches not only harm a business but the associated customers as well. Getting compliant will help in reducing costs, data breaches, prevention from fines, loss of customers' trust etc.
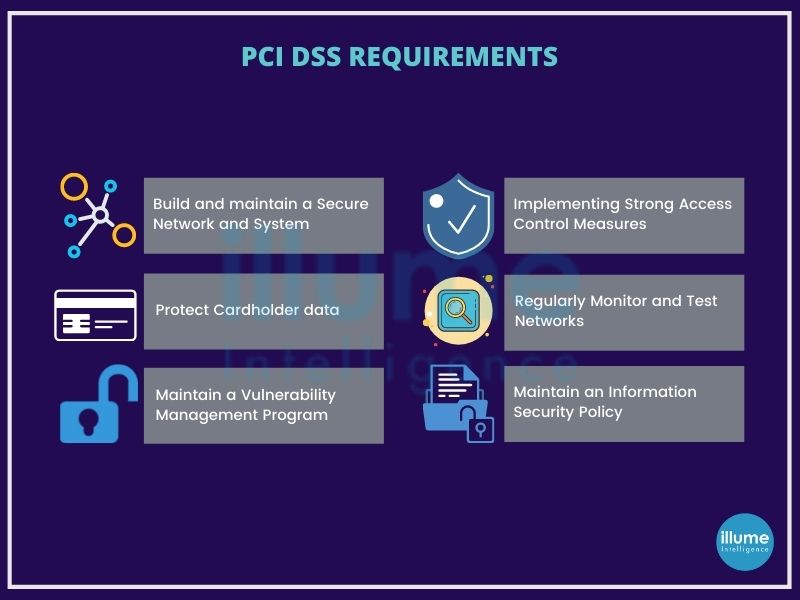
What are the requirements of PCI DSS?
PCI SSC sets both operational and technical requirements with the core focus to protect cardholder data. The 12 requirements are -
1. Install and maintain a firewall configuration to protect cardholder data.
2. Do not use default passwords for the system and other security parameters.
3. Protect stored cardholder data.
4. Encrypt transmission of cardholder data across open, public networks.
5. Use and regularly update anti-virus software or programs
6. Develop and maintain secure systems and applications.
7. Restrict access to cardholder data by businesses that need to know.
8. Assign a unique ID to each person with computer access.
9. Restrict physical access to cardholder data
10. Track and monitor all access to network resources and cardholder data.
11. Regularly test security systems and processes.
12. Maintain a policy that addresses information security for all personnel.
It is advised to define the PCI DSS scope. It is crucial to reduce the PCI DSS audit scope because it will determine the compliance costs, operational costs and risks associated.
Get our expert team to assist you today with your PCI DSS Compliance Preparedness.
Gain a competitive edge with ISO 27001 Certification
Businesses today are processing huge information, increasing challenges for data protection. With an ISO 27001 certification, an organization can ensure its capabilities to perform to international standards for production and quality control.
ISO 27001 certification uses globally recognized standards for assessing the security of information and IT environments. It describes the requirements of implementation as well as documentation of ISMS. Minimizing security risks and implementing IT security procedures contribute to the long-term optimization of the quality of the system. Improving the company's quality standards and maintaining data security is among the multiple benefits of gaining ISO 27001 certification.
One can consider ISO 27001 as a framework that systematizes an organisation's risk management approach. It is required to fulfil stringent norms of legal, physical and technical information risk management systems when applying for ISO 27001 certificate.
Taking the assistance of the ISO 27001 consultancy will be a smart move to easily adhere to the required norms with technical advice on how to improve the current situation. This includes improving general company information security policies and framework, methods of addressing information security, protection and handling of third-party data etc. Implementation of compliance and feedback makes the system more efficient.
What is the importance of the ISO 27001 Consultancy?
1. Improved operational standards - By stepping into your journey to ISO 27001 certificate a consultancy helps in improving the company's standards.
2. Managed resource shortcomings- Managed the skill requirements of the staff for full implementation of the framework.
3. Benefits of stringent forms - Assisting in implementing more stringent forms of information security control ensuring customer trust in the organization.
Team Illume works collaboratively with the ISO 27001 certification organisation to ensure that the framework should be achieved with minimal friction and maximum value.
Why ISO 27001 Consulting?
The benefits of ISO 27001 certification comprise a long list as it gives the trust of the stakeholders and increases the brand value. Some of the major benefits are
Controlled Risk - Reduced chances of security from security breaches and IT risks.
Compliance Ready - Structured method of addressing compliance requirements.
Lower Cost - Regular maintenance is cheaper than losses from data theft.
Competitive Edge - Recognized standard gives a competitive edge over other players.
Trusted Partner - Increase in trust by partners, customers, and stakeholders.
Information Security - Confidentiality of the information.
ISO 27001 2013 vs. ISO 27001 2022 revision – What has changed?
After nine long years, ISO 27001, the world's leading information security standard got updated to the new ISO 27001:2022. The organisations following the 2013 revision have been given 3 years window to transit to the 2022 revision as the complete support for the 2013 revision will end by Oct 2025. Organisations can certify against the 2013 revision until Oct 31, 2023, at the latest.
Overall the changes inculcated in the 27001:2022 revision are small and moderate. The main part of the standard still has 11 clauses with some changes. Annex A has changed in major with the number of controls dropping to 93 from 114 and is now organised into only 4 sections.
The 2022 version includes several updates and improvements including new topics such as data governance, supply chain security, and the use of cloud services. The 2022 version is based on a new high-level structure that is common to all ISO management system standards, making easy integration of ISMS with other ISO standards such as ISO 9001 and ISO 14001. A new risk assessment process has been included in the 2022 version based on ISO 31000 risk management standards allowing organisations to tailor their risk management strategies to specific requirements. Overall the revision 2022 is a more comprehensive and up-to-date standard providing greater flexibility and guidance for organizations looking to implement an effective ISMS.
Need assistance in achieving ISO 27001 certification, contact us by phone, chat or simply drop your query.
Bringing experience, expertise and leadership with virtual CISO to your organisation.
Securing your organization's data and customers' sensitive information associated with the business needs constant efforts along with the guidance of an expert executive-level leader called CISO(Chief Information Security Officer). It is not easy and affordable for all organizations to identify a security professional with expertise, experience and leadership skills to help in preparing and executing a successful security strategy.
Here a virtual CISO (Outsourced security professional) comes into the picture, who offers their expertise in designing or managing the organization's security strategy. This gives the organizations access to experienced cybersecurity, risk and compliance professionals at an affordable range.
Identifying an experienced and qualified CISO in today's competitive world is very challenging. Our virtual CISO can strengthen the IT Staff, set business supporting strategies, balance the administration and establish clear communications in the internal hierarchy of the organisation and stakeholders.
Where Virtual CISO is required?
Although vCISO is very important in designing and managing the security policies and strategies of an organisation, at a certain place their guidance becomes inevitable.
1. Planning of security audits, reviews and assessments.
2. Developing a new security strategy for threat management.
3. Getting compliance-ready.
4. Procuring new security components or expanding the network.
5. Recruiting or training the IT and security personnel.
6. Remediating the security incidents.
By employing a virtual CISO, one gets the benefit of advisory support from an industry expert familiar with the security challenges across a wide range of industries. Our virtual CISO can provide regular counselling, project-based assistance, and guides in making business-critical decisions.
Key responsibilities of virtual CISO
Our virtual CISO aims at providing the security program leadership to guide the internal teams. Virtual CISO provides both the expertise and experience required for strategically leading the cyber security strategy. The key responsibilities of a virtual CISO are -
1. Implementing and Overseeing a Cybersecurity Program.
2. Planning of security audits, reviews and assessments.
3. Expert assessments on threat analysis and compliance.
4. Consultation for developing effective cybersecurity and resilience programs.
5. Aligning Cybersecurity & Business Objectives.
6. Reporting on Cybersecurity.
7. Monitoring Incident Response Activities.
8. Managing Business Continuity & Disaster Recovery.
9. Promote a Culture of Strong Information Security.
10. Managing Vendor Relationships.
11. Utilizing Cybersecurity Budgets Effectively.
12. Facilitating security integration into business strategies.
13. Assisting with the interpretation and integration of security program controls.
14. Serving as industry expert and security liaison to auditors and examiners.
Our virtual CISO helps our customers with effective advisory strategies and controls to build an upright cyber security structure.
Book your call to get your virtual CISO appointed.
Managing the business risk, accelerating innovation and security at the same time
A cyber security strategy is very much important for any company to take a proactive approach to security instead of reacting to mishaps. The strategic security solutions help businesses to understand and tackle cyber risks and opportunities cost-effectively and with minimum disruption.
Securing the company's cyber security is very much important in the ever-rising threats in the industry. Determining what to protect while following the legal guidelines and regulations. Forming a strategy to manage and mitigate cybersecurity risks to systems, people, assets, data and capabilities.
The only method to stay safe is to detect and prevent the attacks before they succeed in disrupting the system. Once the system is compromised the threat actors can destroy it completely. Data misuse can put all the associated clients into a financial threat. Loss of trust, reputation, finance and many many other losses that can't be repaired.
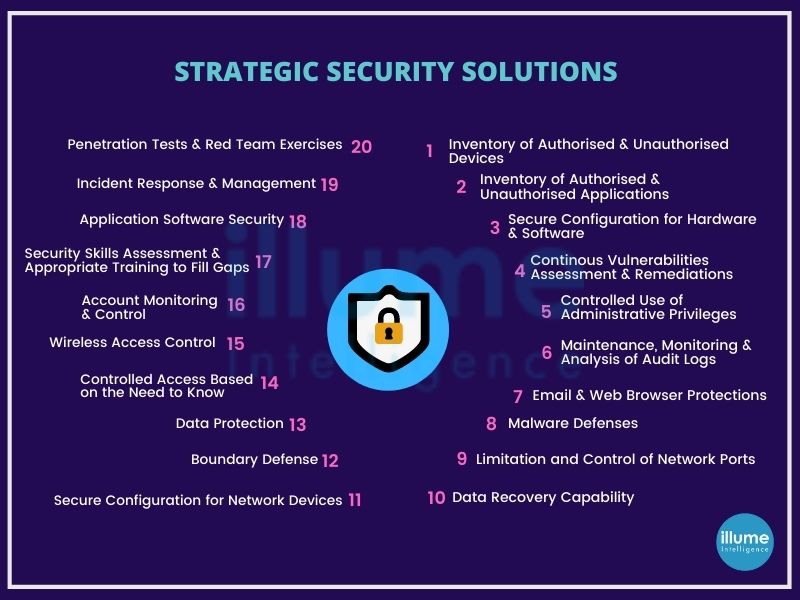
How do we implement strategic security solutions?
Defining the cybersecurity goals and choosing efficient strategies for them is the first step we take. Our experienced team provides strategic and tactical advice and helps in inducing security into the IT system to attain the company goals. We help the organisations to adhere to the local governance, certificates and regulations.
We design our strategies as per the requirements and the specifications of the organisation's IT network. Regular or periodic monitoring is scheduled depending upon certain factors such as the criticality of the business, nature of the business, size etc.
What to consider when implementing the information security strategy?
1. Constantly changing factors in an organisation - Lots of new technology integration keeps on happening in the organisations.
2. Building the strategy from bottom to top - Defining the security scope, obligations, risk and complexity. Developing a holistic view of the needs before starting.
3. Comprehensive security strategy considering people, processes and technologies - The security program includes both governance and management activities.
Guarding requirements, whether it is property, wealth or business had always been there for humans. Implementing strong strategies, and regularly updating and monitoring them can help in protecting the business. The risk can not be eliminated completely but with strategic security solutions, one can protect against most of the threats.
Have you implemented strategic security solutions in your organisation? How safe is your business?
We can help in securing what is important for you. Let’s connect and get secured.
Preventing against Human hacking
Humans are the weakest links in any security strategy. Understanding the security exposure in any organisation is very important to prevent possible social engineering attacks. Human beings are very unpredictable, depending upon the circumstances they are in. The security professional needs to design the security assessment accordingly.
Social engineering is the usage of manipulation techniques by the threat actors exploiting human error and gaining access to private information, spreading malware, ransomware etc. These attacks can be done online, in-person and in other ways.
Social engineering assessment or employee vulnerability assessment comes into the picture to prevent social engineering attacks. Social engineering is dangerous because it is not the vulnerabilities in applications or systems. Mistakes or access given through legitimate users are less predictable. Social engineering simulation is a simulated test aiming to measure the information security awareness levels of the organisation's employees by exploiting the natural behaviour (trust, friendliness, assumptions, biases etc) of the employees.
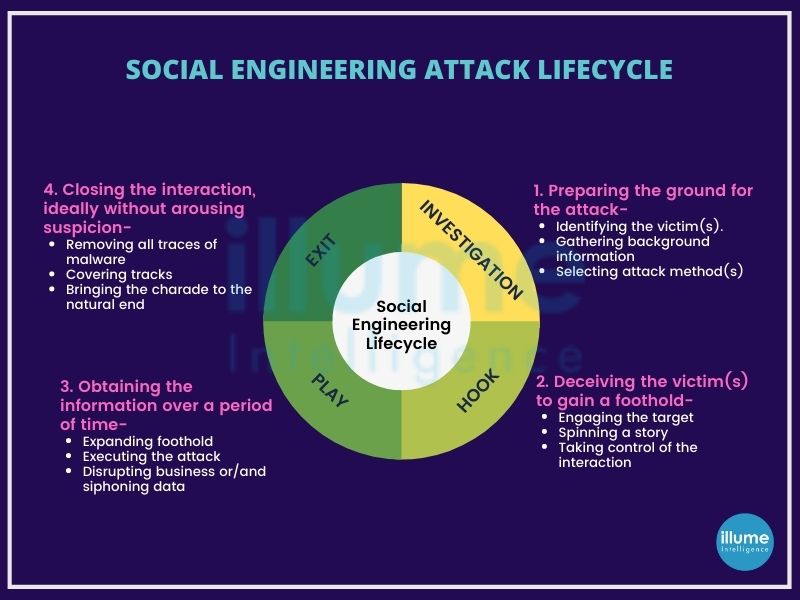
How is social engineering assessment or Employee Vulnerability Assessment done?
The team assessing the system attempts direct contact with the targeted employees, either through phone calls or in-person or through restricted access.
The assessment employs psychological manipulation for deceiving people into performing adverse actions like clicking on fabricated links, opening infected attachments, sharing personal details or divulging confidential information. The social engineering team develops familiar-looking fabricated content to lure the users and then make them take unwarranted actions.
We assist in assessing the ability of the organisation's system and employees to detect social engineering attacks. The assessment is conducted in close coordination with the concerned person in a controlled manner. The assessment may involve following steps:
1. Gathering Information - The assessment team researches the target organization to understand its structure, employees, and security policies.
2. Crafting Attack Scenarios - Our team creates scenarios that mimic real social engineering attacks, such as phishing emails, phone calls, or physical attempts.
3. Executing Simulated Attacks - The team performs the social engineering attacks on employees, monitoring their responses and actions.
4. Analyzing Results - The results of the assessment are analyzed to identify weaknesses and areas of improvement.
5. Providing Recommendations - The assessment report includes recommendations for strengthening the organization's defenses and enhancing employee awareness.
A detailed report on the analysis along with suggestions to improve the security of an organisation is provided after the assessment.
How to prevent social engineering attacks?
One can not guarantee the prevention of social engineering, but some precautions can help in strengthening the organisation's security system against social engineering attacks.
1. Don't open attachments or emails from unknown or suspicious sources.
2. Usage of multifactor authentication can help in avoiding unauthorised access.
3. Be careful with tempting offers. Hackers spoof the sender to make the message look real and offer tempting deals.
4. Antivirus or antimalware software should always be up to date.
Finding flaws in the security regularly like a hacker using Cyberattack Simulation
With the increasing cyber attacks, it has always been a worry for professionals to provide 360-degree protection. Cyber attacks are becoming advanced and audacious day by day leading to financial threats, writing malicious code and lodging political protests. The impact of cyber attacks is unimaginable as the intruder can misuse the system or the stolen data the way they want.
Understanding the loopholes present in the security from a hacker’s perspective can only help the technical team to remove them. Knowing the real threat's an organisation faces, will help in preparing against sophisticated cyber attacks. Illume can enlighten you on this. A cyber-attack simulation exercise is capable of exposing known and unknown vulnerabilities by testing against real-world threats.
Utilizing our customized, tested and proven methodologies to identify shortcomings in physical security, personnel and procedural security and system and application-level security.
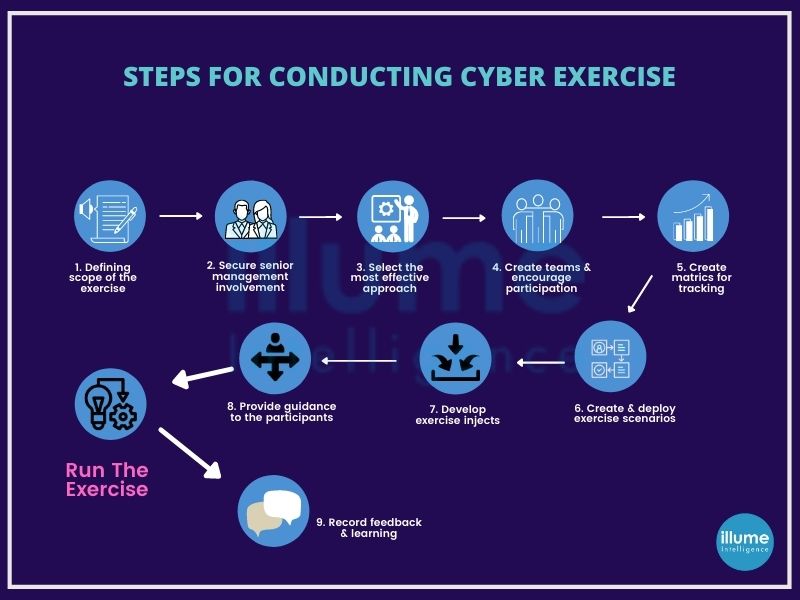
What is cyberattack simulation?
Cyberattack simulation is software used to mimic real-world security threats to find vulnerabilities in the security system of a business and prepare incident response plans. These simulated attacks may send fake phishing attacks to employees or may attack the organisation's web application firewall. It may use automated simulations for continuous testing using AI-based threat logic to ensure the team is always on guard.
These simulations are designed as per the client's requirements. These are available all the time but can be used periodically as per the requirements. No matter whether a manual method is used, it is hard to assess the efficacy of security operations. Our customized software can simulate various threats over various environments to help our clients prepare and evaluate their security. The cyberattack simulation exercise includes phishing, malware compiling and binding, SQL injection, DDOS and other exploits that generate deeper insights for the CISO/CFO/CEO, to strengthen the security of the organisation.
How do we conduct cyberattack simulations?
Thinking like threat actors to identify the exploitable options. We employ the information available on open sources, to understand the hacker's view. Going beyond the traditional penetration testing to understand the importance of the tactics, assets, locations and other factors for a hacker. This helps in easily identifying the security gaps in the organisation's arrangement for protecting the most valued assets. We look at every possible attack surface as anything can be exploited by hackers.
How about understanding your threat position? Let's arrange a confidential cyberattack simulation now.
Identifying your small to severe security risks with vulnerability assessment
Vulnerability assessment as the name suggests is a process of systematically reviewing security weaknesses in an information system. Identifying the system if susceptible to any known vulnerabilities assigns priorities to them for addressing. Recommends remediation or mitigation, if and wherever needed.
This assessment provides the in-depth knowledge, awareness and background to understand and respond to the threats present in the environment of any organisation.
Types of vulnerability assessments
There are several types of vulnerability assessments, which includes -
1. Host assessment - Assessment of servers against vulnerabilities that may lead to severe attacks when left unattended.
2. Network and wireless assessment - Assessment of policies and practices to prevent unauthorized access to network resources.
3. Database assessment - Assessment of databases for vulnerabilities and misconfigurations, identifying rogue databases or insecure environments and classifying sensitive data across an organization's infrastructure.
4. Application scans - Assessing the web applications and their source code by scanning on the front-end or static/dynamic analysis of source code.
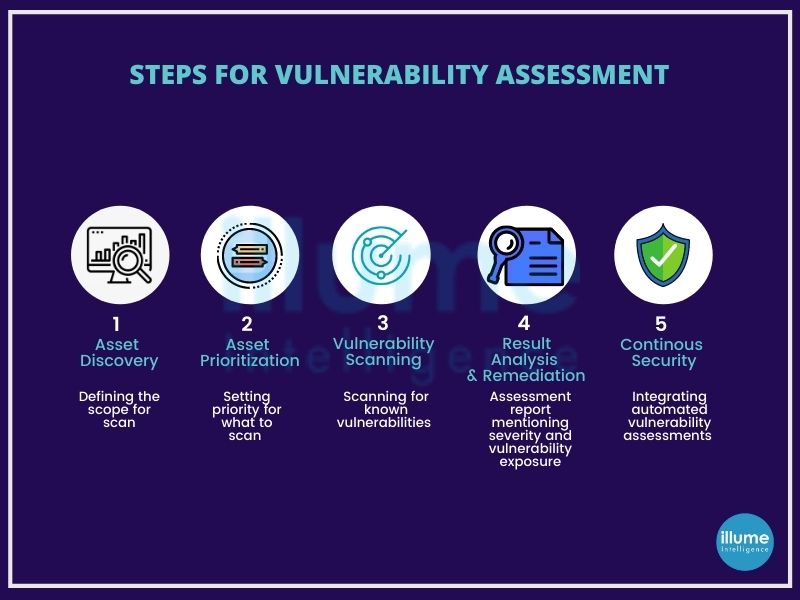
Knowing exactly how vulnerable you are is always a better choice than assuming that you are vulnerable to a cyberattack because with assumptions you can not plan the prevention. Hence a vulnerability assessment helps in testing some or all the systems as per the assessment goal and generates a detailed vulnerability report. Which can then be used to fix problems and avoid intrusions.
Benefits of conducting regular vulnerability assessments:
1. Identifying the loopholes in the security before attackers find them.
2. Ready inventory of all the network components with their purpose and system information. This also includes vulnerabilities associated with a specific device.
3. Ready inventory of all the devices in the organisation with the planning of upgrades and future assessments.
4. Risk assessment of the existing risk on the network.
5. Easy establishment of the risk/ benefit curve for optimized security investments.
How is vulnerability assessment done?
The vulnerability assessment process consists of the following steps:
1. Identification - This phase focuses on listing the application's vulnerabilities. Scanning all the network components using automated tools and manually evaluating to make a complete list of vulnerabilities present.
2. Analysis - Identifying the source and root cause of the vulnerabilities identified in the previous phase.
3. Assessment - Once the risks have been identified, it is important to prioritize them according to the impact and risk associated.
4. Remediation - All the experts from the security, operations and development join hands to remediate each vulnerability.
Once the process is completed doesn't mean that it is done forever. Every day new vulnerabilities are getting detected hence it is advised to repeat the step at regular intervals.
What after vulnerability assessment?
The Vulnerability report generated is a documentation of the risks in the organisation's network, that need to be worked upon with the exerts for determining which vulnerabilities require a simple patch and which need to be addressed seriously with in-depth remediations.
This will lead to the next steps in the p[rocess like penetration testing, vulnerability management and overall risk management before setting goals for the next vulnerability assessment.
Vulnerability assessment informs on the weaknesses and loopholes present in the security of an organisation and guides in mitigating the risks emerging due to these weaknesses. For reducing the security risks, vulnerability assessment is a good choice. We provide a thorough, inclusive assessment of hardware and software. It is advised to conduct a regular assessment of the organisation’s system to assure safety from the attacks.
Securing your network by finding the vulnerabilities, like a hacker
Red Team testing as the name suggests is the assessment of the organisation network by trying to hack it. Red Team is the group of professionals responsible for emulating a genuinely malicious threat actor trying to break into the systems.
Real-world hackers don't follow any rules and methods, for exploiting the limitations of any testing programs. They will deploy any method to gain access, seek a point of entry for a successful breach. At times their passive attacks may exploit the organisations for a long time as they remain unnoticed.
A commonly employed method to breach an organisation's external security is combining social engineering and phishing. There are many ways to breach the first line of defense that depends on the human factor. Once the hackers get in they can steal sensitive data, deploy ransomware or exploit the organisation's resources.
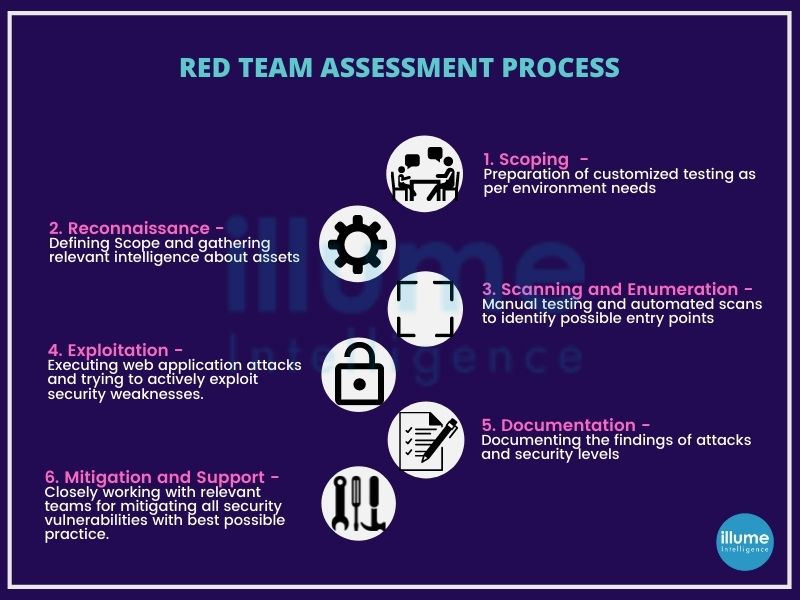
With the increasing size of the organisation, the attack surface also increases and the difficulty to secure and monitor all the endpoints and users. It may be assumed that penetration testing is a great method to secure services, but it often focuses on a specific asset and has a defined scope.
Red Team Testing vs. Penetration Testing
Red Team testing also known as Red Team Security Testing is often confused with penetration testing, but pen testing is only a part of red team assessment. Red team operations have broader objectives than penetration testing.
These assessments are designed to emulate a more real-world scenario, with detailed analysis and defensive strategies. It also includes evasion and persistence, privilege escalation, and exfiltration. The Red team will test the organisation's detection and response capabilities.
How does Illume's Red Team work?
Our Red Team testing methodology covers methods to attempt real-time attacks on an organisation. We follow the ATT&CK Framework, which comprises of the knowledge base of adversary tactics, techniques, and procedures (TTP) based on real red and blue teams’ actual experiences.
The methodology has the following steps -
1. Reconnaissance - This includes Scanning of several areas of the environment to determine interconnecting vulnerabilities and exposure.
2. Payload & Delivery - It is the ability to deliver a malicious payload of malware, ransomware, and viruses across parts of the environment leveraging email, social media, and web content as a rogue delivery tool.
3. Exploitation - This helps in finding the most susceptible areas to the risks in the environment.
4. Installation - This is to locate the scope of adding rouge devices, including WIFI, servers, and Internet of Things devices, without being detected across several parts of the environment.
5. Command & Control - Locating the endpoints and servers which can receive rouge communication instructions from the hackers.
6. Actions on Objectives - setting objectives to find if the response capabilities and defence mechanisms are working as expected across the environment.
7. Post-Engagement Reporting - The post-engagement report will cover remediation recommendations, including improvements to existing adaptive control and response capabilities, security measures, and incident response protocols.
The Red Team security assessment is a powerful technique for identifying the security vulnerabilities of any organisation. It will expose vulnerabilities, hidden from the organisation and mitigate them. Our Red Team assessment will enhance your organisation's security by uncovering the potential vulnerabilities to level up your security as expected.
Preventing your data and services on the cloud with the latest techniques
Every business looking for expanding, selects cloud services for switching from on-premises hardware and technology. The cloud gives access to more applications, better data accessibility, effective team collaboration and easier content management.
Putting the data on the cloud brings many security challenges as well hence cloud security comes into the picture. Cloud Security or Cloud Computing Security is a collection of security measures designed to protect cloud-based infrastructure, applications and data. This ensures user authentication, device authentication, data privacy protection, data access control and resource access control. This also protects against DDoS, malware and other hacking attacks. It also supports regulatory data compliance.
Due to the features provided on the cloud, more and more IT professionals are concerned about shifting more data and applications to the cloud. Thus making cloud security more crucial. Preventing leaks and data theft is critical for maintaining a customer's trust and protecting his assets.
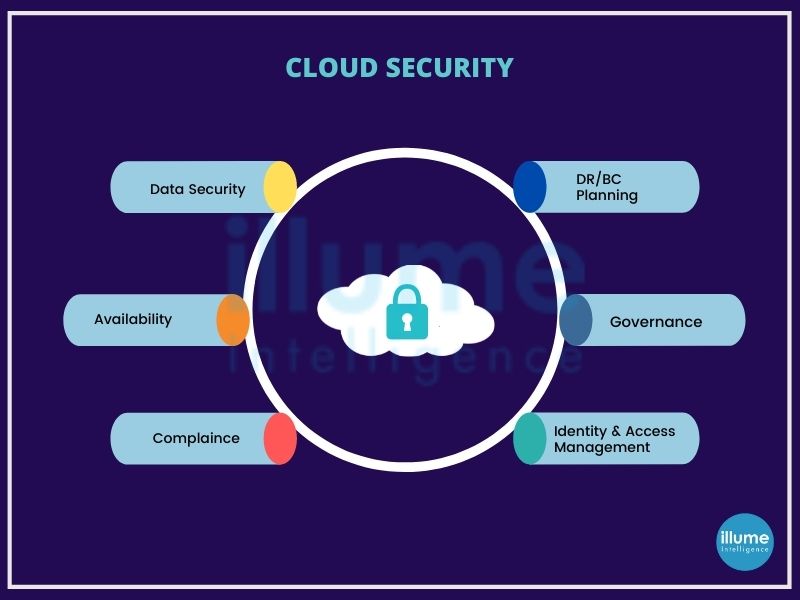
What does cloud security include?
Cloud security services encompass a variety of security measures, which may include:
1. Identity and access management (IAM) - Managing user identities, authentication, and access controls to ensure only authorized individuals can access cloud resources.
2. Data encryption - Encrypting data both at rest (stored in storage systems) and in transit (during transmission between systems) to protect against unauthorized access.
3. Network security - Implementing firewalls, intrusion detection/prevention systems, and secure network configurations to safeguard cloud networks from threats and attacks.
4. Vulnerability scanning and assessments - Regularly scanning cloud systems for vulnerabilities and conducting assessments to identify and address security weaknesses.
5. Security monitoring and incident response - Continuously monitoring cloud environments for suspicious activities or security breaches, and responding promptly to incidents to mitigate potential damage.
6. Security information and event management (SIEM) - Collecting and analyzing security event logs from various cloud resources to detect and respond to security incidents.
7. Security audits and compliance - Conduct audits and assessments to ensure compliance with industry standards and regulatory requirements.
8. Disaster recovery and business continuity - Implementing backup, replication, and recovery mechanisms to protect against data loss and ensure business continuity in case of disasters or disruptions.
What to look for when selecting a cloud security service for your business?
Finding the right solution for cloud services is essential for data protection and the company's overall safety. A good vendor should know the importance of security in cloud computing and have a few main features to lower risk.
1. Data Leakage Prevention - Built-in secure cloud computing controls to prevent issues such as unauthorized access, accidental data leakage and data theft.
2. Strong Authentication - Multi-factor authentication for all kinds of users and single sign-on to provide secure access to the users.
3. Data encryption - Security for both the data in rest and data in transit should be ensured.
4. Threat Detection - Automatic threat detection for unwanted behaviour and identity threats along with instant reporting.
5. Compliance Support - The services provided should be under regulation and compliance.
6. Integrated Security - The tools used by the service provider should integrate with your applications for a better user experience.
We aim at providing all the services you need at one point and for that, we may collaborate with some vendors to ensure your business security, integrity and continuity.
We protect our clients through a combination of threat intelligence, robust architecture and an efficient automated service delivery model. Testing and bringing the latest security features into our solutions to meet the client requirements with compliance is our agenda.
How secure is your present security system? Are you running your business from the cloud but still not sure about your data security? Maybe it's time to revise your cloud security services for enhanced business continuity.
Auditing to remove unwanted policies and hardening servers as per CIS Benchmarks
Protecting systems and data is crucial for every organisation to ensure security from cyber attacks. System hardening or Server hardening is a process of securing a system’s configurations and settings to reduce IT vulnerability. It is done to minimize exposure to threats and mitigate possible risks.
The operating systems are designed to provide convenience and ease of use over security. The IT security team may have a different opinion on this. But they don't have to worry as there are steps that can be taken to harden a system and eliminate as many security risks as possible. For example, the basic one is to change the vendor's default username and password. Default access codes can be easily hacked as they are available on open sources. The other examples include removing unnecessary services from the configuration settings, applying firewall rules, enforcing password complexity, system idle time outs and more.
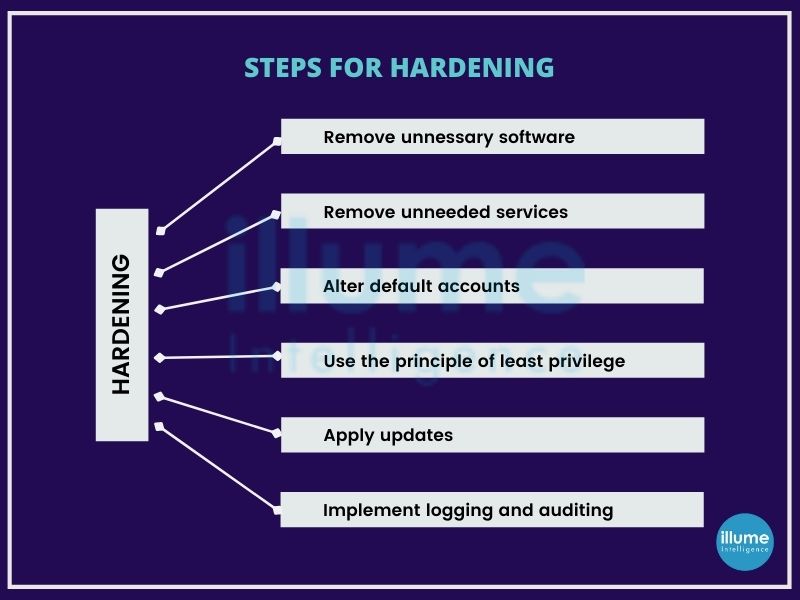
Securing systems is crucial for IT infrastructure. Every organisation has one or multiple servers connected to the internet. Business continuity and credibility depend on the security of data stored in these devices.
We have a qualified team to support the clients' infrastructure management needs. Implementing hardening measures at multiple levels is required for ensuring reliability and uptime for the business. Some of the standard practices that we follow are -
1. Physically securing the server facility.
2. Separating the database server from the application server.
3. Hardening of webserver and application servers.
4. Security audits using tools.
5. Enforcing IP-based restrictions.
6. Implementing server password policy.
7. Limiting access.
8. Isolating production environment.
9. SSH hardening
10. Monitoring and maintaining infrastructure.
Why is Server Hardening important?
When talking about server hardening it is not only required for security but compliance as well.
Server hardening is an important factor in protective technologies like Firewalls and EDRs. If the server is not hardened properly no amount of money spent can secure the server.
All the major compliance frameworks have server hardening as mandated. All compliance frameworks consider CIS Benchmarks as the best practice. Hence when looking for compliance this becomes essential.
If you haven’t yet established the system hardening routine for your organisation, it is a good time to start now. We can help in building your policy according to the CIS Benchmarks, followed by implementation and maintenance.
Discovering the security flaws in your VoIP infrastructure to secure from external attacks
VoIP (Voice over Internet Protocol) has become important for businesses and hence a good option for the attacker to exploit whenever left unprotected. Unlike other IT infrastructure, VoIP is also subjected to risks like interception, caller ID spoofing, Denial of Service (DoS) etc.
VoIP security is not only about call encryption, it is the level of trust that's conveyed over the text and voice network. If it is compromised, it can become a huge threat by carrying out more attacks.
A VoIP security assessment is a manual assessment of the security of the VoIP infrastructure. It identifies the vulnerability in the VoIP system to reduce the risk of financial loss or unauthorized access.
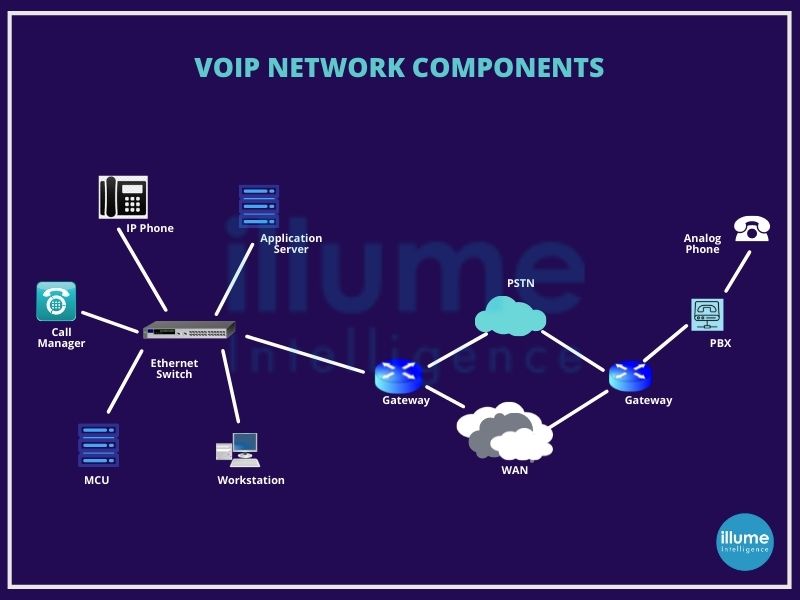
Securing a VoIP network is important for every organisation in a world full of uncertainties. Our team accesses the VoIP infrastructure to determine the risk of all the possible network infrastructure attacks. Evaluating the different VoIP components from the security perspective and capability to ensure they maintain confidentiality, integrity and availability. VoIP security assessment generally includes-
1. Application-level vulnerabilities
2. Extension enumeration and number harvesting
3. Default credentials testing
4. Voicemail security testing
5. Traffic capture and eavesdropping
6. Caller ID spoofing
7. Identifying DoS vulnerabilities
8. Design and configuration issues
How is VoIP security assessment performed?
The general approach is to gain access to the network and identify the vulnerabilities which are explained in the steps below -
1. Information gathering - Gathering all the possible information about the IP of servers, VoIP devices, PSTN's signalling system etc.
2. Enumeration - Gathering information about services running in the environment.
3. Vulnerability analysis - Identifying the vulnerabilities in the devices, services and infrastructure.
4. Attacking - Exploiting the vulnerabilities to gain access and accessing the scope of attacks
5. Report and Support - Presenting a detailed report on the vulnerabilities found with their strength, risk and standard associated with the security. Assisting in deploying the mitigation strategies as suggested in the assessment.
It is important to resolve the flaws as early as possible as the slightest negligence can result in severe financial and property losses. Application of required regulations for every business using VoIP infrastructure.
Are you still using unprotected VoIP services for your business? We can help in securing your VoIP infrastructure located anywhere in the world. Contact us via call or write an email and we will be there for assistance.
Know the vulnerabilities in your network security
A network security assessment is an audit designed to seek vulnerabilities in any network. A network with weak security can be compromised easily resulting in harming the business operations and leaking sensitive data. The vulnerabilities can be due to old software, viruses, malware or coding flaws in applications.
securing the network should be the top priority of any organisation. It's obligatory to carry out vulnerability assessments to comply with compliance and regulatory standards like HIPAA, PCI DSS etc.
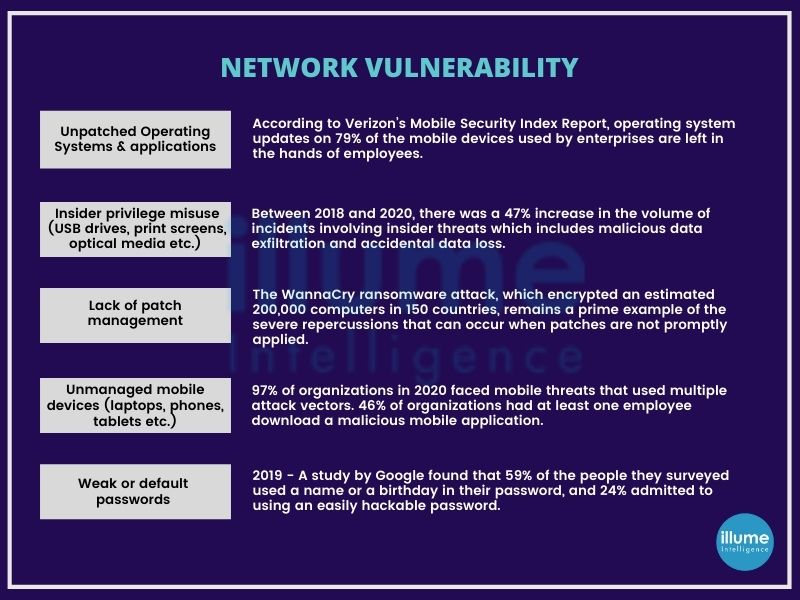
Network VAPT assessment helps in identifying vulnerabilities lying in the physical layer and network design of the infrastructure. It is capable of finding the loopholes and the vulnerabilities caused so that the experts can remediate them quickly before being exploited by the threat actors.
Network Vulnerability Assessment helps in finding security flaws from both inside and outside the network whereas Penetration Testing looks for the vulnerabilities that can be exploited to gain access to the network.
What are the goals of the Network Security Assessment?
1. Determine the ability of attack vectors.
2. Identifying the low-risk vulnerabilities could be exploited to impact more.
3. Identifying flaws that are hard to be tracked by vulnerability scanning software.
4. Auditing and analysing the impact of attacks if successful, from inside and outside the network.
5. Testing the capacity of network defenders to detect and respond.
How do we perform a Network vulnerability assessment?
We perform internal and external network penetration testing using network vulnerability assessment with the black box and grey box testing. While auditing external and internal network testing are very important to make the system foolproof.
1. Assessment scope - Depending upon the requirements we outline the assets, services, devices and IP addresses for scanning.
2. Information gathering - Gathering information on all possible assets using the open-source tools.
3. Scanning for vulnerabilities - scanning the target with the manually tuned automated scanning tools.
4. Analysis - Analysing the findings for filtering false positives and assigning priorities with the severity of the impact.
5. Reporting - Comprehensive report on the methods employed, findings, remediations and mitigations according to the findings.
We suggest performing network vulnerability assessment and penetration testing every 3 months (monthly in case of regulations) and each time after introducing changes into the network.
Stay ahead of the emerging security threats and keep your data protected without wasting your money. Our team of experts can help in securing your network.
Ensuring the safety of your network against the threats, that may originate from IoT devices
The Internet of Things includes all the electrical devices, vehicles, and security devices that can connect to the internet for taking commands to operate. These devices are often made by different vendors using different techniques and methods. Ignoring their vulnerabilities can lead to severe havoc on your security.
IoT penetration testing is security testing used to test the insecurities posed by connecting IoT devices to the organisation’s network. It means conducting vulnerability assessment and penetration testing of all the IoT devices on the network. This ensures all the security flaws are identified and resolved. The connected devices are contributing to the growth of business and hence are being frequently targeted by the threat actors.
How can IOT penetration testing help?
The Center for Internet Security (CIS), recommends best practices for securing IT systems and data. Large organisations need to implement organizational CIS controls.
1. IoT devices have multiple interfaces making them vulnerable. Penetration testing can help in securing the input methods.
2. Network infrastructure interconnecting to these devices is at the risk of exploitation. Automated tools and manual penetration testing methods should be utilised to secure network infrastructure and protocols.
3. Scanning proprietary programs are important to secure the entire system architecture.
How do we perform IoT penetration testing?
Our team of experts helps you in strategically building and implementing an IoT ecosystem safe from threat actors. We use the most progressive penetration testing techniques to identify, evaluate and analyze vulnerabilities across the network ensuring the regulations and compliances.
We follow the below testing methodologies-
1. OWASP Testing Guide
2. NIST SP 800-115 Technical Guide to Information Security Testing and Assessment
3. PCI DSS Information Supplement
4. FedRAMP Penetration Test Guidance
5. ISACA's How to Audit GDPR
Every organisation needs to build a comprehensive security defence strategy with governance by regulations and compliances. With the help of penetration testing, the business can get a deep insight into the risks and vulnerabilities to implement the best-suited defence system.
How safe is your network with the IoT devices connected? We can help in securing your network as an IOT penetration testing and strategising partner leading to business growth.
Securing the most critical network of the organisation and strengthening bonds with clients and stakeholders
WiFi is a wireless method of establishing network connections using radio waves. Due to its nature connecting WiFi has been a lucrative option for threat actors to penetrate organisations' networks. IoT devices have also enhanced the risk of cyber attacks.
Wireless penetration testing plays a role in identifying the potential vulnerabilities in the wireless network environment. It attempts to penetrate the network using any vulnerabilities to gain access. This helps in creating mitigation strategies for enhancing security.
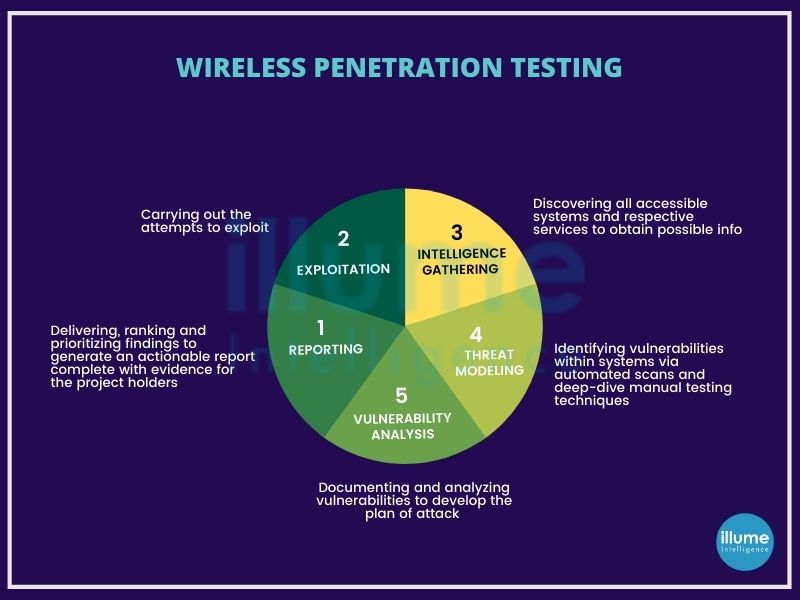
What is the need to protect wireless networks?
Wireless networks enhance the organisation's performance and connectivity, however, they are also targeted by the threat actors to disclose the organisation's critical data. Organisations are required to follow certain regulations to do business by granting safety to the organisation's and customer's data.
Testing the wireless network can help in addressing the issues related to security controls along with real-world vulnerabilities. It will help in strengthening the security posture of the organisation as well as increasing customer trust and brand value.
How do we perform Wireless Penetration Testing?
The wireless penetration testing at Illume Intelligence comprises various modes of analysis to identify vulnerabilities, resilience against threats and responses against attacks. We inculcate methods developed by Penetration Testing Execution Standard (PTES) and Information Systems Security Assessment Framework (ISSAF), suiting best to the organisations' needs:
1. Reconnaissance - Creating a comprehensive map of all the network components based on available systems and services.
2. Threat modelling - Combining automated scans and manual testing to determine the exposure to threats.
3. Vulnerability analysis - Documenting the analysis and development of the attack plan so that nothing skips.
4. Exploitation - Attacking the system to reveal the vulnerabilities impacting the network's security.
5. Reporting - Providing a complete report on the methods, processes, results etc, for better decisions on implementing adequate solutions.
How secure is your wireless network? We can be your reliable security partner enhancing your business security and growth.
Migrating your critical data and applications with efficiency for better performance
Migrating data centres and applications have never been an easy task for any organisation. Maintaining the complete log of securities and policies and applying them perfectly in the new location is a very tedious and complicated task. Even the slightest mistake can lead to serious issues or outages.
The organizations grow and the current system no longer serves the organisation's storage needs forcing them to a data centre and application migrations. Data centre migration caters to the need for bigger infrastructure for an organisation. It helps in empowering the organisation to improve productivity, efficiency and agility. By shifting the workload to the new and efficient platform one can get the following benefits-
1. Scaling and growing the business
2. Supporting more business needs
3. Digital transformation of the organisation
4. better customer relations
5. Improved performance and market value
How to plan a successful data centre migration?
The data centre migration process includes the below steps-
1. Assessment of current system - knowing about the current system in place, evaluating the application supported, servers, operating systems etc.
2. Forming strategy for migration - Documenting the requirements like equipment needed, connectivity diagrams, cooling infrastructure, space utilization and power requirements.
3. Selecting the location for migration - Based on the requirements select the destination for migration.
4. Planning and recording - This includes the design and review of the steps of the migration process.
5. Development - After planning, development begins in this phase as required to support the physical infrastructure. This is important to avoid last-minute changes.
6. Validation - This phase validates the plan and the components through the cool-down process. It also includes business validation making sure all stakeholders are aware of migration.
7. Migration - Finally the migration begins here. The critical applications and components are migrated as per the strategies made.
8. Post-Migration verification - It is required to verify the migration happened correctly and all the components are working fine to their capacity.
How do we implement the data centre migration successfully?
We at Illume Intelligence follow the industry's best practices for data centre migration -
1. Making a strategy - Migrating the data centre is very critical hence strategy plays an important role. Designing the strategy according to the organisation's needs is very important.
2. Planning a budget - Planning the budget before starting the process with the risk of exceeding in consideration.
3. Defining the purpose - Understanding every application and component's purpose and status. The power specifications and configurations are very crucial.
4. Data backup strategy and replication - Taking a backup to avoid any kind of accidental data loss during migration.
Data migration enhances performance and competitiveness. Rigorous testing to confirm the proper functioning along with descriptive documentation for future needs is very important. Are you looking for a reliable data centre migration partner? You can trust us for your upcoming migration.
Strengthening your security with Firewall Security Testing and removing vulnerabilities
Firewall is the first line of defense in preventing cyber threats for any corporate network. Firewall security testing is the testing of the firewall done by pen testers similar to the threat actors for locating the vulnerabilities in the security method implemented or for deploying adequate security methods.
One can consider the firewall as the fencing around the periphery of the corporate network that secures against external threats and allows clients and trusted vendors traffic to enter. This traffic is often secured with the key given to them for the security of the network.
Considering and maintaining a firewall as an important component for security as it protects against data breaches or theft, is important for the organizations safety.
It is important to understand firewall security before implementing it as a security feature for your organization. Firewall security is
1. A preventive technical security control system (hardware/software).
2. Automated protection preventing unauthorised access.
3. An important part of business continuity plan and defense strategy.
Firewalls have their own predefined rules and filters to determine incoming traffic, hence making it important to configure them properly to achieve the expected security.
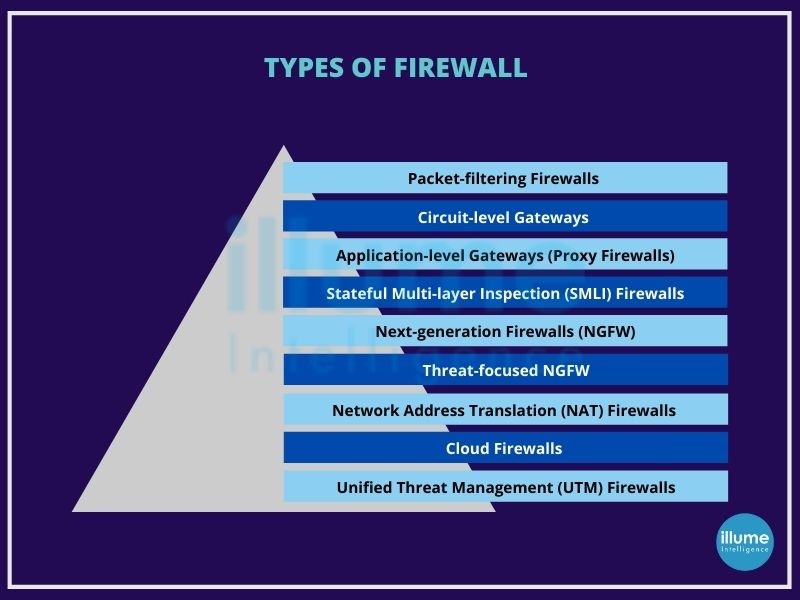
The idea behind firewall testing is to prevent unauthorized access to the secured network.
Why is firewall security testing needed?
Firewall security testing helps in identifying vulnerabilities in the network security posture. One can accordingly customize the security policies to ensure network security for intrusions.
1. Trust among stakeholders
2. Securing the company's network from malicious traffic
3. Proper configuration to remove the loopholes.
4. Regularly updating the system to keep it bug-free.
5. Proper functioning of the firewall rules.
Generally, firewall security testing (firewall penetration testing) includes locating the firewall, conducting traceroute, scanning ports, banner grabbing, access control enumeration, identifying the architecture, testing policies, firewalking, port redirection, internal and external testing, testing for covert channels, HTTP tunnelling and identifying firewall specific vulnerabilities.
How do we conduct firewall security testing?
1. Collect key information - Any security test can not be successful without complete information regarding hardware, software, rules, policies and risks.
2. Access Change Management - maintaining the proper record of changes done and changes required in the network.
3. Performing security checks on OS and physical components - evaluating the procedures deployed for the components and verifying the operating system passes standard rules.
4. Improving the rule base and decommissioning the old rules - decluttering the firewall rules by decommissioning old and inactive codes and rules.
5. Risk assessment and remediating - Analysing the risk and vulnerabilities. Making strategies to resolve and implement them.
6. Conducting regular audits - Penetration testing is required at regular intervals and specifically after implementing and changing.
Are you looking to implement firewall security testing? irrespective of the firewall implemented in your organisation, our experts will be able to find the vulnerabilities for suggest the best security measures required. Let's get your firewall secured.
Making applications better resistant to threats with Application Security Testing
Application security testing is the process of making applications more resistant to security threats, by identifying the vulnerabilities. The applications with flaws are susceptible to cyber threats no matter any security policy you apply. Hence the source code has to be secured by removing the flaws at the time of developing the applications.
initially, application security testing was a manual process. Due to growing threats, huge open source components and modularity of organisation's software, application security testing has become automated.
Application Security is not a single method or technology it is a set of best practices, functions, features etc. added to prevent and remediate cyber security threats for an organisation. Hence the organisations are using a combination of security tools.
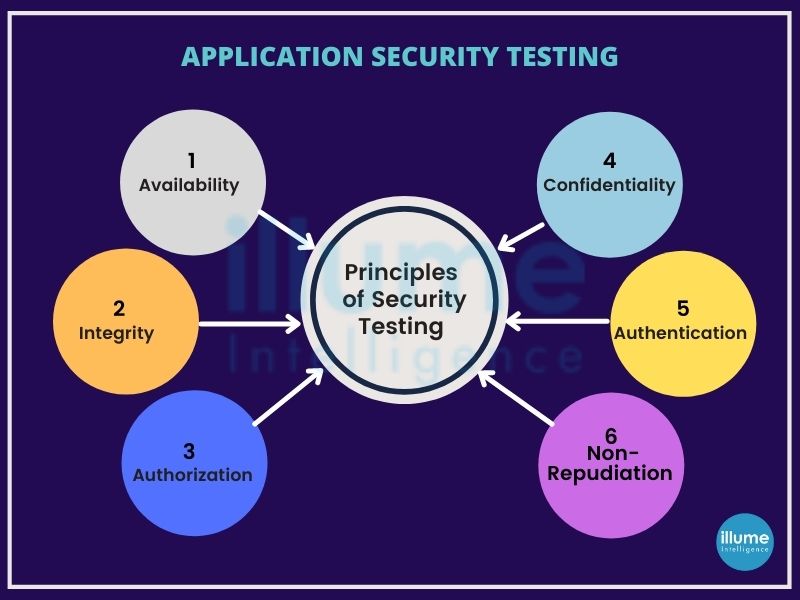
Application Security Testing tools
Experts divide the application security tools into two broad categories: security scanning tools and runtime protection tools.
Security scanning tools are used to remediate vulnerabilities in the development. At the same time, runtime protection is used in production and is considered as an extra layer of protection, not as an alternative to scanning.
Static Application Security Testing (SAST)
SAST tools are used for white box testing, used to test application source code, binaries for coding and design flaws, etc. This examines the static source code and reports vulnerabilities.
Dynamic Application Security Testing (DAST)
DAST tools are used as the black box testing, executing the code and inspecting for security vulnerabilities and architectural weaknesses by simulating external attacks.
Interactive Application Security Testing (IAST)
IAST is a combination of the above two to detect a wide range of security weaknesses. These provide the root cause and details of the vulnerabilities making it easier for remediation.
Software Composition Analysis (SCA)
SCA tools help in automated scans of third-party and open source components used. SCA makes an inventory of all open source software and scans them for vulnerabilities to remediate to resolve security threats.
Runtime Application Self-Protection (RASP)
RASP evolved from the SAST, DAST and IAST. They can analyse application traffic and user behaviour at runtime, to detect and prevent cyber threats.
Why application security testing is crucial?
Applications have become important for every website and business.
Insecure application is a threat for the business as well as for the user. A business providing an online service or product has to make sure the application behaves correctly for the users.
All businesses need solutions for a safe online experience for their brand. We help in securing the enterprises and keeping them safe with our application security testing services.
Malware analysis keeping you safe from the potential threats
Malware analysis is implemented for identifying and accessing the threats. Every day lots of businesses and personnel are falling prey to cyberattacks, many of them are in the form of malware. Malware is malicious software that is intended to harm the system. These have various forms like viruses, trojan horses, worms, spyware etc. They all are intended to gather information about the infected device without the knowledge or authorization of the user.
malware can be distributed through emails (phishing attacks), USB drives, software download from websites, etc. Disguising using the obfuscation methods to mimic legitimate files and websites for tricking the users. Once successful in attacking, it uses persistence techniques to stay undercover till the launch of the attack.
Malware analysis will help in understanding the behaviour and objective of the suspicious file or URL. It helps in detection, mitigation and limiting the scope of the potential threat.
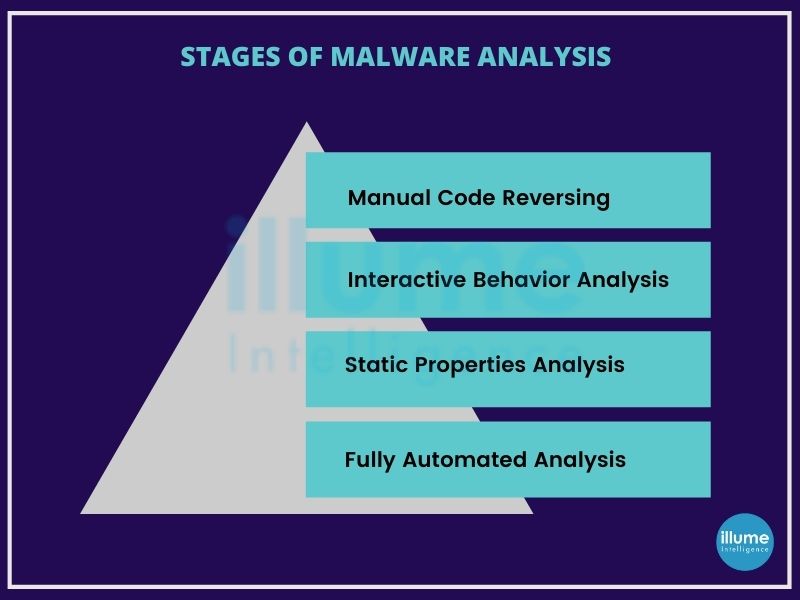
Types of Malware Analysis
When it comes to malware analysis, it can be done in three ways-
Static Analysis - Static analysis examines the files for malicious intent without running the code. In this kind of analysis technical indicators are identified like file names, hashes, strings, IP addresses etc to determine if the file is malicious or not. Some more tools can help in observing the working of the malware without executing the file.
As Static analysis does not run the code, sophisticated malware run-time behaviour can go undetected.
Dynamic Analysis- Dynamic malware analysis executes the suspected code in a controlled environment called Sandbox. This enables the professionals to observe the malicious software in action without the fear of an outbreak, infecting the entire enterprise network.
This type of analysis enables the threat hunters and incident responders to uncover the true nature of the malware with deeper visibility. One of the biggest advantages of using a sandbox is the reduced time for reverse engineering to discover the malicious code.
The threat actors are aware of sandboxes and hence can deceive by smartly hiding the code to stay in a dormant state until the specific conditions are met.
Hybrid Analysis -As the name says Hybrid analysis aims to utilise the best of both approaches. This can detect the malicious code that is trying to hide, and then extract all the indicators of compromise. The hybrid analysis is capable of detecting unknown threats.
How to safeguard against Malware infection?
Availing malware analysis services is important but prevention is always a better approach.
1. Keep the systems and applications up to date.
2. Stay alert to social engineering attacks that may compromise data.
3. Regular scans using antivirus and anti-malware solutions.
4. Follow security best practices like using secure connections, no file download from unknown sources etc.
5. Create regular backups for business-critical data.
With the list of malware being developed every day increasing rapidly, only staying alert and taking security measures can help. We provide malware analysis services to help the business stay safe. Our experts can handle any malware-related issues.
Boosting your applications' performance with static and dynamic code analysis
Since the beginning, there had been comparisons between the static and dynamic code analysis.
Static code analysis helps in finding the flaws in the program without executing it. Source code, byte code or application binaries are tested for security vulnerabilities. Static analysis tests the internal structure of the application.
Dynamic code testing the application in the running phase looks for the outside security vulnerabilities. It executes the software and validates the output with the expected outcome. The main idea is to confirm that the software product is working in conformance with the business requirements.
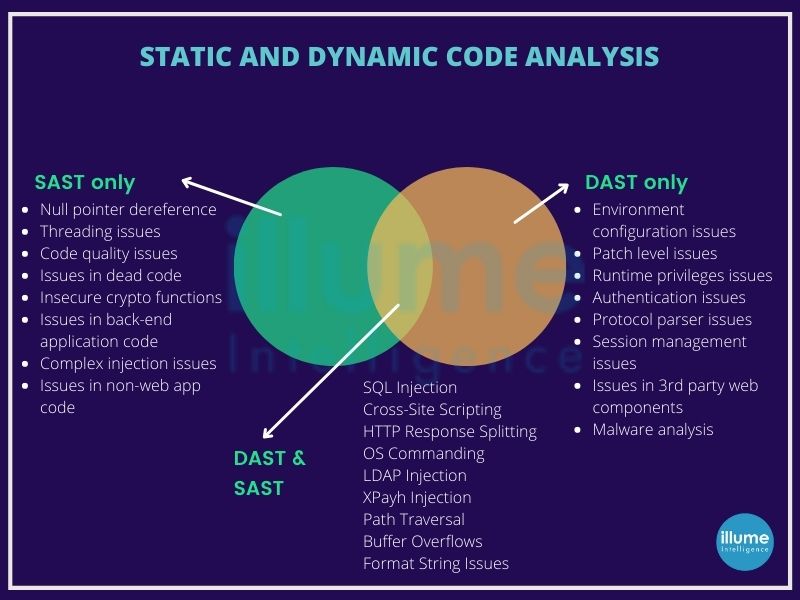
Static And Dynamic Code Analysis: which one to choose?
When it comes to testing the application, dropping any of these methods is foolish. For the complete testing of the application, both are equally important. Testing the code for its coding flaws as well as functional flaws makes it reliable, durable and compatible.
Various tools can be used to perform these testing but below are reasons that differentiate our testing from others.
1. Performance - Static analysis tool helps us to find the common coding pattern causing poor performance. This keeps us updated with the coding pattern with a better way out.
2. Reliability - Removing all the unwanted codes that may not be affecting the functioning of the code but may lead to future problems like downtime.
3. Security - Using industry-standard testing tools to ensure the security of the application.
4. Style - Maintaining a uniform coding style that is well suited to the testers for automation and manual testing.
Both Static and Dynamic code analysis have their benefits and shortcomings but when used in combination helps in strengthening the application, making it strong against security and mishandling threats. A well-tested code can be easily integrated with any other application as and when required in future and is well accepted by the universal standards and regulations.
Are you securing your applications with Static and Dynamic code analysis? We can help in securing your business.
Ensuring Web Services and API security in your organizations
APIs or Application Programming Interface and Web Services are the ways employed by the applications to exchange data. These are an integral part of software development as they connect and transfer data and logic over multiple systems and applications.
Web Service Testing is testing used for validating web services for functionality, reliability, performance and security of an API (Application Program Interface).
The web services and the APIs available in the public domain have to be tested rigorously, ensuring there are no loopholes, which may be exploited by the threat actors to harm the software or its users.
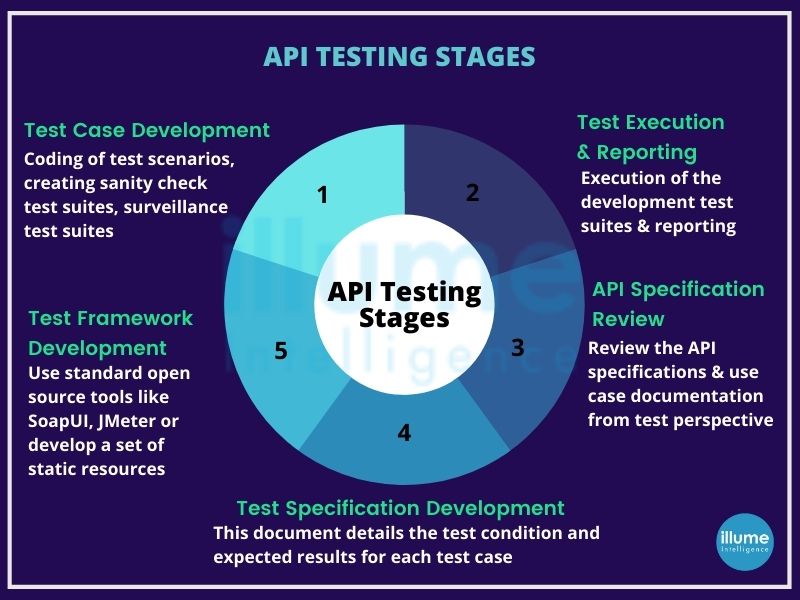
How do we do Web Services and API Security?
Adopting a hybrid approach for implementing the security, for Penetration testing wherein we follow the OWASP methodology and have included our specially designed test cases. We ensure an all-around approach for the testing. After the testing all the findings are documented, we extend our support to the developers and help them build secure coding practices ensuring API security issues from arising again.
1. Project Planning - Planning the flow of the project thoroughly for the proper implementation of the Web services and API testing to be processed seamlessly.
2. Customised Test Cases - Specifically designed test cases designed for the proper testing of the applications.
3. Automation Testing - Testing the application using the automation tools to ensure the testing is done from the industry-rated tools.
4. Manual Testing - Ensuring foolproof assessments by testing manually for the codes that may be surpassed by automation.
5. Reporting - Preparing the complete report by documenting everything for future reference.
Web Services and API testing has to be tested rigorously based on the protocols defined to ensure the safety of the user and network. The application based on APIs and Web services should be safe against hacking attempts. How safe are your applications?
Ensuring data protection with Mobile App security testing
The increased usage of mobile applications has also raised the concern for the safety of the user data. Delivering a perfectly working and secure application is crucial for user retention. Users must be updated about the data collection and how and why it is collected. The applications should only collect the necessary data.
Mobile app security testing is intended to ensure complete data protection. Using the set of tests it is tested against the vulnerabilities that may allow external threats to gain access into the device.
It is often hard for organisations to monitor their applications adequately to adapt security protocol to mitigate the emerging threats. Changing compliance laws also requires the organisations to strictly follow the mandates to protect the security of users (e.g. GDPR compliance).
Application security is of utmost importance for the organisation to develop and improve the business with the assurance that they are safe from potential threats. Lacking in implementing security will lead to severe issues like compliance violations, financial losses, reputation and trust loss from the stakeholders and clients.
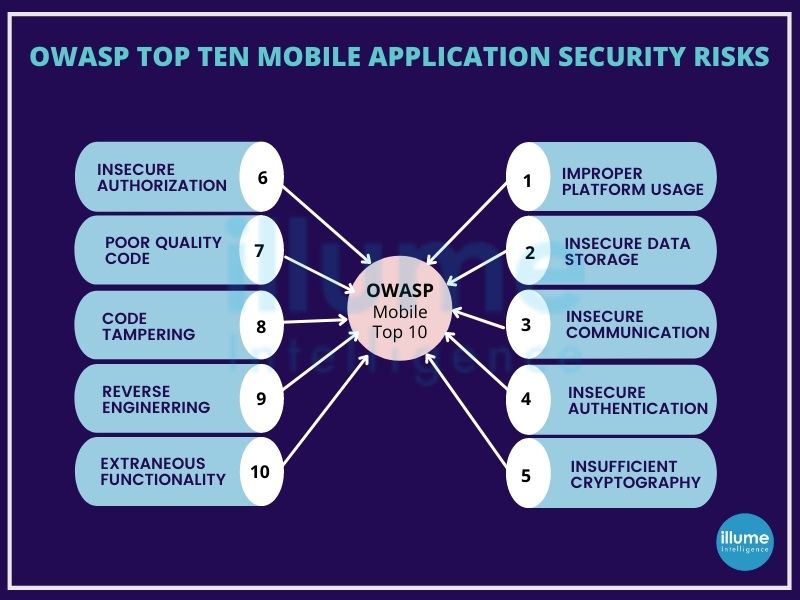
What are the mobile application security risks?
Mobile apps are designed focusing on providing the smooth interface and best functionality to users. They lack the capabilities to secure data transmission over the internet. Hence installing the antivirus app may secure the network and prevent the device but it failed to protect against a weak password or a poorly designed app.
There are common security lapses documented by the industry experts under the Open Web Application Security Project (OWASP).
How do we test mobile application security?
The important steps that we take while testing any app are below-
1. Application Threat Model - Creating the model by understanding the application requirements.
2. Performing Static and Dynamic assessment -Using automated tools and exploring the application manually to explore and execute the test cases in various scenarios.
3. Pen Testing - Exploiting the vulnerabilities to gain access and perform malicious activities.
4. Reporting and Mitigating - Reporting the bugs and mitigations to the client in detail.
Testing the mobile application is important for the developer as it takes lots of effort, money and time for the developer along with the security of the user using the application. Any misconfiguration may lead to serious losses on part of both parties.
With the increase of portable devices, the usage of applications will only increase in the future. Are you ready with the secure applications?
Designing the business cordial to the Enduser
Business logic vulnerabilities are often defined as the flaws in the design and implementation of an application that allows the threat actors to exploit the applications. These flaws generally occur as the developers fail to anticipate the behaviour of the end-user using the application.
Business logic is intended to enforce the rules and constraints defined at the time of designing the application, preventing the users from doing anything that may negatively impact the business. These logic-based vulnerabilities can be extremely diverse depending on the application and its functionalities.
Bugs or flaws in the logic can allow the attackers to outwit these rules. They might exploit by making arbitrary changes in the user data or may pass unexpected values to the server-side of the application forcing it to do unexpected tasks.
The impact of business logic vulnerabilities can be huge. These flaws in logic should be fixed even if the developers can't figure out, how these can be exploited.
Business logic testing or application logic testing, for testing the flaws in a multi-functional application requires unconventional methods. It is not possible to test these vulnerabilities through automated tools, hence it's done by a person.
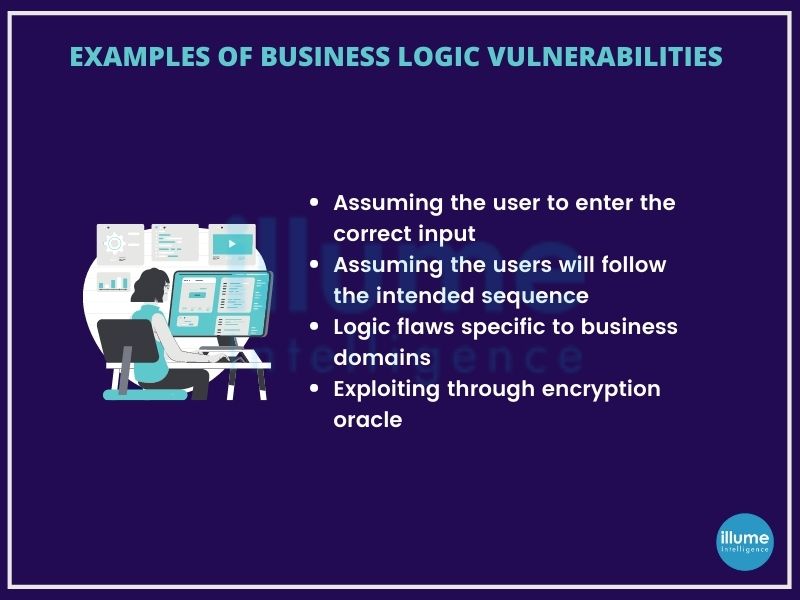
Why is Business logic testing important for your business?
A logic vulnerability is not a flaw in the coding framework, but the way it is exploited to do something unexpected. developers often focus on making the application user-friendly but are unaware of ways hackers can misuse certain functionalities from the server side as in the case of authorization issues, denial of service etc.
Using both Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST) the application security can be improved on overall compliance and risk management. Tools included in the manual vulnerabilities finding are OWASP Top 10, CWE Top 25 issues, Cross-Site Scripting (XSS), SQL injection, Fingerprinting, Content Spoofing, Cross-Site Request Forgery (CSRF), URL redirector abuse, Brute Force, etc.
According to the experts, 20% of the vulnerabilities are detected during Business Logic Testing or Application security testing, out of which 80% are of high to medium rating.
Are you looking to remove vulnerabilities of your applications that may lead to serious data breaches? Contact our experts to avail Application logic testing services.
Ensuring secure applications for your business through VAPT assessment
Vulnerability assessment and penetration testing a.k.a VAPT is a combination of Vulnerability assessment and penetration testing. This combination gives any organisation a better identification, classification and mitigation of the vulnerabilities present in the system and applications.
Vulnerability Assessment is focused to find the internal flaws present in the organisation’s system that may arise due to frequent changes made in the applications or due to the firewall default settings or other network settings. That’s the reason this needs to be regularly scanned and addressed.
Penetration testing aims at identifying the flaws in the system and exploiting them like a real-world hacker but in a controlled way, giving insight to the organisation on the vulnerabilities of their system. This testing is advised to be done at least annually for securing the system. The exposed flaws can be mitigated to strengthen the system, saving it from external cyber threats.
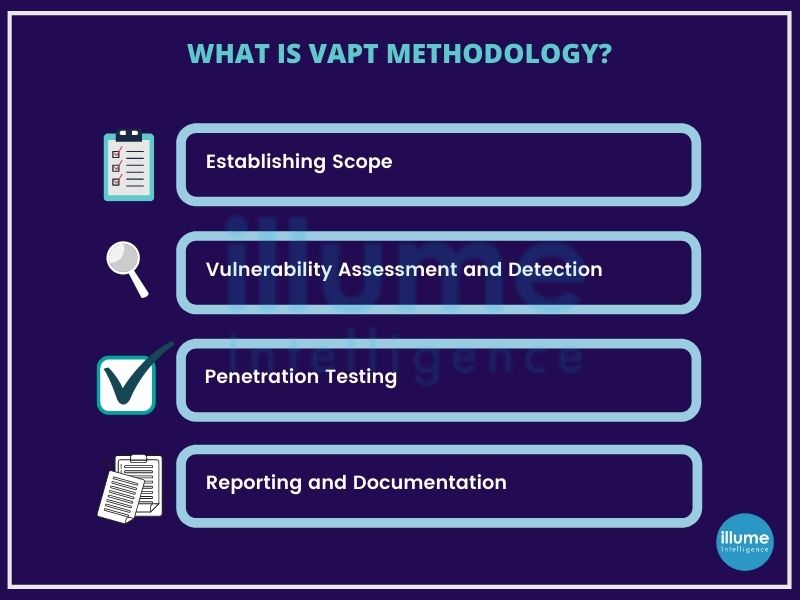
What is the necessity for Vulnerability Assessment & Penetration Testing (VAPT)?
Cyber attacks and threats are becoming nightmares for organisations these days, with thousands of websites and networks being compromised every day. Some of the reasons that make conducting Vulnerability Assessment & Penetration Testing (VAPT) in any organisation important are-
1. Keeping the data secure while in transition over the network.
2. Protecting the user data.
3. Identifying the security vulnerabilities within the system.
4. Detecting loopholes and flaws in the system.
5. Accessing the tolerance of the business against cyber attacks.
6. Implementing an effective security strategy in the organisation.
Protecting your data and resources before the attack is the idea behind conducting Vulnerability Assessment & Penetration Testing (VAPT). Every organisation is spending on security to stay away from cyber attacks.
Depending upon the requirements of the various industries, Vulnerability Assessment & Penetration Testing (VAPT) is mandatory across many industries as some compliance standards require VAPT at regular intervals. A list of such compliances are -
ISO 27002 / ISO 27001
PCI DSS – Payment Card Industry Data Security Standard
SOX – Sarbanes-Oxley Act
HIPAA – Health Insurance Portability and Accountability Act
TRAI – Telecom Regulatory Authority of India
DOT – Department of Telecommunication
CERT-In – Cyber Emergency Response Team of India
GLBA – The Gramm–Leach–Bliley Act
FISMA – The Federal Information Security Management Act
NIST – National Institute of Standards and Technology
SAS 70 – Statement on Auditing Standards
COBIT – Control Objectives for Information and Related Technology
Knowing how much vulnerable your organisation is always better than assuming the vulnerabilities, as then only one can take necessary preventive measures. If you are looking to fix your organisation's vulnerabilities we can help.
Discovering your Cybersecurity Vulnerabilities with Penetration Testing
Penetration testing also known as Pen Test across the IT Industry is the simulated cyber attack on your security system to check, how vulnerable your system is? This can be done for any web application or network.
With the increasing digitization of business operations and processes, we are more exposed to the risks of new technologies. Threat actors can easily exploit the vulnerabilities that exist within our IT infrastructure. It's not hard to imagine what all can happen once the hackers get access to the internal critical data of an organisation.
Mitigating the risk and avoiding these attacks from happening is the only way out. It is advisable to be capable of preventing, detecting, responding and recovering from such risks. No system can be 100% secure hence we need proper procedures in place to perform security assessments such as Penetration Testing.
Penetration testing helps in risk assessment, along with adhering to compliances and regulations. The organisation's reputation and security of critical data are also at stake due to these attacks, which can be saved using Penetration Testing.
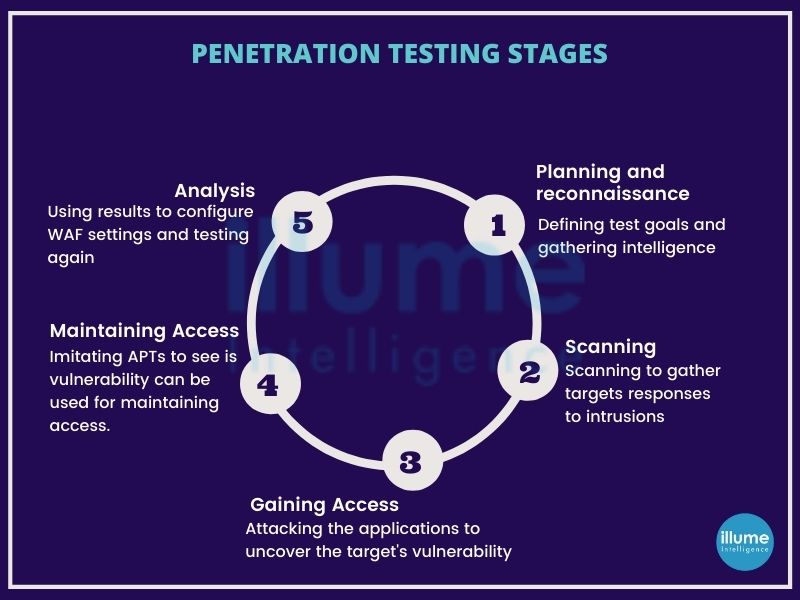
How do we implement Penetration Testing?
The type of testing depends upon the requirement of the organisation.
1. External Testing - Testing the organisational assets visible to the outside company's network, e.g. web applications, website, email and domain name servers.
2. Internal Testing - Testing from inside the corporate wherein the tester has got access to the organisational network as in case of stolen credentials.
3. Blind Testing - The tester is given limited information about the target and has to gather information from open sources.
4. Double-Blind Testing - Similar to blind testing but here in the organisation the security team is not updated about the activity. This helps in ascertaining how fast and effective the security team is in detecting the risk.
5. Targeted Testing - Tester and security person team up to keep each other updated on their movements. This helps in gaining real insights and feedback from the hacker's perspective.
Every organisation should conduct penetration testing on the regular basis especially after implementing any change in the IT infrastructure.
Contact us to safeguard your organisation from cyber threats.







